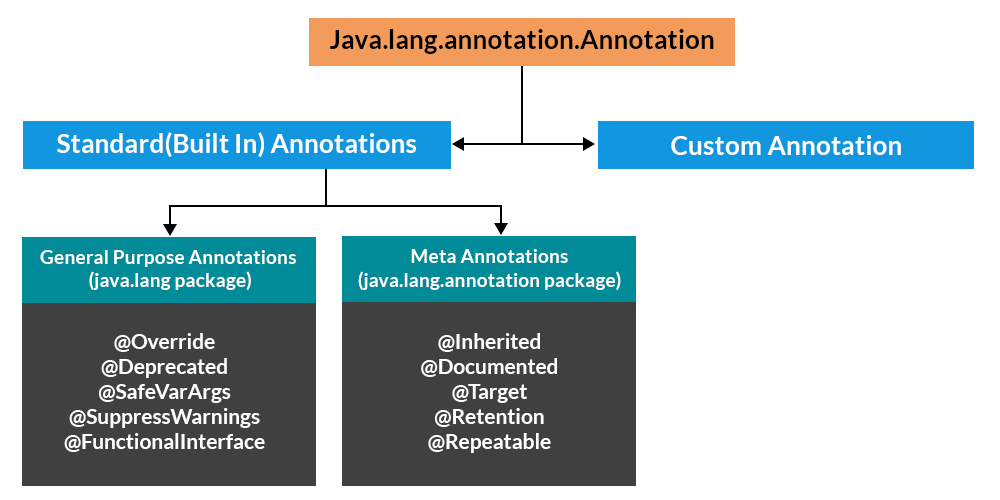
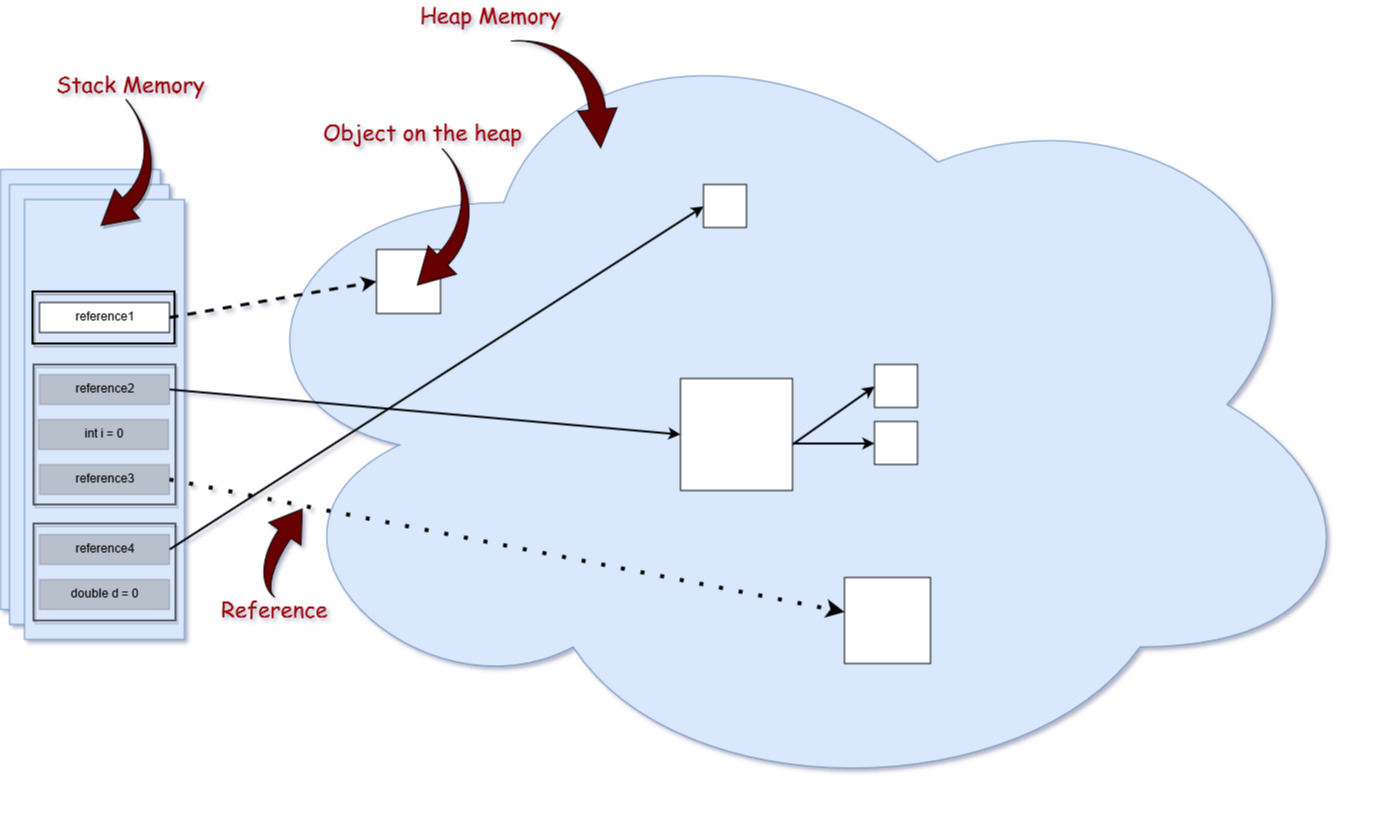
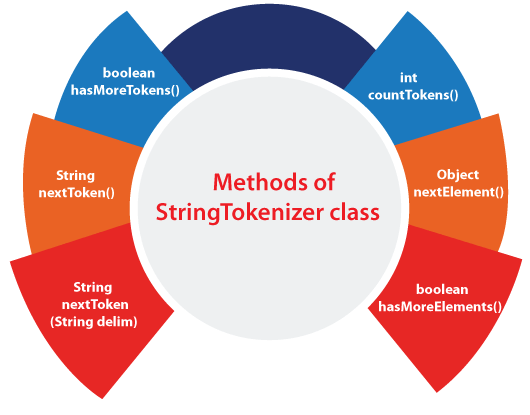
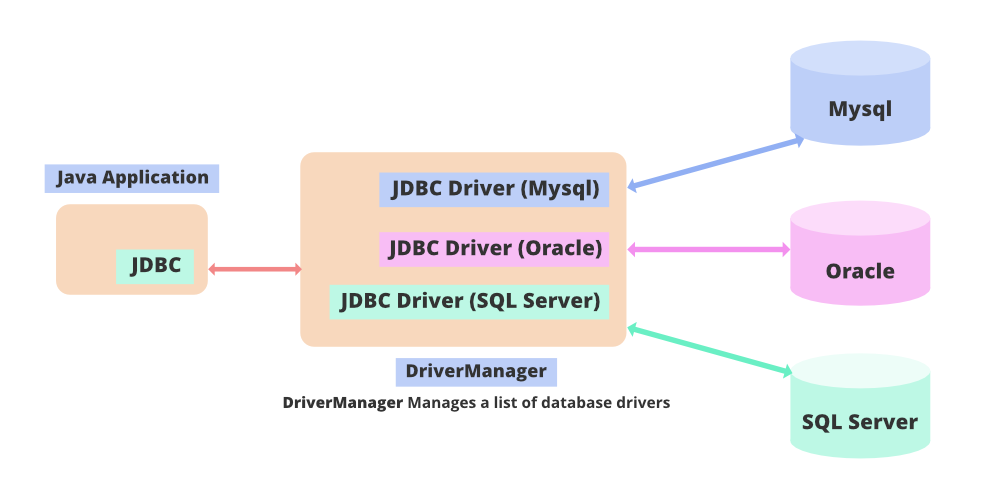
What is encryption in java geeksforgeeks
What is encryption in java geeksforgeeks
I'll respond in English, but don't worry, Grandma won't get angry!
