Java authentication and authorization service spring boot
Java authentication and authorization service spring boot

Java Authentication and Authorization Service for Spring Boot
Authentication and authorization are crucial components of a web application's security infrastructure. In the context of a Spring Boot application, you can utilize various libraries and tools to implement these features. One popular option is Java Authentication and Authorization Service (JAAS).
What is JAAS?
JAAS stands for Java Authentication and Authorization Service. It is an API provided by Oracle that allows developers to integrate authentication and authorization functionality into their applications. The primary goal of JAAS is to provide a standardized way of handling user authentication and access control in a multi-user environment.
How Does JAAS Work?
The basic workflow of JAAS involves the following steps:


Advantages of Using JAAS in Spring Boot
Decoupling Security and Business Logic: By separating security concerns from business logic, you create a more modular application that is easier to maintain and extend. Standardized API: JAAS provides a standardized API for authentication and authorization, making it easier to integrate with other libraries and tools. Scalability: As your application grows in complexity and user base, JAAS can handle the increased load while maintaining performance. Flexibility: You can customize JAAS to fit your specific security needs by creating custom login modules, subjects, and policies.How to Integrate JAAS with Spring Boot
To integrate JAAS with Spring Boot, you need to follow these steps:
Add the Required Dependencies: In yourpom.xml file (if you're using Maven) or build.gradle file (if you're using Gradle), add the required dependencies for JAAS and Spring Security. Configure JAAS: Create a custom JAAS configuration by defining login modules, subjects, and policies in the application's security settings. Use Spring Security to Secure Your Application: Use Spring Security to secure your application by configuring user details, roles, and permissions.
Conclusion
JAAS is an excellent choice for implementing authentication and authorization in your Spring Boot applications. Its standardized API, scalability, flexibility, and ability to decouple security concerns from business logic make it a valuable tool in any developer's toolkit. By following the steps outlined above, you can successfully integrate JAAS with Spring Boot and build robust, secure applications.
Java authentication and authorization service example

Here is an example of a simple Java-based authentication and authorization service:
What is Authentication?
Authentication is the process of verifying the identity of a user or system to ensure that they are who they claim to be. In other words, it's about confirming that a user is legitimate and authorized to access a particular system, network, or application.
What is Authorization?
Authorization is the process of deciding what actions a verified user can perform once they've been authenticated. It determines whether a user has permission to read, write, delete, or execute certain data or resources.
Example Architecture:
Let's design a simple authentication and authorization service using Java:
User Repository: Store users' information in a database or file system. Each user is identified by a unique ID (e.g., username). Authentication Service: Implement an interface that contains the following methods:authenticate(String username, String password): Verify the provided credentials against the user repository. getUserId(String username): Retrieve the user's ID based on their username. Authorization Service: Create another interface that provides the following methods: hasPermission(int userId, String permission): Check if a user with the given ID has the specified permission (e.g., "read", "write", "execute"). getPermissions(int userId): Retrieve the list of permissions for a specific user. Application: Use these services to authenticate and authorize users when they interact with your application.
Here's some sample code:
// User Repository
public class UserStore {
private Map<String, User> users = new HashMap<>();
public void addUser(User user) {
users.put(user.getUsername(), user);
}
public User getUser(String username) {
return users.get(username);
}
}
// Authentication Service
public interface Authenticator {
boolean authenticate(String username, String password);
int getUserId(String username);
}
// Authorization Service
public interface Authorizer {
boolean hasPermission(int userId, String permission);
List getPermissions(int userId);
}
// Sample User class
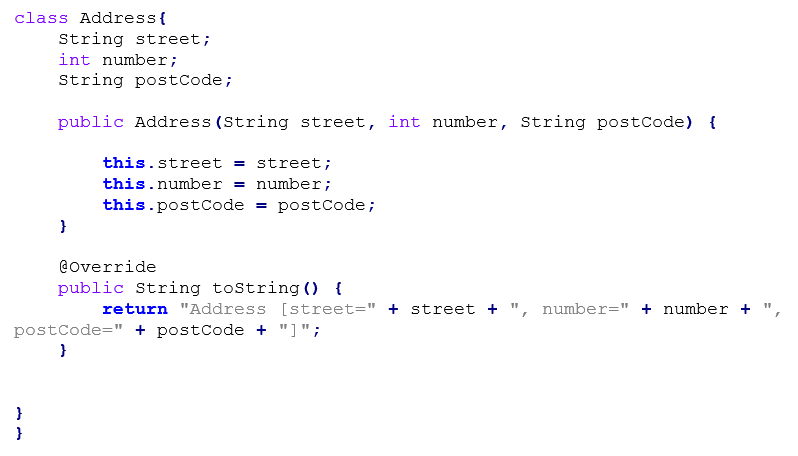
public class User {
private int id;
private String username;
private String password;
public User(int id, String username, String password) {
this.id = id;
this.username = username;
this.password = password;
}
public int getId() {
return id;
}
public String getUsername() {
return username;
}
}
// Sample Application
public class MyApp {
private Authenticator auth;
private Authorizer authz;
public MyApp(UserStore userStore) {
auth = new AuthenticatorImpl(userStore);
authz = new AuthorizerImpl();
}
public void login(String username, String password) {
if (auth.authenticate(username, password)) {
int userId = auth.getUserId(username);
// Perform authorized actions based on the user's permissions
List permissions = authz.getPermissions(userId);
for (String permission : permissions) {
System.out.println("User has permission: " + permission);
}
} else {
System.out.println("Invalid credentials");
}
}
}
In this example, we have a simple UserStore that manages user information. The Authenticator interface provides methods for authenticating users and retrieving their IDs. The Authorizer interface handles permissions and checks whether a user has a specific permission.
The sample application uses these services to authenticate and authorize users when they interact with the system. For example, when a user logs in, the app verifies their credentials using the Authenticator, retrieves their ID, and then checks which permissions they have based on the Authorizer. This allows us to control access to different resources and actions within our application.
Of course, this is a simplified example, and you'll need to add more features, such as session management, to create a robust authentication and authorization system.