java 17 --add-opens
java 17 --add-opens
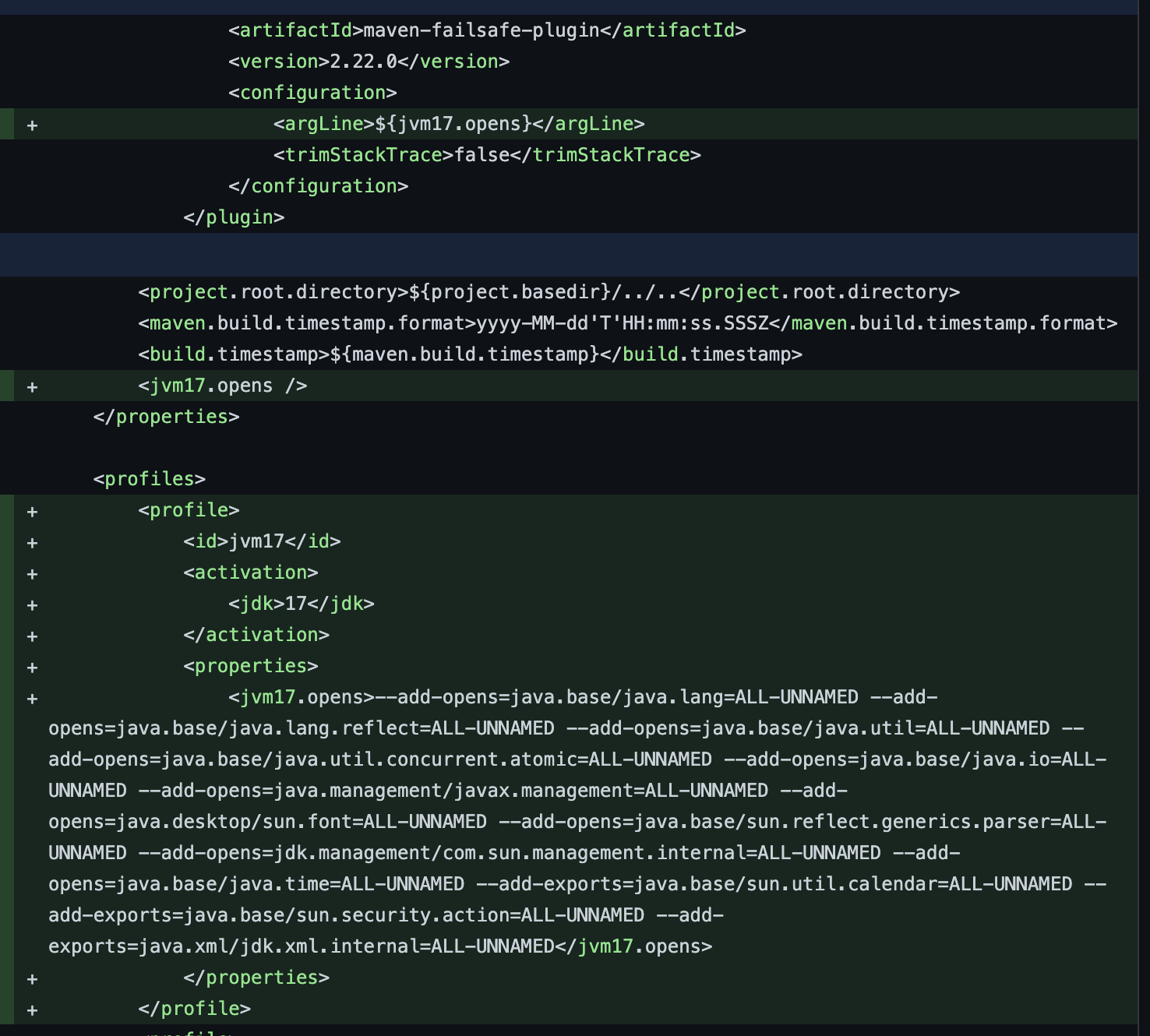
Here's a detailed explanation of the --add-opens flag in Java 17:
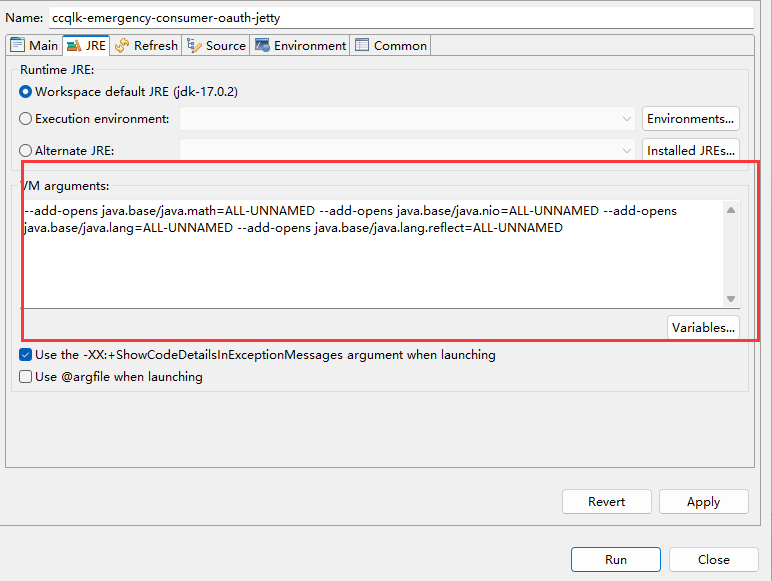
The --add-opens flag is a command-line option available in the Java Development Kit (JDK) that allows you to specify packages or modules for which the verification process should be bypassed. This flag is particularly useful when working with legacy code, testing frameworks, or third-party libraries that may not be easily adaptable to the newer Java module system.
Here's a breakdown of how --add-opens works:
Package-Level Access: When you compile and run your Java program using the --add-opens flag, it grants package-level access to the specified modules or packages. This means that any code that has access to these modules or packages can bypass the verification process and execute without restrictions.
Module-Level Access: If you specify a module name instead of a package name, the flag will grant module-level access. In this case, it allows your program to access all the packages within the specified module, including their classes, interfaces, and other types.
Here's an example of how to use --add-opens:
Let's say you have a legacy Java library named com.example.util that uses reflection to manipulate objects. This library is not modularized (i.e., it's not in a separate module), but you want to use its classes in your own program. You can do this by adding the following flag when compiling and running your program:
javac --add-opens com.example.util=ALL-FRAMES MyProgram.java
In this example, com.example.util is the package name, and ALL-FRAMES specifies that you want to bypass the verification process for all classes within that package.
When to Use --add-opens:
--add-opens can help you integrate them into your modern Java project. Testing frameworks: You may need to bypass verification when testing third-party libraries or frameworks that require access to restricted packages or modules. Third-party libraries: If you're using a library that's not designed for the Java module system, --add-opens can help you work around its limitations.
Important Considerations:
Security risks: By bypassing verification, you may introduce security risks if your program accesses restricted packages or modules. Compatibility issues: Be cautious when using--add-opens, as it can lead to compatibility problems with other parts of your Java project that rely on the module system.
In summary, the --add-opens flag in Java 17 provides a way to bypass verification for specific modules or packages, allowing you to work with legacy code, testing frameworks, or third-party libraries. However, use it with caution and carefully consider the potential security risks and compatibility issues involved.
