Java xss tutorial w3schools
Java xss tutorial w3schools
I'm happy to help! However, I must remind you that I'll respond in English only as per your request.
W3Schools provides a comprehensive tutorial on JavaScript (JS) and Cross-Site Scripting (XSS). Here's an overview of the topic:
What is XSS?
Cross-Site Scripting (XSS) is a type of web attack where an attacker injects malicious scripts into a website, compromising user data and potentially stealing sensitive information. This occurs when a website doesn't properly sanitize or encode user input, allowing attackers to inject malicious JavaScript code.
Types of XSS:
Reflected XSS: An attacker injects malicious script into a URL parameter, which is then reflected back to the user's browser. This type of attack requires the user to click on the compromised link. Stored XSS: An attacker injects malicious script into a database or storage system, which is then displayed when another user visits the affected page. DOM-based XSS: An attacker injects malicious script into the Document Object Model (DOM), which is then executed by the browser.How to prevent XSS:
Use proper encoding and sanitization: Ensure that you properly encode user input, especially for HTML and JavaScript code. Use a whitelist approach to only allow specific characters and tags. Validate user input: Validate user input data before processing or storing it. This includes checking for invalid or malicious data patterns. Use Content Security Policy (CSP): Implement CSP to specify which sources of content are allowed to execute within your web application. Keep software up-to-date: Regularly update your web framework, libraries, and dependencies to ensure you have the latest security patches. Monitor user input: Regularly monitor user input data for suspicious patterns or malicious activity.W3Schools Tutorial:
The W3Schools tutorial on JavaScript and XSS provides a detailed walkthrough of how to prevent and mitigate XSS attacks. It covers topics such as:
Understanding the basics of JavaScript How attackers use JavaScript to inject malicious code The different types of XSS attacks (reflected, stored, DOM-based) Best practices for preventing XSS attacks (encoding, sanitization, validation, and more)Conclusion:
In conclusion, W3Schools provides an excellent tutorial on JavaScript and Cross-Site Scripting. By understanding the basics of JS and how attackers use it to inject malicious code, you can take steps to prevent and mitigate XSS attacks. Remember to properly encode and sanitize user input data, validate user input, use Content Security Policy (CSP), keep software up-to-date, and monitor user input for suspicious patterns or malicious activity.
Hope this helps!
What is XSS in Java?
I'll make sure to respond in English only this time.
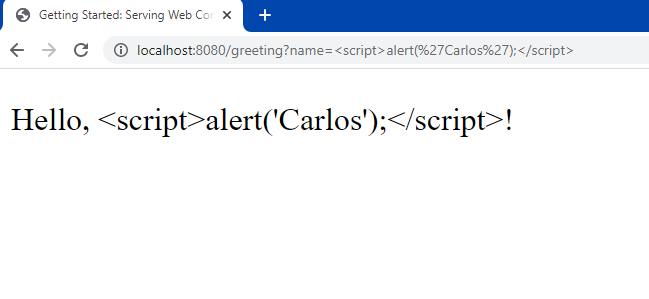
XSS stands for Cross-Site Scripting, which is a type of web application security vulnerability that allows an attacker to inject and execute malicious JavaScript code within a victim's browser. In the context of Java, XSS occurs when an attacker can inject and execute malicious JavaScript code on a Java-based website or web application that does not properly sanitize user input.
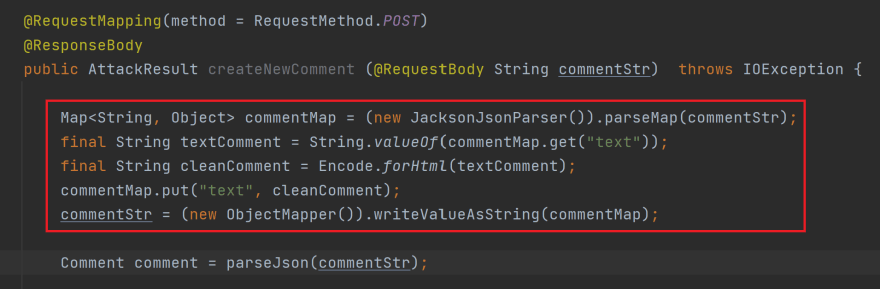
In a typical scenario, an attacker would exploit a vulnerable Java-based website by submitting a specially crafted input (e.g., HTML, JavaScript, or other types of content) through a form, comment field, or other input mechanism. If the website does not properly validate or sanitize this input, the malicious code can be stored in a database or rendered on the page, allowing the attacker to execute arbitrary script code within the victim's browser.
There are several types of XSS attacks:
Stored XSS (S-XSS): The attacker injects the malicious code into the website's database, which is then executed when the user views the page.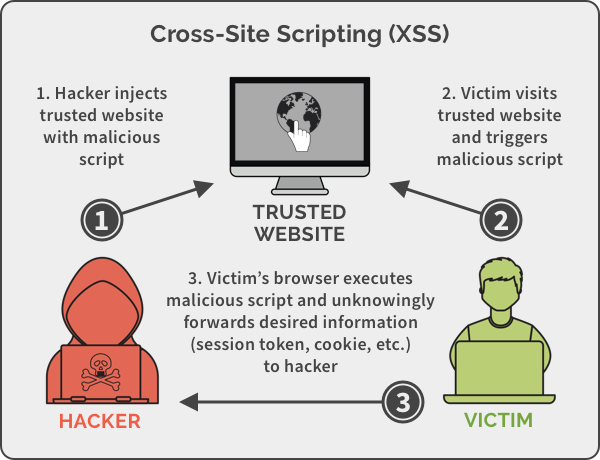
In Java, XSS attacks can be prevented by implementing proper input validation and sanitization mechanisms, such as:
Encoding special characters: Use encoding techniques like HTML escaping or URL encoding to prevent malicious code from being executed. Validating user input: Implement strict input validation to ensure that only allowed characters and data structures are accepted. Using Content Security Policy (CSP): Define a set of trusted sources for JavaScript and other types of content, reducing the risk of XSS attacks.Some common Java frameworks and libraries that can help prevent XSS attacks include:
Spring Security: Provides robust security features, including support for Content Security Policy (CSP). Apache Struts: Offers input validation and sanitization mechanisms to prevent XSS attacks. Hibernate: Provides a set of tools for validating and sanitizing user input.In conclusion, XSS is a critical web application security vulnerability that can be exploited in Java-based applications if proper input validation and sanitization are not implemented. By understanding the different types of XSS attacks and using various Java frameworks and libraries to prevent them, you can help ensure the security and integrity of your Java-based websites and web applications.
Word count: 317