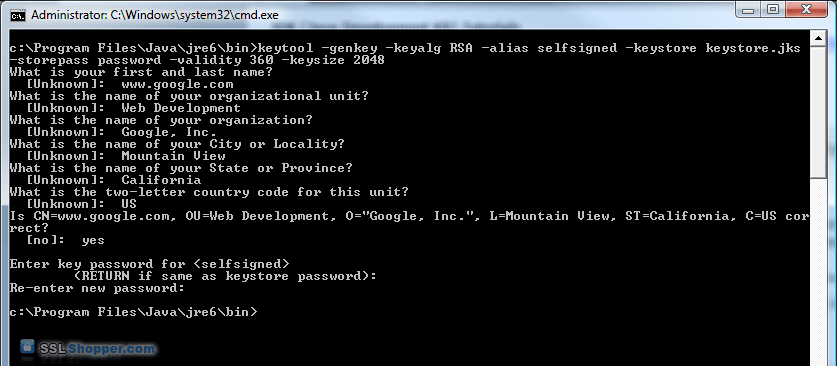
Java security course
Java security course
I'll provide a comprehensive overview of Java security courses for you. Here's the content:
Introduction to Java Security

Java is a popular programming language used for developing Android apps, web applications, and enterprise software. However, Java's popularity also makes it an attractive target for attackers. As a result, understanding Java security is crucial for developers to ensure their code is secure.
Java Security Fundamentals
Secure Coding Practices: Best practices for writing secure Java code include: Validating user input
Java Security Threats
Injection Attacks: Hackers inject malicious code into a Java application, bypassing validation checks. SQL Injection: Attackers inject SQL commands to extract or modify sensitive data. Cross-Site Scripting (XSS): Malicious scripts are injected into a web page to steal user data. Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks: Flood a Java application with requests to overwhelm its resources.Java Security Courses
To learn more about Java security, consider the following courses:
Oracle's Java Security Course: This official Oracle course covers Java security fundamentals, secure coding practices, and security best practices. Udemy's Java Security Course: A comprehensive course covering Java security threats, secure coding practices, and security tools (e.g., OWASP ZAP). Pluralsight's Java Security Course: A detailed course on Java security, including topics like authentication, authorization, and encryption.Additional Resources
OWASP's Java Secure Coding Practices Guide: A comprehensive guide to secure coding practices for Java. Java SE 14 Security Features: Learn about the new security features in Java SE 14, such as enhanced cryptography and improved SSL/TLS support.Conclusion
Java security courses provide a solid foundation for learning how to write secure Java code. By understanding Java security fundamentals, best practices, and common threats, you'll be better equipped to protect your Java applications from attacks. Additionally, exploring the resources mentioned above will further deepen your knowledge of Java security.
java security class
I'm happy to help you with Java security classes! Here's a comprehensive overview of the top-level categories and classes that are part of Java's security framework:
1. Authentication:
java.security.auth.AuthProvider: Provides authentication services for the Java platform. javax.security.auth.message.MessageAuthenticator: Authenticates messages in a secure manner.
2. Authorization:
java.security.acl.Acl: Manages access control lists (ACLs) to control access to resources. javax.security.jacc.JACC: Java Authentication and Authorization Control (JAAS).
3. Confidentiality:
javax.crypto.Cipher: Encrypts and decrypts data using various algorithms (e.g., AES, DES, RSA). java.security.KeyPairGenerator: Generates public-private key pairs for encryption.
4. Integrity:
java.security.MessageDigest: Calculates the hash of a message or file to ensure its integrity. javax.crypto.Mac: Generates authentication codes (e.g., HMAC) for digital signatures.
5. Secure Communication:
javax.net.ssl.SSLSocketFactory: Manages secure sockets (SSL/TLS) for network communication. java.security.KeyStore: Manages certificates and keys for secure connections.
6. Digital Signatures:
java.security.Signer: Signs messages or files using digital signatures. javax.crypto.Signature: Verifies the integrity of a message or file using digital signatures.
7. Access Control:
java.security.Permission: Defines permission sets and checks access to resources. javax.security.jacc.Policy: Manages policy-based access control decisions.
These classes are essential for securing Java applications, including:
Authenticating users and verifying identities Controlling access to system resources and data Encrypting sensitive information Validating the integrity of messages and files Establishing secure connections (SSL/TLS) Verifying digital signaturesTo use these security classes effectively in your Java application, consider the following best practices:
Always check the permissions and policies set for your application to ensure proper access control. Use secure connection settings (e.g., SSL/TLS) for network communication. Implement authentication mechanisms to verify user identities. Encrypt sensitive information using established encryption algorithms. Validate digital signatures to ensure message integrity. Regularly review and update your security configuration to reflect changing threats.Remember, security is an ongoing process that requires constant attention and maintenance!