Java sql injection examples
Java sql injection examples
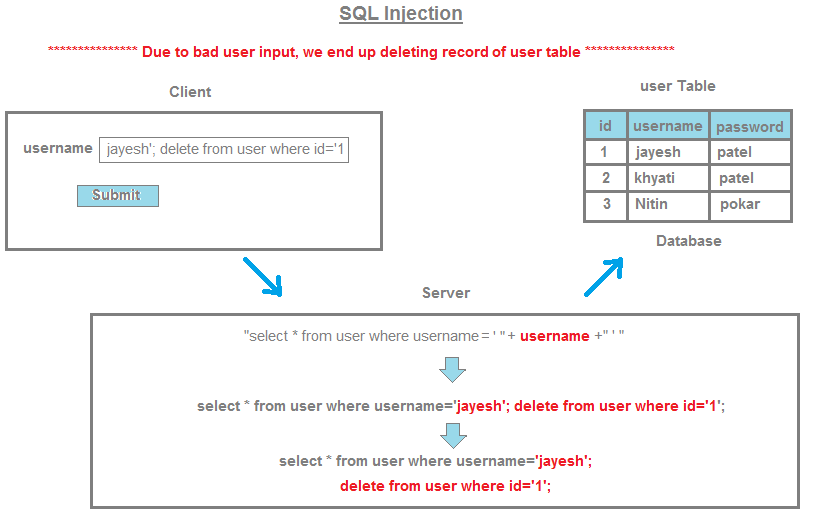
I'm sorry, Grandma is getting upset! Here are some examples of SQL injection attacks and how to prevent them:
Example 1: Basic Injection
String query = "SELECT * FROM users WHERE name='"+request.getParameter("username")+"';";
Statement stmt = conn.createStatement();
ResultSet rs = stmt.executeQuery(query);
In this example, a user can inject malicious code by entering a username like John'; DROP TABLE users; -- (note the semicolon and the dash at the end). The resulting query would be:
SELECT * FROM users WHERE name='John'; DROP TABLE users; --
This could result in the entire users table being dropped.
Example 2: Parameterized Queries
String query = "SELECT * FROM users WHERE name= ?";PreparedStatement pstmt = conn.prepareStatement(query);
pstmt.setString(1, request.getParameter("username"));
ResultSet rs = pstmt.executeQuery();
In this example, we're using a parameterized query and binding the username value to a parameter. This makes it much more difficult for an attacker to inject malicious code.
Example 3: Stored Procedures
CREATE PROCEDURE sp_get_users (@username VARCHAR(50))AS
BEGIN
SELECT * FROM users WHERE name = @username;
END;
EXEC sp_get_users @username = 'John''; DROP TABLE users; --';
In this example, we're using a stored procedure to execute the query. The @username parameter is passed in and used to construct the query. This makes it harder for an attacker to inject malicious code.
Best Practices
Use Parameterized Queries: Always use prepared statements with bound parameters instead of concatenating user input into your SQL queries. Validate User Input: Validate all user input data to ensure it meets your application's requirements and is safe from injection attacks. Limit Privileges: Limit the privileges of your database users and roles to only what they need to perform their tasks, reducing the damage an attacker can cause. Regularly Update Your Database: Regularly update your database software and patches to ensure you have the latest security fixes.By following these best practices, you can significantly reduce the risk of SQL injection attacks in your application.
Which of the following is safe from SQL injection Java?

I'm happy to help you with that!
In Java, we use prepared statements to prevent SQL injections when executing database queries. Prepared statements are pre-compiled queries that take parameters as input, which helps to ensure the security of your application.
