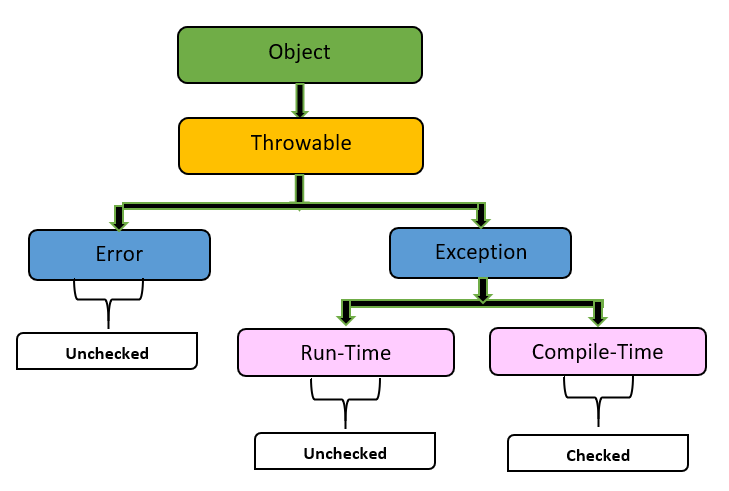
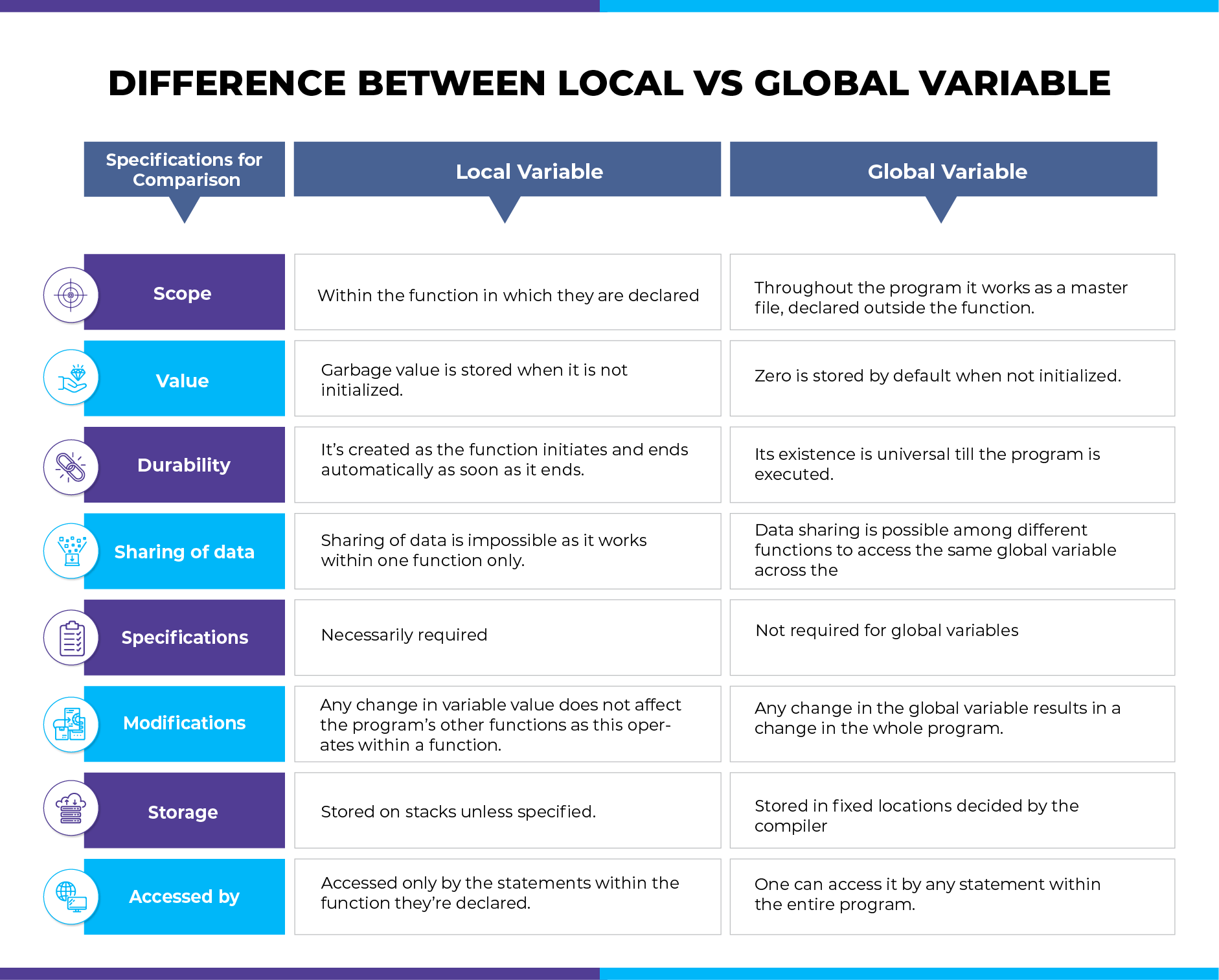
How do I encrypt in Java?
How do I encrypt in Java?
I'm glad you asked! Encrypting data in Java can be achieved using various algorithms and libraries. Here's a comprehensive guide to get you started:
Why Encrypt?
Before diving into the encryption process, it's essential to understand why encryption is crucial for protecting sensitive data. Encryption ensures that even if an attacker gains access to your data, they won't be able to read or use it without the decryption key. This is particularly important in today's digital era where data breaches and cyber attacks are common.
