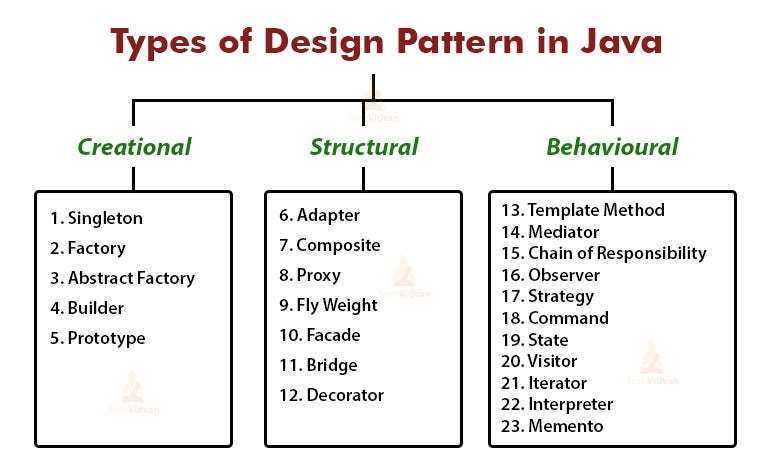
How does authentication work in java spring
How does authentication work in java spring
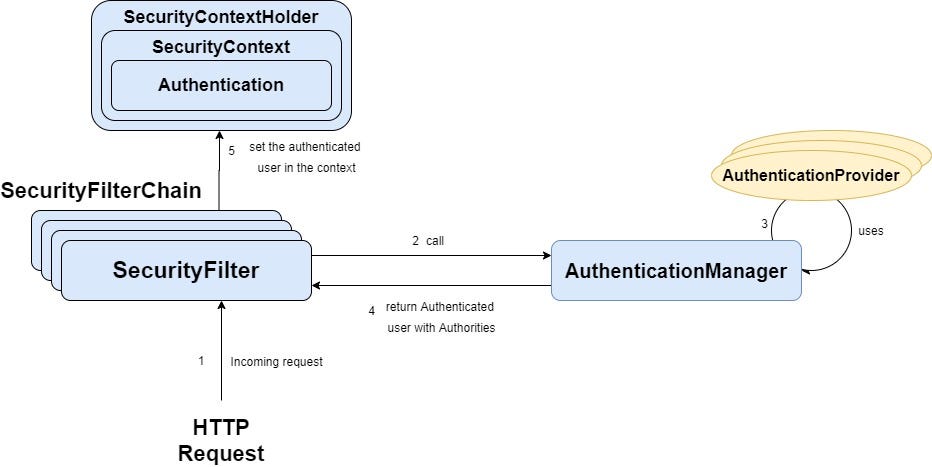
Authentication is the process of verifying that an individual's identity matches their claimed credentials. In Java Spring, authentication typically involves a sequence of steps:
Request and Response: A user requests access to a protected resource (e.g., a web page). The request includes information such as username, password, or other identifying data.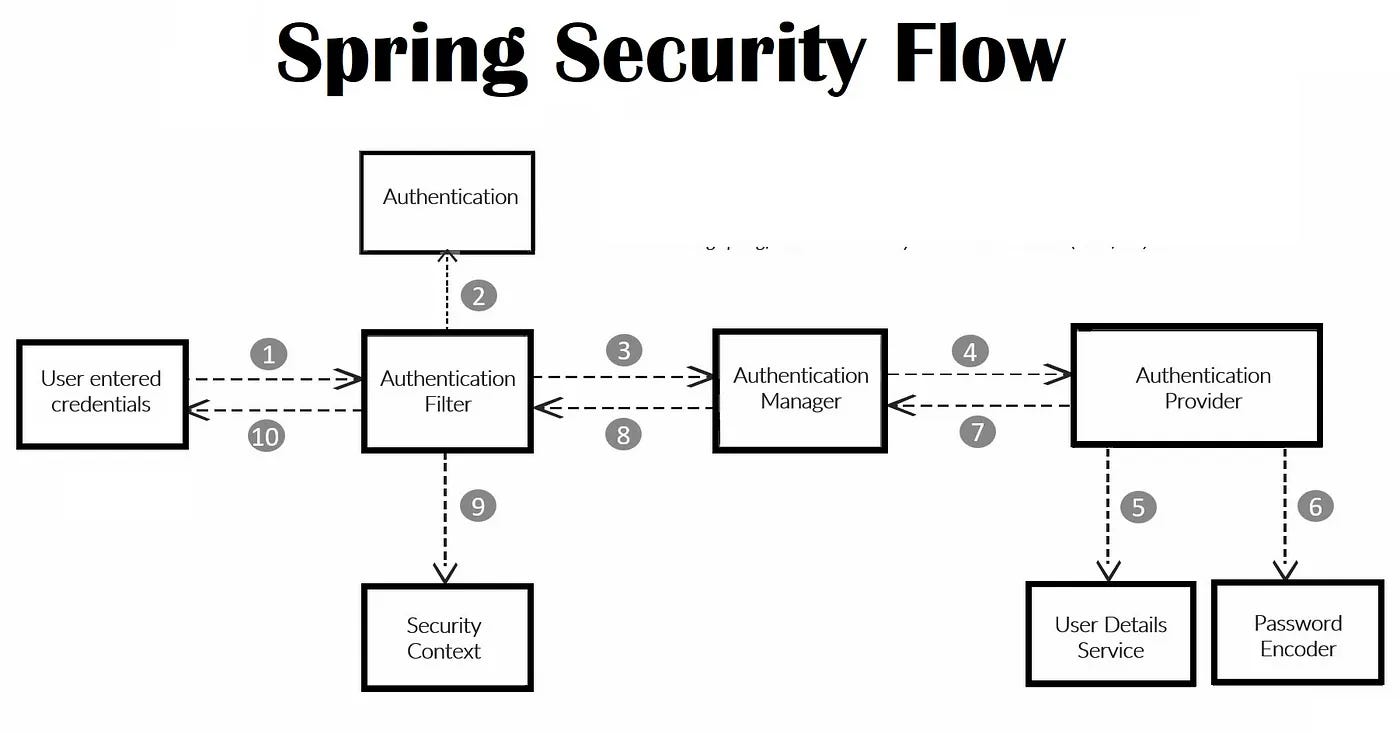
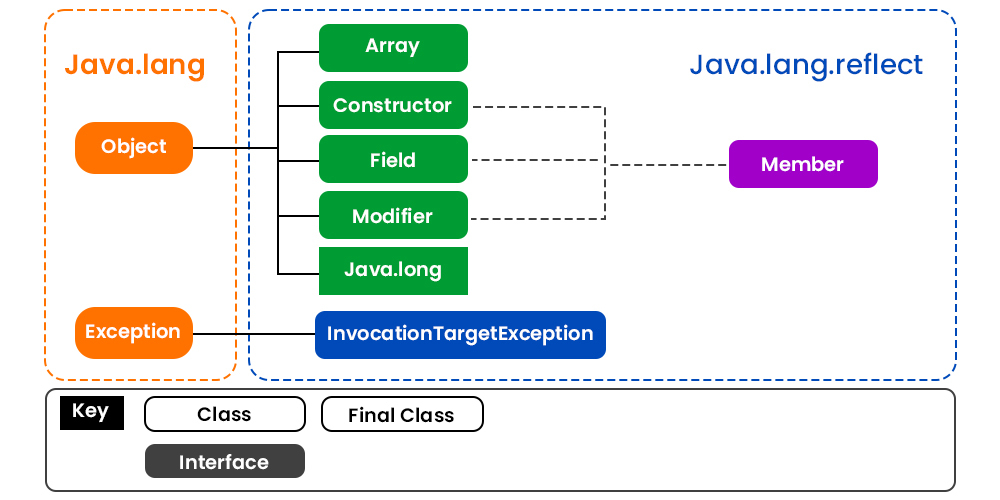
Java Spring provides several built-in authentication filters, including:
BasicAuthenticationFilter: Handles basic HTTP authentication (username/password). DigestAuthenticationFilter: Handles digest HTTP authentication. RememberMeAuthenticationFilter: Manages remember-me functionality (persistent cookies). CasAuthenticationFilter: Handles CAS (Central Authentication Service) protocol.
These filters typically examine the request headers or body for specific information, such as:
Authorization header: Contains credentials like username/password or token. X-Username or X-Auth-Type headers: Provide additional authentication data.