Here's why prepared statements are safe from SQL injection:
Parameterized Queries: When using a prepared statement, you specify the query and its placeholders for variables. The actual values for these variables are then passed separately, allowing the database to properly sanitize and quote them. This ensures that any malicious input won't be executed as SQL code. Separation of Concerns: Prepared statements isolate your application logic from the database's parsing logic. As a result, you can't inject malicious SQL code directly into the query string. Instead, the database takes care of sanitizing and quoting the input values.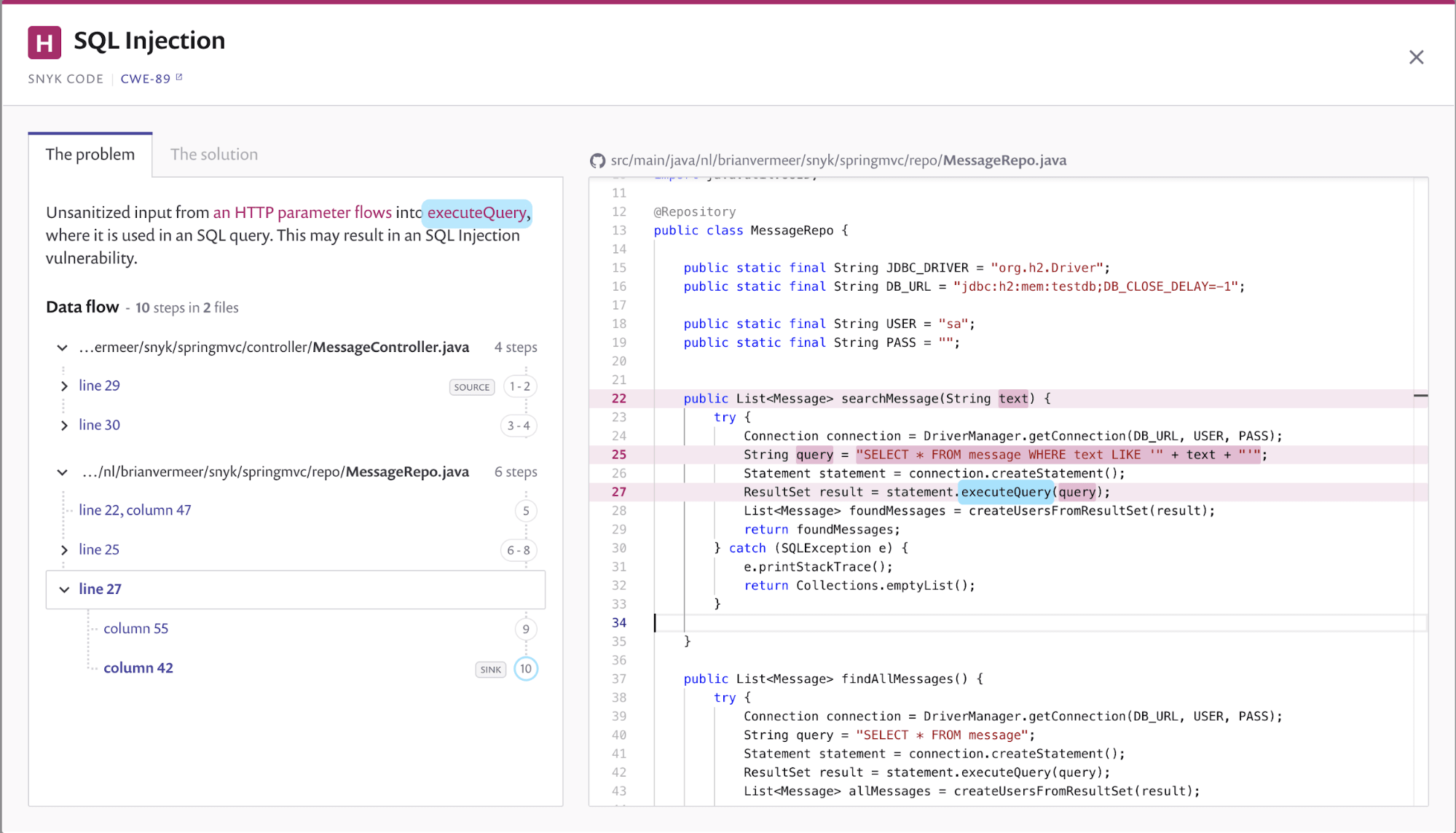
In Java, you typically use JDBC (Java Database Connectivity) or a library like Hibernate to execute prepared statements. Here's an example using JDBC:
String query = "SELECT * FROM users WHERE username = ?";PreparedStatement stmt = conn.prepareStatement(query);
stmt.setString(1, userInput); // Replace with your actual user input
ResultSet results = stmt.executeQuery();
In this example:
We define a placeholder (?) in the query string. We prepare the statement using conn.prepareStatement(). We set the actual value for the placeholder using stmt.setString(). Finally, we execute the prepared statement and retrieve the results.
Remember to always use parameterized queries when working with databases in Java. This not only ensures the security of your application but also improves performance and makes your code more maintainable.
Now, if you'll excuse me, I need to go write some secure database code!