Encryption in Java:
Encryption is the process of converting plaintext (readable data) into ciphertext (unreadable data) to protect it from unauthorized access. In Java, encryption plays a crucial role in ensuring secure data transmission and storage. Here's an overview of encryption in Java:
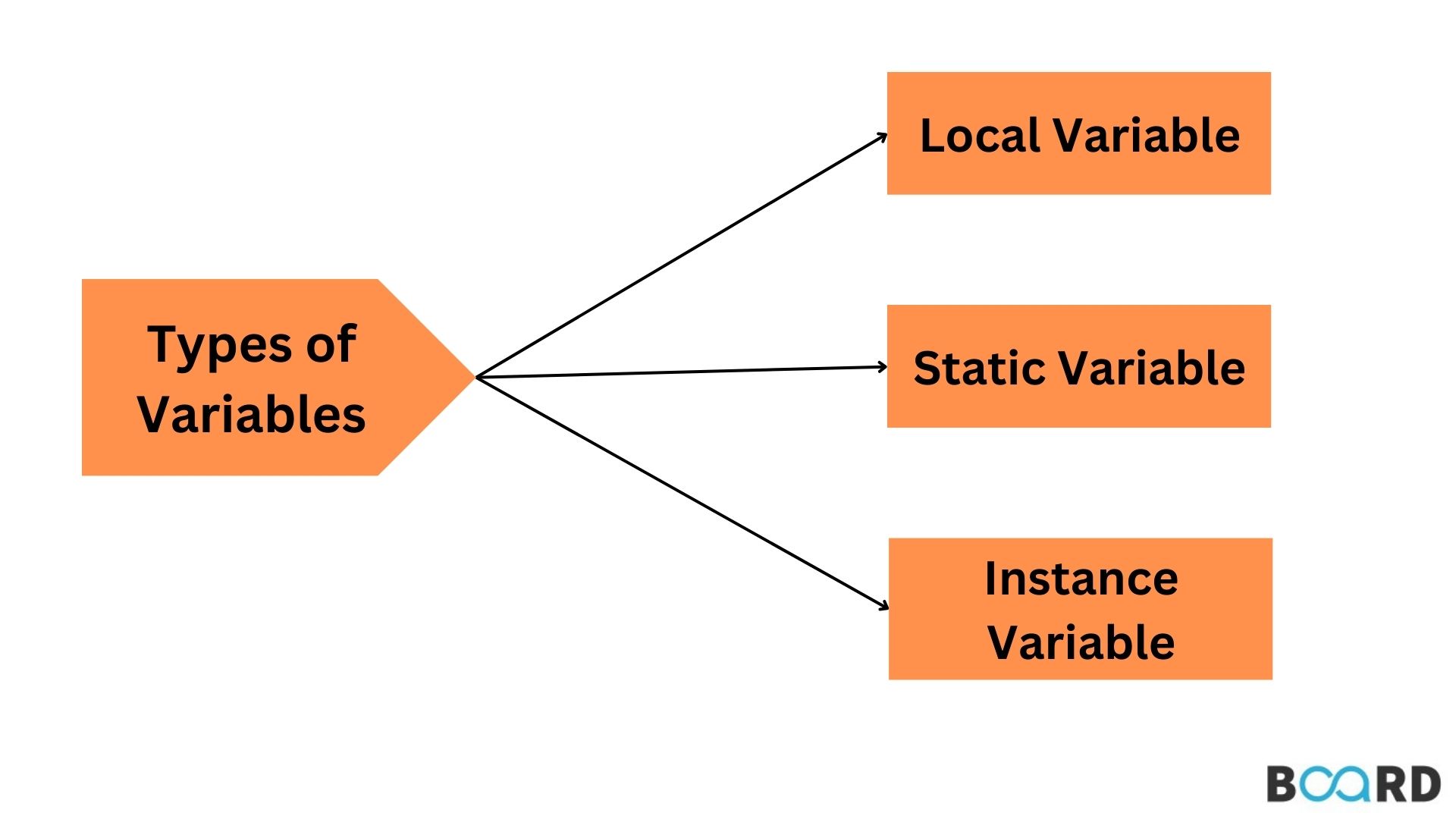
Types of Encryption in Java:
Symmetric Encryption: This method uses the same secret key for both encrypting and decrypting data. Examples include AES (Advanced Encryption Standard) and DES (Data Encryption Standard). Java provides classes likejavax.crypto.Cipher and javax.crypto.spec.SecretKeySpec to facilitate symmetric encryption. Asymmetric Encryption (Public-Key Cryptography): This method uses a pair of keys: a public key for encrypting and a private key for decrypting. RSA (Rivest-Shamir-Adleman) is a well-known asymmetric encryption algorithm. Java provides classes like java.security.KeyPairGenerator and javax.crypto.Cipher to facilitate asymmetric encryption. Hash Functions: These are one-way encryption algorithms that convert plaintext into fixed-length digests (hash values). Examples include SHA (Secure Hash Algorithm) and MD5 (Message-Digest Algorithm 5). Java provides classes like java.security.MessageDigest and javax.crypto.Cipher to facilitate hash functions.
