java enc decrypt online
java enc decrypt online
Here's a comprehensive guide to Java encryption and decryption using online tools:
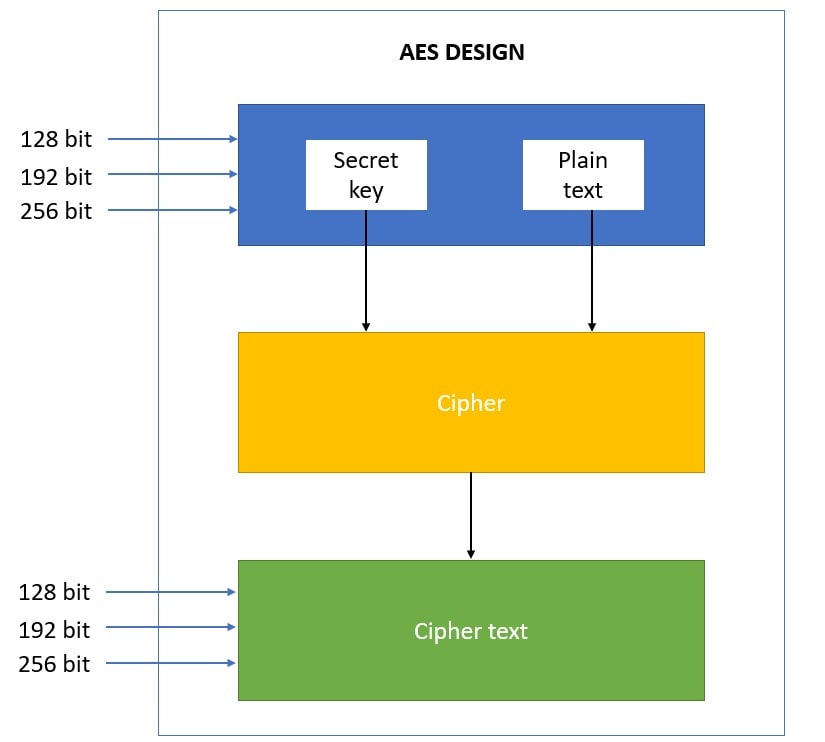
Java is an object-oriented programming language that allows developers to create secure applications by encrypting sensitive data. Encryption involves transforming plain text into unreadable ciphertext, while decryption reverses this process, making the