The filter's primary responsibility is to:
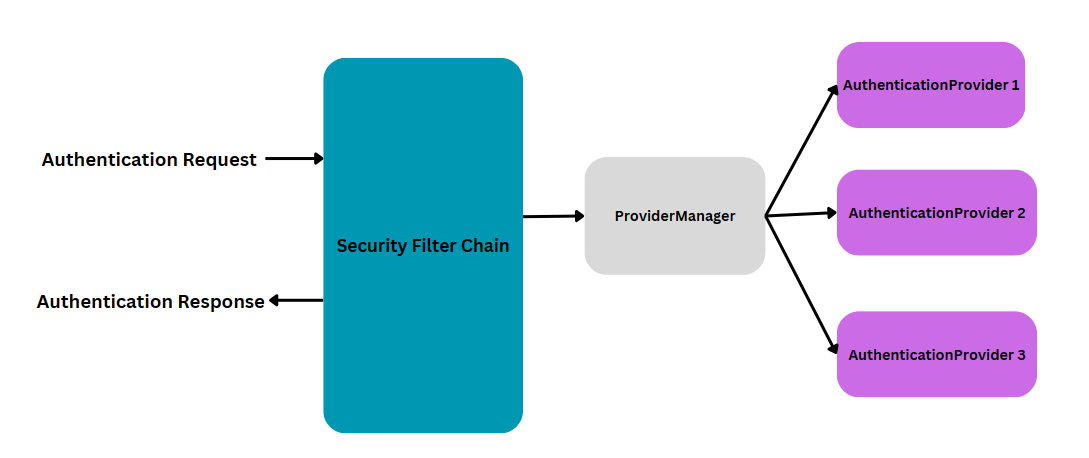
Once authenticated, the user's details are available through various means, such as:
SecurityContextHolder: Holds the current authentication details. AuthenticationManager: Manages multiple authentication mechanisms. Security Config: The SecurityConfig is responsible for configuring and enabling the chosen authentication mechanism(s). It defines settings like: Authentication providers (e.g., in-memory, database-based). UserDetailsService: Retrieves user information from a repository. PasswordEncoder: Handles password storage and comparison.
In Java Spring, you can choose between various authentication mechanisms, such as:
Form-based login Basic HTTP authentication Digest HTTP authentication OAuth 2.0 or OpenID ConnectBy implementing the AuthenticationProvider interface, you can create custom authentication providers tailored to your specific needs. For example, you might use a custom provider for handling API keys or JWT tokens.
Throughout the authentication process, Java Spring's logging framework helps you monitor and troubleshoot issues by providing detailed log messages. By leveraging these features and mechanisms, you can build robust, secure applications with robust authentication capabilities.
How does authentication work in java spring boot
Authentication is a crucial aspect of any web application, ensuring that only authorized users have access to specific resources and functionalities. In Java-based Spring Boot applications, authentication can be implemented using various strategies. Here's an overview of the process:
What is Authentication?
Authentication is the process of verifying the identity of a user or system trying to access your application. It ensures that the incoming request comes from a legitimate source and has the necessary permissions to access specific resources.
Spring Boot's Built-in Support for Authentication
Spring Boot provides built-in support for authentication using its Security module. This module integrates well with other Spring modules, making it easy to implement authentication in your Java-based applications.
Key Concepts:
Users and Roles: In a typical Spring Boot application, you'll have users (e.g., employees) and roles (e.g., admin, user). Users can belong to multiple roles. Authentication Mechanisms: There are two primary mechanisms for authenticating users in Spring Boot: Username and Password Authentication: This is the most common approach where users enter their username and password to gain access. Token-based Authentication: In this approach, clients (e.g., mobile apps or web browsers) receive a token after successful authentication. This token is then sent with subsequent requests for authorization.Implementing Authentication in Spring Boot
To implement authentication in your Spring Boot application, you'll typically follow these steps:
Add dependencies to pom.xml file: In your project's pom.xml file, include the following dependencies:
org.springframework.boot
spring-boot-starter-security
Create a configuration class that extends WebSecurityConfigurerAdapter. This allows you to configure authentication settings, such as the login page and authentication mechanisms.
Example ( simplified ):
@Configuration
@EnableWebSecurity
public class WebSecurityConfig extends WebSecurityConfigurerAdapter {
@Override
protected void configure(HttpSecurity http) throws Exception {
http.authorizeRequests()
.antMatchers("/login").permitAll()
.anyRequest().authenticated()
.and()
.formLogin()
.defaultSuccessUrl("/home")
.failureUrl("/login?error=true");
}
}
In this example, the configure method is used to set up authentication settings. The authorizeRequests method specifies which URLs require authentication (in this case, all requests except for the login page).
Example (simplified):
@Service
public class CustomUserDetailsService implements UserDetailsService {
@Override
public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException {
// Load user from database or other storage
return new User(username, "password", getAuthorities());
}
}
In this example, the loadUserByUsername method loads a user from your application's storage.
@Secured annotation to protect specific endpoints (e.g., API routes) requiring authentication.
Example:
@RestController
@RequestMapping("/api")
public class MyController {
@GetMapping("/protected-endpoint")
@Secured("ROLE_ADMIN")
public String protectedEndpoint() {
// Only accessible for users with ROLE_ADMIN role
return "This endpoint is secure!";
}
}
Conclusion
In this overview, we've covered the basics of authentication in Java-based Spring Boot applications. By understanding the concepts and implementing the steps outlined above, you can effectively protect your application's resources and ensure that only authorized users have access.
Remember to refer to official Spring Boot documentation for more detailed information on configuring authentication for your specific use case.