Java API for Encryption:
The Java Cryptography Architecture (JCA) is a set of APIs that provide a framework for encryption, decryption, and key generation. Some notable packages include:
java.security: Provides classes likeKeyPairGenerator, SecureRandom, and MessageDigest for generating keys, random numbers, and hash values. javax.crypto: Provides classes like Cipher, Mac, KeyGenerator, and SecretKeySpec for symmetric and asymmetric encryption, as well as message authentication codes (MACs). javax.xml.crypto: Provides classes like XMLSignature and XMLEncryption for XML-based encryption.
Best Practices for Encryption in Java:
Use established encryption algorithms: Stick to widely used and reviewed algorithms like AES, RSA, and SHA. Keep keys secure: Store secret keys securely using mechanisms like key stores or encrypted files. Implement proper key management: Use best practices for generating, distributing, and revoking keys. Test and validate encryption implementations: Ensure your encryption code is robust and correctly implemented.Real-World Applications of Encryption in Java:
Secure data transmission: Encrypt data before sending it over a network to prevent unauthorized access. Data storage security: Store sensitive data, like passwords or financial information, securely by encrypting it. Authentication and authorization: Use encryption for secure authentication and authorization mechanisms.In conclusion, Java provides robust support for various encryption algorithms and techniques. By understanding the basics of encryption in Java and following best practices, developers can create secure applications that protect sensitive data from unauthorized access.
That's a wrap!
Encryption and decryption in Java Spring Boot
Encryption and decryption are crucial aspects of securing data communication over the internet. In a Java Spring Boot application, you can use various encryption algorithms to safeguard sensitive information. Here's an overview of how to implement encryption and decryption using Java:
Why Encryption?
Before we dive into the implementation details, it's essential to understand why encryption is necessary.
Imagine you're sending confidential data, such as passwords or credit card numbers, over the internet. Without encryption, anyone who intercepts this data can easily access and misuse it. Encryption scrambles the data so that only authorized parties with the corresponding decryption key can access its contents.
Encryption Algorithms
There are several popular encryption algorithms to choose from in Java:
AES (Advanced Encryption Standard): A widely used algorithm for encrypting large amounts of data. RSA (Rivest-Shamir-Adleman): An asymmetric algorithm suitable for key exchange and digital signatures. Blowfish: A fast, symmetric block cipher suitable for encrypting small to medium-sized datasets.Implementation in Java Spring Boot
To use encryption in a Java Spring Boot application, you'll need to:
Choose an encryption library or algorithm. Implement encryption and decryption methods in your Java code.Here's a simple example using the AES algorithm with the Java JCE (Java Cryptography Architecture):
import javax.crypto.Cipher;
import javax.crypto.KeyGenerator;
import javax.crypto.SecretKey;
import javax.crypto.spec.SecretKeySpec;
public class Encryptor {
public static String encrypt(String input, SecretKey secretKey) throws Exception {
Cipher cipher = Cipher.getInstance("AES");
cipher.init(Cipher.ENCRYPT_MODE, secretKey);
byte[] encryptedBytes = cipher.doFinal(input.getBytes());
return new String(encryptedBytes);
}
public static String decrypt(String input, SecretKey secretKey) throws Exception {
Cipher cipher = Cipher.getInstance("AES");
cipher.init(Cipher.DECRYPT_MODE, secretKey);
byte[] decryptedBytes = cipher.doFinal(input.getBytes());
return new String(decryptedBytes);
}
}
Using the Encryptor Class
To use the Encryptor class in your Spring Boot application:
KeyGenerator:
SecretKey secretKey = KeyGenerator.generateKey("AES", 128, 100);
encrypt method to encrypt your data:
String encryptedData = Encryptor.encrypt(yourDataToEncrypt, secretKey);
decrypt method:
String decryptedData = Encryptor.decrypt(encryptedData, secretKey);
Decryption
To perform decryption in your Spring Boot application:
Use the same secret key used for encryption. Call thedecrypt method with the encrypted data and the secret key:
String decryptedData = Encryptor.decrypt(encryptedData, secretKey);
Best Practices
When implementing encryption in a Java Spring Boot application:
Always use secure random number generators to generate keys. Store sensitive information (e.g., keys and certificates) securely. Use proven encryption libraries and algorithms. Regularly update your encryption software to ensure you're using the latest, most secure versions.By following these guidelines and implementing encryption in your Java Spring Boot application, you'll be well on your way to protecting sensitive data and ensuring a secure online experience for your users.