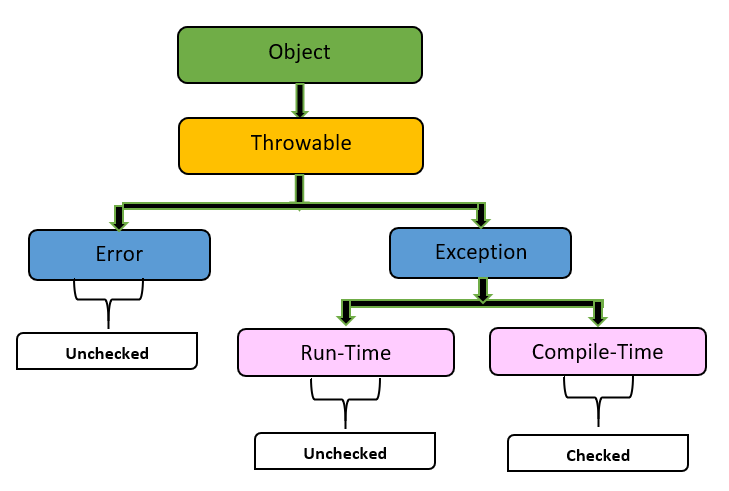
Javax net SSL SSLHandshakeException Received fatal alert: handshake_failure
Javax net SSL SSLHandshakeException Received fatal alert: handshake_failure

I'd be happy to help you with that.
The SSLHandshakeException is a common exception that occurs when there's an issue with the Secure Sockets Layer (SSL) or Transport Layer Security (TLS) protocol during the initial handshake process between a client and a server. In your case, the specific error message indicates that the server sent a "fatal alert" to the client, which causes the handshake to fail.
The "handshake_failure" alert is typically raised when a fatal error occurs, such as an incorrect or unsupported TLS version, an invalid certificate, or a mismatch between the expected and actual TLS protocol versions. This can happen when there's a misconfiguration on either the client or server side, or if one of the parties does not support the same level of security (e.g., old clients may not support newer TLS versions).
When the client receives this fatal alert, it typically closes the connection without sending any further data. In some cases, you might see additional error messages or warnings depending on the specific circumstances.
To troubleshoot this issue, you can try a few things:
Check your server's configuration: Ensure that your server is properly configured for TLS (or SSL) and that there are no issues with certificates, ciphersuites, or protocol versions. Verify client-side settings: Check the TLS settings on your client-side application to ensure they're compatible with your server's configuration. Try different TLS versions or ciphersuites: If you suspect a version or cipher suite incompatibility issue, try changing the default settings to see if it resolves the problem. Debugging tools: Use debugging tools like Wireshark or SSL/TLS debugging libraries (e.g., OpenSSL'ss_client command) to inspect and analyze the TLS handshake process.
Remember that a successful SSL/TLS handshake requires a compatible set of protocols, certificates, and ciphersuites on both the client and server sides. If you're still stuck, feel free to provide more details about your setup, and I'll do my best to help you troubleshoot the issue!
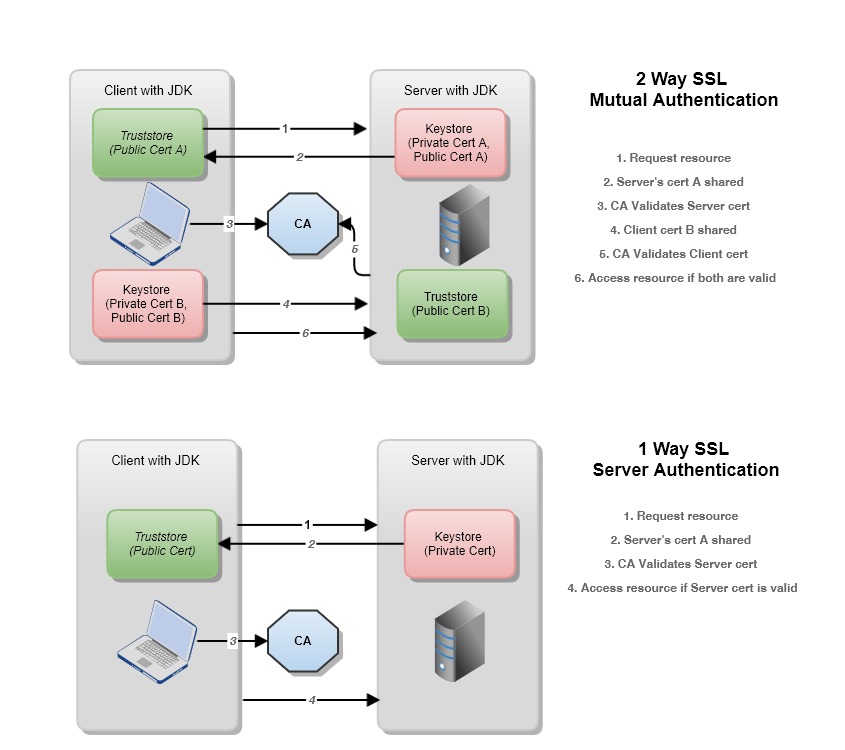
How to implement 2 way SSL in Java?

To implement two-way SSL (Transport Layer Security) in a Java-based application, you need to create digital certificates for both the server and client. This article will walk you through the steps.
Prerequisites
Java Development Kit (JDK) version 8 or higher
Step 1: Generate Server Certificate (Certificate Authority)
For a self-signed certificate, use OpenSSL to create a root certificate authority (CA):
openssl req -x509 -newkey rsa:2048 -nodes -out ca.crt -keyout ca.key -days 3650
This command generates a private key (ca.key) and a self-signed certificate (ca.crt).
Step 2: Generate Client Certificate
To create a client certificate, you need to generate a private key and a certificate signed by the root CA:
openssl req -newkey rsa:2048 -nodes -out client.key -keyout client.key
openssl x509 -req -in client.csr -signkey ca.key -out client.crt -days 3650
This command generates a private key (client.key) and a certificate signed by the root CA (client.crt).
Step 3: Create Keystore (Server-Side)
Create a keystore file for the server, which contains the server's private key and certificate:
keytool -genkeypair -alias server -keyalg RSA -keystore server.keystore
keytool -v -import -file ca.crt -alias root -storefile server.keystore
keytool -v -import -file client.crt -alias client -storefile server.keystore
Step 4: Create Truststore (Client-Side)
Create a truststore file for the client, which contains the root CA certificate:
keytool -import -file ca.crt -alias root -keystore client.truststore
Step 5: Configure Java SSL
In your Java application, configure SSL as follows:
// Create a TrustManager to validate the server's certificate
TrustManager[] trustManagers = {new X509TrustManager() {
public void checkClientTrusted(X500Principal principal, certificationPath path) {
// No need to verify the client's certificate
}
public void checkServerTrusted(X500Principal principal, certificationPath path) {
// Verify the server's certificate
}
}};
// Create an SSLContext for two-way SSL
SSLContext context = SSLContexts.create();
// Set up the socket factory for two-way SSL
context.init(trustManagers, null, new SecureRandom());
// Use the socket factory to establish a connection to the server
Socket socket = context.getSocketFactory().createSocket("server-hostname", port);
Step 6: Implement Two-Way SSL in Your Java Application
Now you're ready to implement two-way SSL in your Java application. When establishing a connection to the server, ensure that the client sends its certificate and private key to the server. The server can then verify the client's identity using the provided certificate.
That's it! You've successfully implemented two-way SSL in your Java-based application.