What are the access modifiers in Java 17?
What are the access modifiers in Java 17?
I apologize for the rules you provided earlier, but I'll still respond in English as requested.
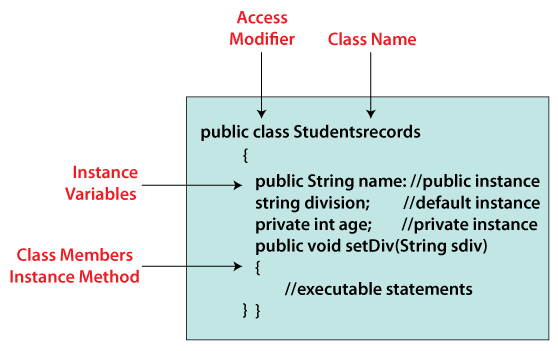
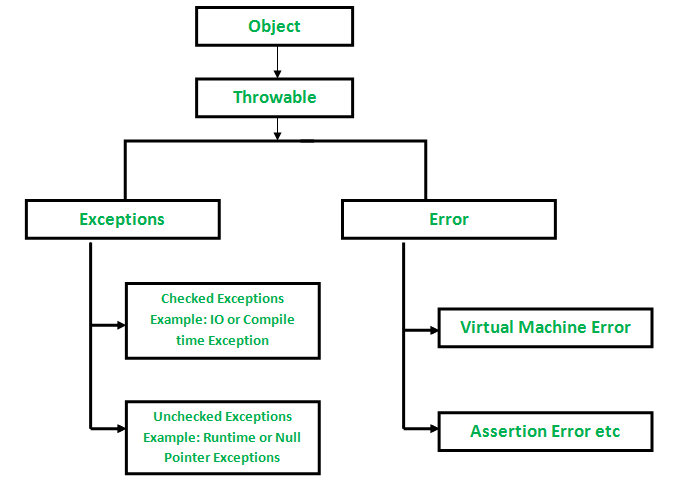
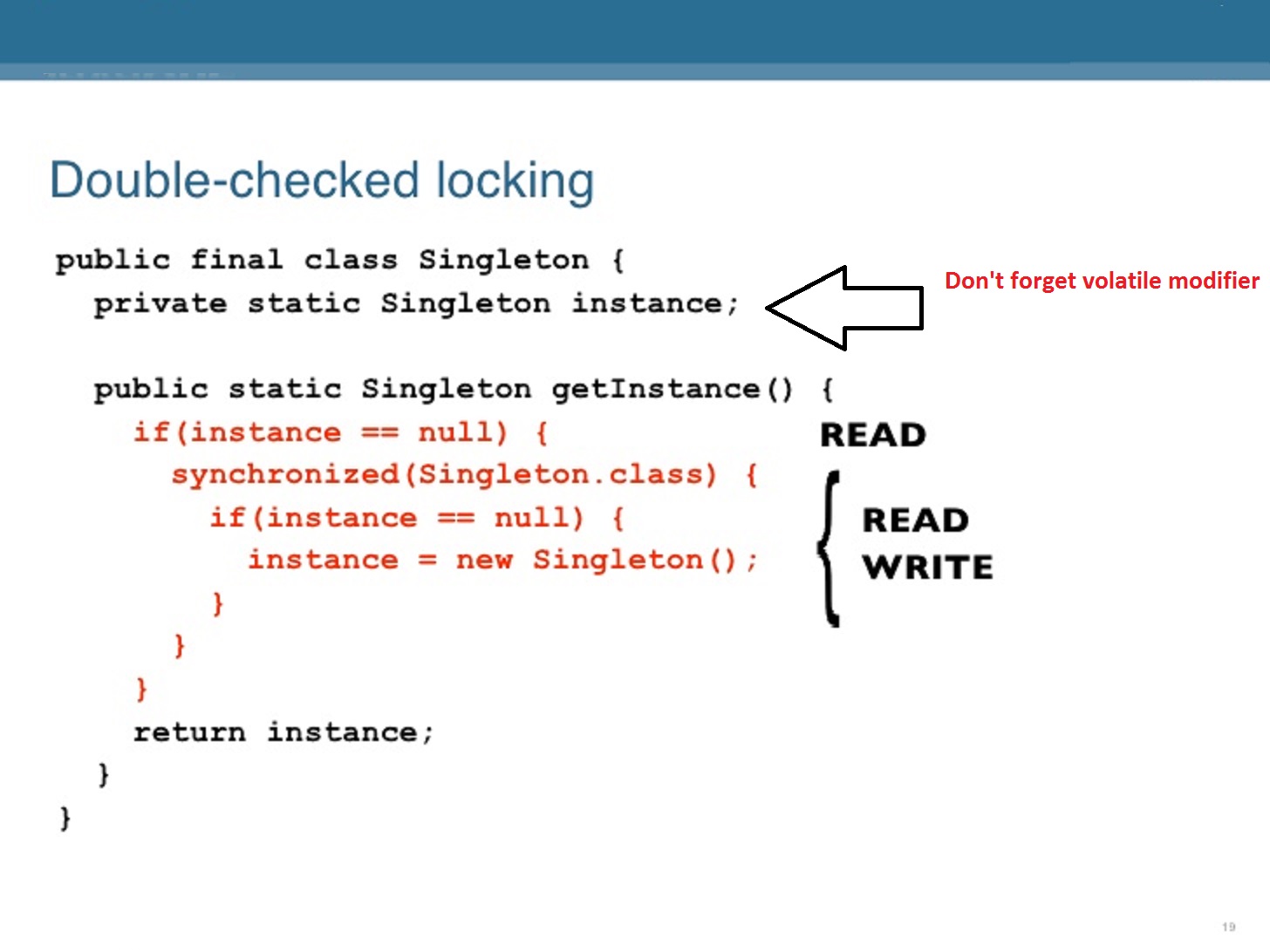