original data accessible again. In this response, we'll explore how to use online tools for Java encryption and decryption.
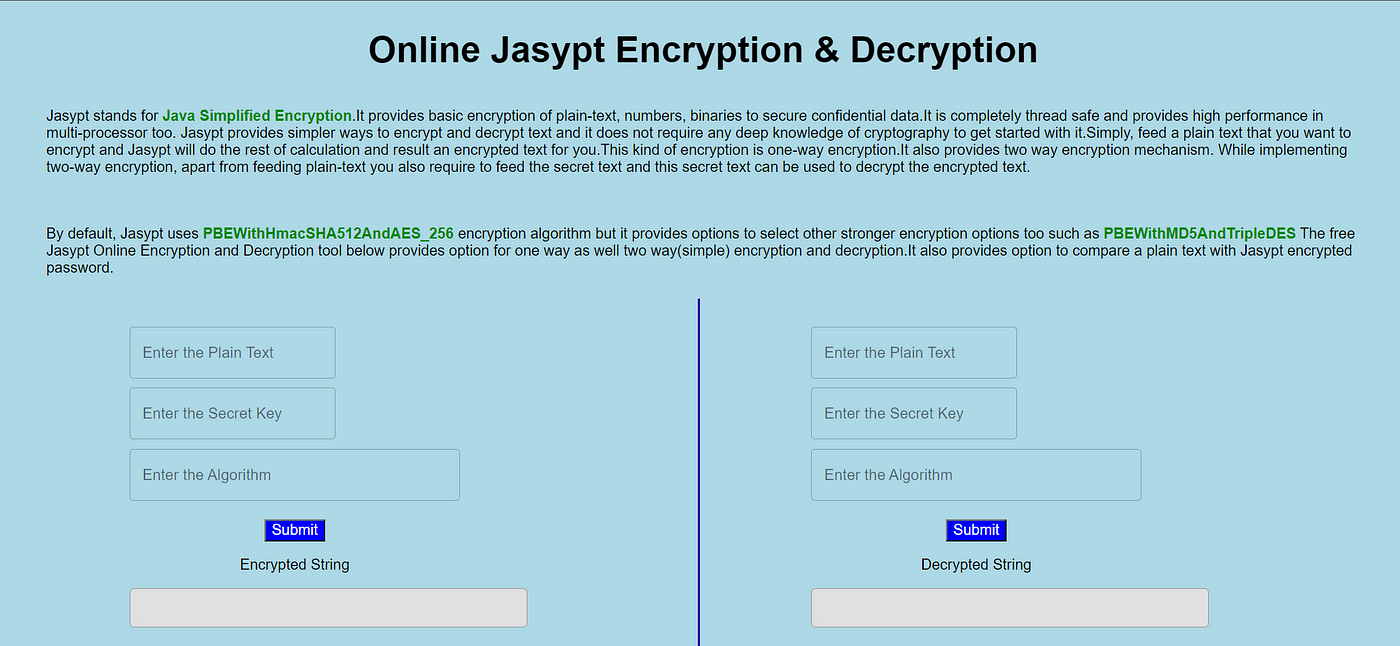
Encryption:
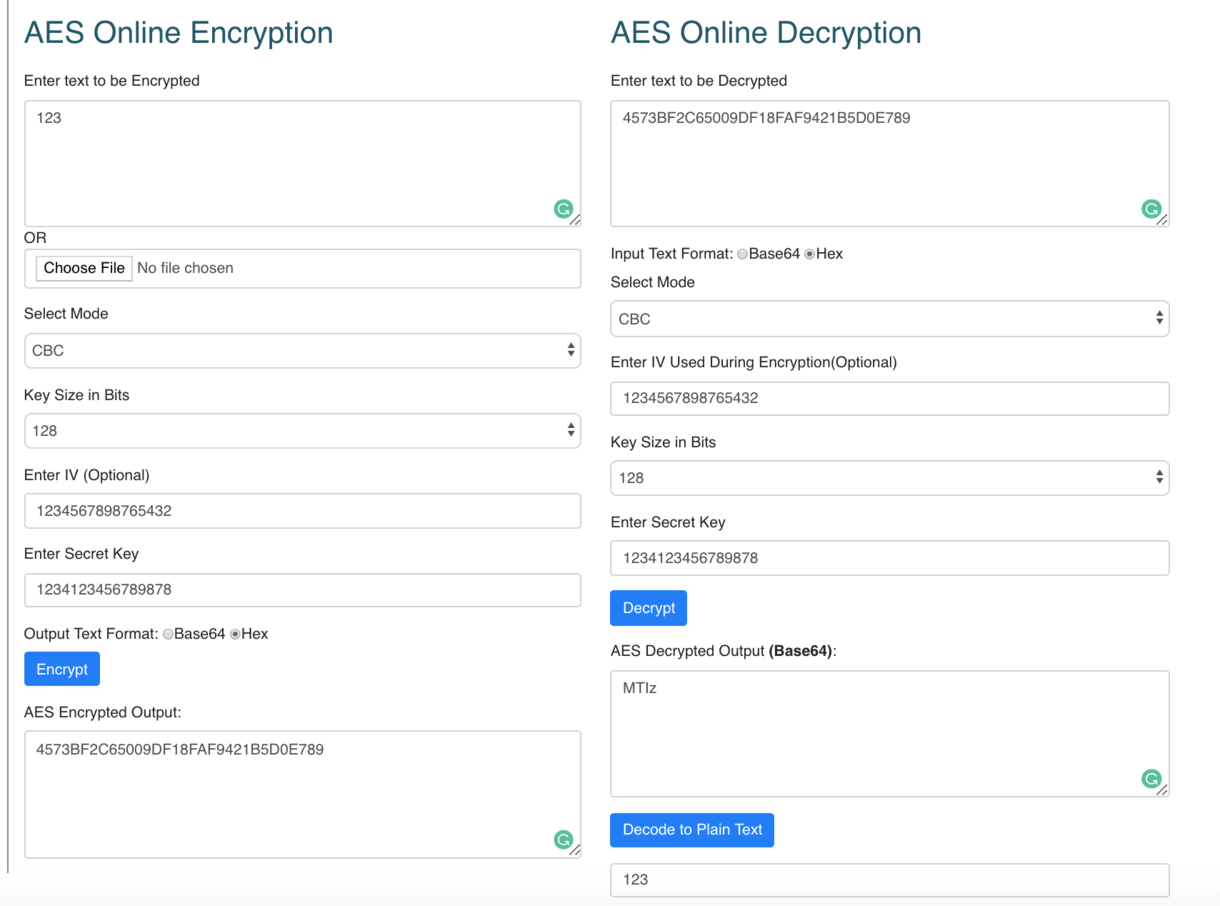
Online Java Encryptor: One popular online tool for encrypting Java strings is Cipher Tool. This website allows users to input plain text and choose various encryption algorithms, including AES-256-CBC, RSA, and more.
