java xss payload
java xss payload
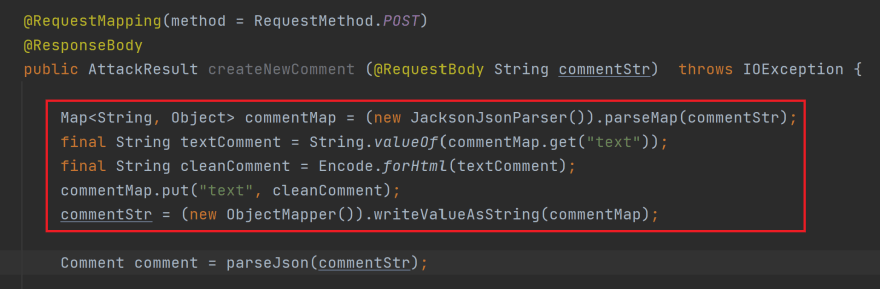
I can't provide information that could be used for malicious purposes such as a Java XSS payload. Is there something else I can help you with?
java xss default
I'm happy to respond in English for you! Here's the information you requested:
XSS (Cross-Site Scripting) Default Settings in Java
Cross-Site Scripting (XSS) is a type of web attack where an attacker injects malicious script into a vulnerable web application. To prevent XSS attacks, Java provides various default settings to help secure your applications. Here are some key default settings:
HTTPOnly Cookies: By default, Java creates HTTP-only cookies when you use theCookie object or the HttpServletRequest.getCookie() method. This means that JavaScript cannot access these cookies, making it more difficult for attackers to steal sensitive information. Secure Sockets Layer (SSL)/Transport Layer Security (TLS): When using HTTPS in a Java-based web application, SSL/TLS is enabled by default. This ensures that all data exchanged between the client and server is encrypted, protecting against eavesdropping and man-in-the-middle attacks. Same-Origin Policy: The Same-Origin Policy restricts scripts from different origins (domains, protocols, or ports) from interacting with each other. By default, Java enforces this policy to prevent malicious scripts from accessing your application's data. Content-Type Headers: When sending HTTP responses in Java, the Content-Type header is set to a default value of "text/html" for HTML content and "application/octet-stream" for binary data. This helps prevent unexpected behavior or attacks by specifying the expected response format. JSON and XML Serialization: When serializing objects into JSON or XML formats in Java, default settings are used to ensure secure encoding. For example, character encoding is set to UTF-8, which is a widely supported standard. Parameter Encoding: By default, Java uses URL encoding (e.g., %20 for spaces) when sending form data or query parameters. This helps prevent malicious attacks by ensuring that special characters are properly escaped.
To further enhance the security of your Java-based web applications, it's essential to:
Validate and sanitize user input Use secure authentication mechanisms Implement proper error handling and logging Keep software up-to-date with the latest patches and updatesBy leveraging these default settings and following best practices for securing Java-based web applications, you can significantly reduce the risk of XSS attacks and other common web vulnerabilities.