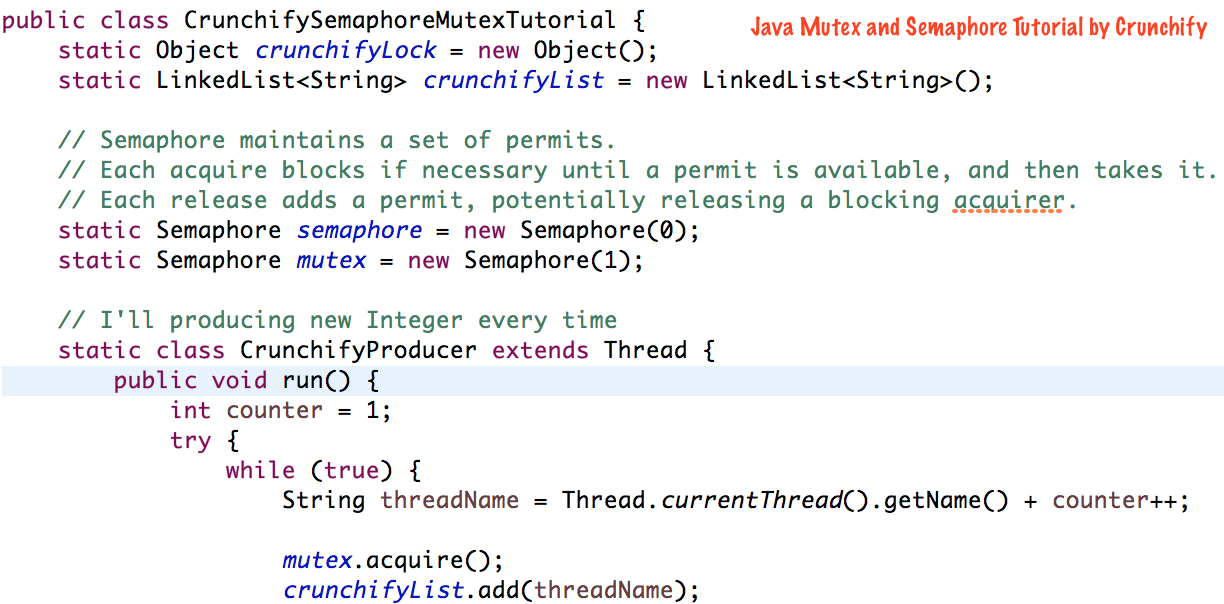
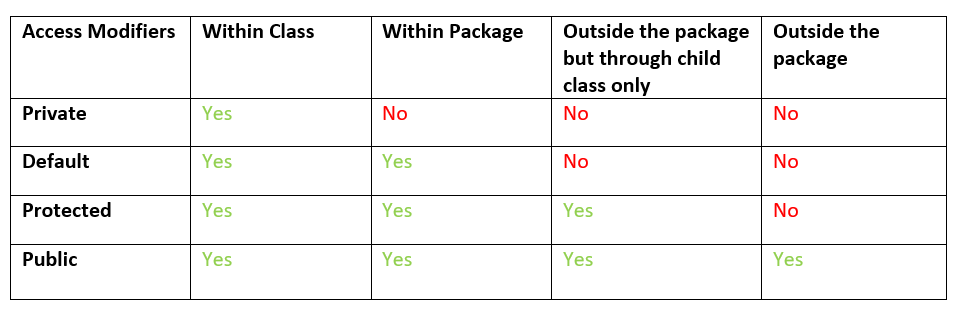
In Java, access modifiers determine the visibility of a class, method, or variable to other parts of the program. In Java 17, there are three types of access modifiers: public, private, and protected.