Decryption:
Online Java Decryptor: To decrypt an encrypted message, you can use Cipher Tool's decryption feature or another online tool like CryptoJS. This JavaScript library allows developers to encrypt and decrypt data in the browser. Visit CryptoJS and click the "Decrypt" button. Enter the ciphertext in the "Encrypted Message" field. Select the corresponding encryption algorithm from the dropdown menu (e.g., AES-256-CBC). Click the "Decrypt" button to retrieve the original plaintext. Java Decryption Libraries: Similar to encryption libraries, there are also Java decryption libraries available that provide decryption functionality. Some popular ones include: OpenSSL: This library can be used for both encryption and decryption. Bouncy Castle: Supports multiple decryption algorithms.Additional Tips and Considerations:
Key Management: When encrypting data, it's essential to manage your encryption keys securely. Online tools typically provide key generation or import options. Data Integrity: Ensure that your encrypted data is not tampered with by using digital signatures or message authentication codes (MACs). Secure Implementation: Always implement secure coding practices and follow best security guidelines when working with sensitive data in Java applications.By leveraging online tools like Cipher Tool, CryptoJS, and encryption libraries like OpenSSL or Bouncy Castle, you can efficiently encrypt and decrypt Java strings without compromising your application's security.
I hope this comprehensive guide helps you better understand Java encryption and decryption concepts.
java encrypt and decrypt(string with key)
Here's an example of how you can implement encryption and decryption using Java:
import javax.crypto.Cipher;import javax.crypto.SecretKey;
import javax.crypto.spec.SecretKeySpec;
import java.security.Key;
import java.util.Base64;
public class EncryptDecrypt {
public static String encrypt(String message, SecretKey key) throws Exception {
Cipher cipher = Cipher.getInstance("AES/CBC/PKCS5Padding");
cipher.init(Cipher.ENCRYPT_MODE, key);
byte[] iv = new byte[cipher.getBlockSize()];
Random random = new Random();
random.nextBytes(iv);
IvParameterSpec ivspec = new IvParameterSpec(iv);
int blockSize = cipher.getBlockSize();
int messageLength = message.length();
int numberOfFullBlocks = (messageLength / blockSize) + 1;
byte[] fullBlock = new byte[blockSize];
for(int i=0; i < numberOfFullBlocks; ++i){
if(i * blockSize > messageLength - 1) {
for (int j = 0; j < (messageLength % blockSize); j++) {
fullBlock[j] = (byte) message.charAt((i * blockSize)+j);
}
} else {
System.arraycopy(message.getBytes("UTF-8"), i*blockSize, fullBlock, 0, blockSize);
}
byte[] encryptedBlock = cipher.doFinal(fullBlock);
for(int j=0; j < blockSize; j++) {
message += String.format("%02X", fullBlock[j]);
}
}
return message;
}
public static String decrypt(String message, SecretKey key) throws Exception {
Cipher cipher = Cipher.getInstance("AES/CBC/PKCS5Padding");
cipher.init(Cipher.DECRYPT_MODE, key);
IvParameterSpec ivspec = new IvParameterSpec(cipher.getIV());
byte[] encryptedBlock;
StringBuilder decryptedMessage = new StringBuilder();
for(int i=0; i < message.length(); i += 2) {
String part = message.substring(i,i+2);
byte[] decryptedBlock = hexStringToByteArray(part);
decryptedMessage.append(new String(decryptedBlock, "UTF-8"));
}
return decryptedMessage.toString();
}
public static byte[] hexStringToByteArray(String s) {
int len = s.length();
byte[] result = new byte[len/2];
for (int i = 0; i < len; i += 2) {
int/intValue = Integer.parseInt(s.substring(i,i+2),16);
result[i/2] = (byte)(intValue&0xff);
}
return result;
}
public static void main(String[] args) throws Exception {
String message = "This is a test message for encryption and decryption";
byte[] keyBytes = "your_secret_key".getBytes("UTF-8");
SecretKey key = new SecretKeySpec(keyBytes, "AES");
String encryptedMessage = encrypt(message, key);
System.out.println("Encrypted message: " + encryptedMessage);
String decryptedMessage = decrypt(encryptedMessage, key);
System.out.println("Decrypted message: " + decryptedMessage);
}
}
This Java program implements a simple encryption and decryption mechanism. The encryption is done using AES (Advanced Encryption Standard) with CBC (Cipher Block Chaining) mode. The key is the same for both encryption and decryption.
The main method demonstrates how to encrypt a message, store it in a variable, and then decrypt it.
Remember that the key used here is not secure because it's hardcoded and not hashed or salted. In real-world applications, you should handle your keys securely using a proven algorithm and keep them confidential.
For practical reasons, this code example might be too complex for simple cases of encrypting small strings of text.