Java Encryption Libraries
Java offers several libraries for encrypting data, including:
Java Cryptography Architecture (JCA): JCA provides a framework for developing cryptographic applications. It includes providers for various encryption algorithms. Apache Commons Codec: This library provides utilities for encoding and decoding text, as well as encryption and decryption capabilities. Bouncy Castle: Bouncy Castle is a popular open-source Java library that provides a wide range of cryptography-related functionality.Encryption Algorithms
Java supports several encryption algorithms, including:
AES (Advanced Encryption Standard): A symmetric-key block cipher used for encrypting large amounts of data. RSA (Rivest-Shamir-Adleman): An asymmetric encryption algorithm often used for key exchange and digital signatures. DES (Data Encryption Standard): A legacy symmetric-key block cipher that's still widely used. Blowfish: A symmetric-key block cipher known for its high speed and security.How to Encrypt in Java
Here's a step-by-step guide on how to encrypt data using Java:
Choose an encryption algorithm: Select the algorithm you want to use, such as AES or RSA. Generate keys: Create keys for encryption (and decryption if needed). For example, you can generate a random key for AES encryption. Encrypt the data: Use the chosen algorithm and generated keys to encrypt your sensitive data. Store encrypted data: Store the encrypted data securely, such as in a database or file.Example: AES Encryption
Here's an example of how to use the JCA and Apache Commons Codec libraries for AES encryption:
import org.apache.commons.codec.binary.AESCipher;
public class AesEncryptionExample {
public static void main(String[] args) throws Exception {
// Generate a random key (128 bits)
byte[] key = new byte[16];
SecureRandom rand = SecureRandom.getInstance();
rand.nextBytes(key);
// Create an AES cipher
AESCipher aes = new AESCipher(key, 0); // Use the first 16 bytes of the key
// Encrypt some data
String originalText = "Hello, World!";
byte[] encryptedData = aes.encrypt(originalText.getBytes());
// Decrypt the data
String decryptedText = new String(aes.decrypt(encryptedData));
System.out.println("Original text: " + originalText);
System.out.println("Encrypted text: " + bytesToHex(encryptedData));
System.out.println("Decrypted text: " + decryptedText);
}
private static String bytesToHex(byte[] b) {
StringBuffer sb = new StringBuffer();
for (int i = 0; i < b.length; i++) {
String ip;
ip = Integer.toHexString(0x100 + ((b[i] & 0xff)));
if(ip.length() == 4)
sb.append(ip);
else
sb.append("0").append(ip);
}
return sb.toString();
}
}
In this example, we generate a random key for AES encryption using the SecureRandom class. We then create an AES cipher instance and use it to encrypt some sample data. Finally, we decrypt the encrypted data and print the results.
Conclusion
Java provides robust support for encryption through various libraries and algorithms. By choosing the right library and algorithm, you can effectively protect sensitive data in your Java applications. Remember to always use secure key generation and handling practices when working with encryption.
java cryptography architecture
The Java Cryptography Architecture (JCA) is a framework that provides a set of APIs for developing secure applications using cryptographic algorithms. The JCA is part of the Java Standard Edition (SE) and provides a foundation for building robust, secure, and reliable software applications.
The JCA provides several key components that enable developers to implement cryptography in their applications:
Cryptographic Algorithm Implementations: The JCA includes implementations of popular cryptographic algorithms such as symmetric encryption (e.g., DES, AES), asymmetric encryption (e.g., RSA), hashing (e.g., SHA-256), and digital signatures. Key Generation and Management: The JCA provides classes for generating and managing keys, including key pair generation, key wrapping, and key unwrapping. Cryptographic Utilities: The JCA includes a set of utility classes that provide functionality for tasks such as data encryption, decryption, signature generation, and verification.The JCA is designed to be modular and extensible, allowing developers to easily integrate new cryptographic algorithms or implement custom cryptographic protocols. This modularity also makes it easier to maintain and update the framework over time.
Some key benefits of using the JCA include:
Improved Security: By leveraging standardized cryptographic algorithms and best practices for cryptography implementation, the JCA helps ensure that applications are secure and robust. Simplified Development: The JCA provides a set of reusable APIs and utilities that simplify the development process, reducing the need to write custom cryptographic code. Interoperability: The JCA is designed to work with other Java frameworks and libraries, making it easier to integrate cryptography into larger applications.In addition to its core components, the JCA also includes several tools and utilities for testing and debugging cryptographic implementations. These include classes for generating test data, simulating attacks, and validating cryptographic implementations.
Overall, the Java Cryptography Architecture (JCA) is an essential framework for developing secure and robust software applications in Java. Its modular design, extensibility, and standardization make it a valuable resource for developers looking to incorporate cryptography into their projects.
Here's a high-level overview of how the JCA works:
Key Generation: The JCA provides classes for generating public-private key pairs using algorithms such as RSA. Data Encryption: Developers can use the JCA's encryption APIs to encrypt data using symmetric or asymmetric algorithms, such as AES or RSA. Signature Generation: The JCA includes utilities for generating digital signatures using algorithms like SHA-256 and RSA. Validation: After signature generation, developers can use the JCA's validation APIs to verify the authenticity of signed data.The Java Cryptography Architecture (JCA) is a powerful tool for building secure software applications in Java. By providing a standardized set of cryptographic APIs and utilities, the JCA simplifies the development process while ensuring that applications are robust and secure.