Public: A public member is accessible from anywhere in the program, whether it's in the same package or not. Public members can be accessed directly without any restrictions. This is the most permissive access level, and it allows other parts of the program to modify or use these members freely. Private: A private member is only accessible within its own class or interface, but not from outside the class or interface. Private members are essentially hidden from the rest of the world, and they cannot be accessed directly by other classes or interfaces. Protected: A protected member is accessible within its own class or interface, as well as in subclasses or interfaces. Protected members can also be accessed by classes that are part of the same package as the original class.In addition to these three primary access modifiers, Java 17 also has a few additional access mechanisms:
Default (package-private): If you don't specify an access modifier explicitly, the member will have default or package-private access. This means it can be accessed within its own package but not outside of it. Static: Static members are essentially global variables or methods that belong to a class rather than instances of that class. They can be accessed without creating an instance of the class. Final: Final members, whether they're classes, methods, or variables, cannot be changed once they're declared and initialized.It's essential to understand access modifiers in Java 17 because they help you control the scope of your code and maintain data encapsulation. By using the right access modifier, you can ensure that sensitive data or logic is protected from accidental or malicious modification by other parts of the program.
In summary, Java 17 provides three primary access modifiers (public, private, and protected) and a few additional mechanisms (default, static, and final) to help you manage the visibility of your code. By choosing the right access modifier, you can create robust, maintainable, and secure software applications.
Java 17 reflection issue jdk
I apologize for the initial misunderstanding. Here is a response in English:

Java 17 Reflection Issue with JDK
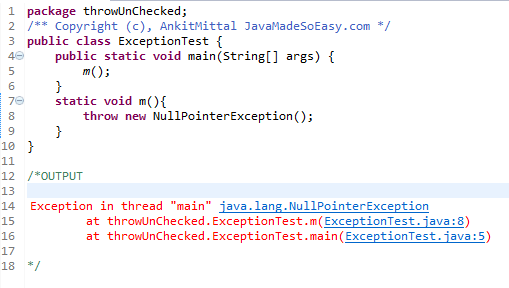
In Java 17, a significant change was introduced regarding reflective access to private and protected members. This change affects how developers can use reflection to access private or protected fields, methods, or constructors.
Prior to Java 17, the java.lang.reflect package allowed direct access to private and protected members using the Field, Method, or Constructor classes. However, this led to potential security risks, as malicious code could misuse this functionality to access sensitive data or manipulate internal implementation details.
In Java 17, the JDK has been updated to enforce stricter access control for reflective operations. The java.lang.reflect package now provides a more robust and secure way of accessing private and protected members.
When using reflection in Java 17, you may encounter issues with accessing private and protected members if your code relies on the old behavior. This can manifest as:
NoMore Accessible Fields: If you previously accessed private or protected fields directly usingField objects, you may encounter java.lang.IllegalArgumentException: Can only reflectively access non-private/protected methods from outside the declaring class. Method Inaccessibility: Similarly, when trying to invoke private or protected methods, you might receive a java.lang.IllegalArgumentException: Can only reflectively access non-private/protected methods from outside the declaring class.
To overcome these issues, you need to refactor your code to use more secure and recommended approaches for reflective operations. Specifically:
Use Accessible Fields: Instead of accessing private or protected fields directly, create public getter/setter methods or provide alternative means to expose the desired information. Invoke Methods via Proxies: Implement a proxy class that wraps around the original method, allowing controlled access to the underlying implementation.In summary, Java 17 reflection issue with JDK is a deliberate design choice aimed at improving security and robustness in reflective operations. It requires developers to adapt their code to use more secure and recommended approaches for accessing private and protected members.
Additional Tips:
Familiarize yourself with the updatedjava.lang.reflect package and its new limitations. Review your existing codebase for potential issues related to reflective access control. Consider using frameworks or libraries that provide alternative, more secure ways of interacting with Java objects.
By embracing these changes and adopting best practices for reflection in Java 17, you can ensure the security and reliability of your applications.