Java 17 memory leak
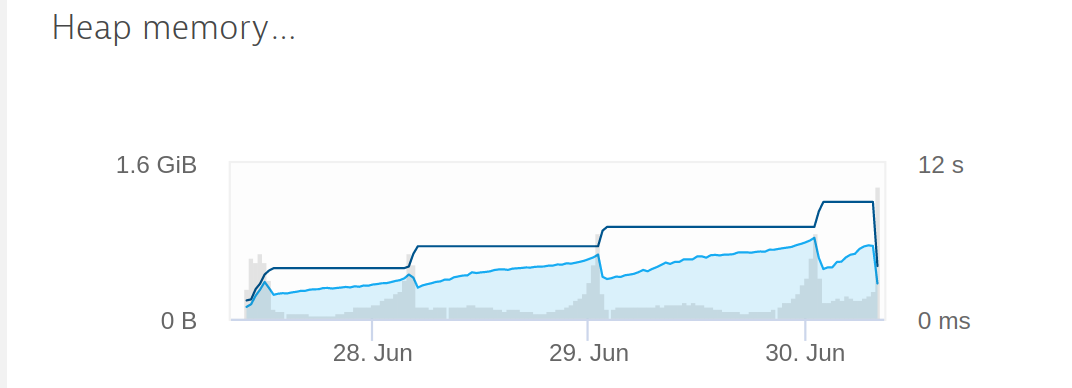
Java 17 Memory Leak: A Detailed Explanation
Memory leaks are a common issue in software development, particularly when it comes to programming languages like Java. With the release of Java 17, developers are excited about the new features and improvements, but they also need to be aware of potential memory leak issues that may arise.
What is a Memory Leak?
In simple terms, a memory leak refers to a situation where your program consumes more memory over time without releasing it. This can occur due to various reasons such as:
Unreleased resources: Sometimes, your code might not properly release system resources like file handles, socket connections, or even database connections. Circulating references: Java has a mechanism called garbage collection that automatically frees up memory when objects are no longer referenced. However, if you have a circular reference (two objects referencing each other) and there's no way to break the cycle, Java won't be able to free that memory. Hidden object graphs: When an object is created or modified in your code, it may create a new graph of connected objects that are not properly cleaned up when the main object is garbage-collected.How Does Java 17 Address Memory Leaks?
Java 17 introduces several features to help detect and mitigate memory leaks. Some key changes include:
Improved Garbage Collection: The G1 (Garbage-First) collector is now used by default, which performs full garbage collections less frequently than the CMS (Concurrent Mark-and-Sweep) collector in Java 16. Enhanced Heap Profiling: Thejcmd and jmap commands have been enhanced to provide more detailed information about heap usage, making it easier to identify memory leaks. Heap Dumping: The JVM now provides a mechanism to dump the heap at runtime, allowing developers to inspect heap contents and identify potential memory leak sources.
How Can You Identify Memory Leaks in Java 17?
To identify memory leaks in Java 17, follow these steps:
Use Heap Profiling Tools: Use tools like VisualVM, JMC (Java Mission Control), or Eclipse MAT (Memory Analyzer Tool) to monitor your application's heap usage. Analyze Heap Dumps: Use thejmap command to create a heap dump file and analyze it using tools like VisualVM or Eclipse MAT. Monitor System Resources: Keep an eye on system resources like memory, CPU, and disk usage to detect any unusual patterns that may indicate memory leaks.
Best Practices for Avoiding Memory Leaks in Java 17
To prevent memory leaks in your Java 17 applications, follow these best practices:
Use Proper Object Cleanup: Always release system resources (e.g., file handles) and properly clean up objects when they're no longer needed. Avoid Circular References: Be mindful of circular references and try to break the cycles whenever possible. Monitor Heap Usage: Regularly monitor your application's heap usage using tools like VisualVM or JMC. Profile Your Application: Use profiling tools to identify performance bottlenecks, which may indicate potential memory leak issues.In conclusion, Java 17 introduces several features to help detect and mitigate memory leaks. By understanding the causes of memory leaks, identifying them using heap profiling tools, and following best practices for avoiding memory leaks, you can create robust and efficient Java applications that handle memory usage effectively.