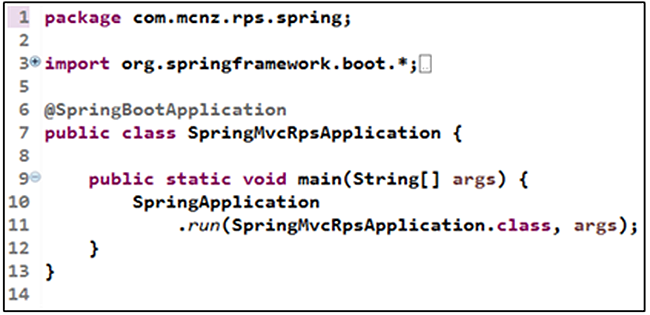
java rmi architecture
java rmi architecture
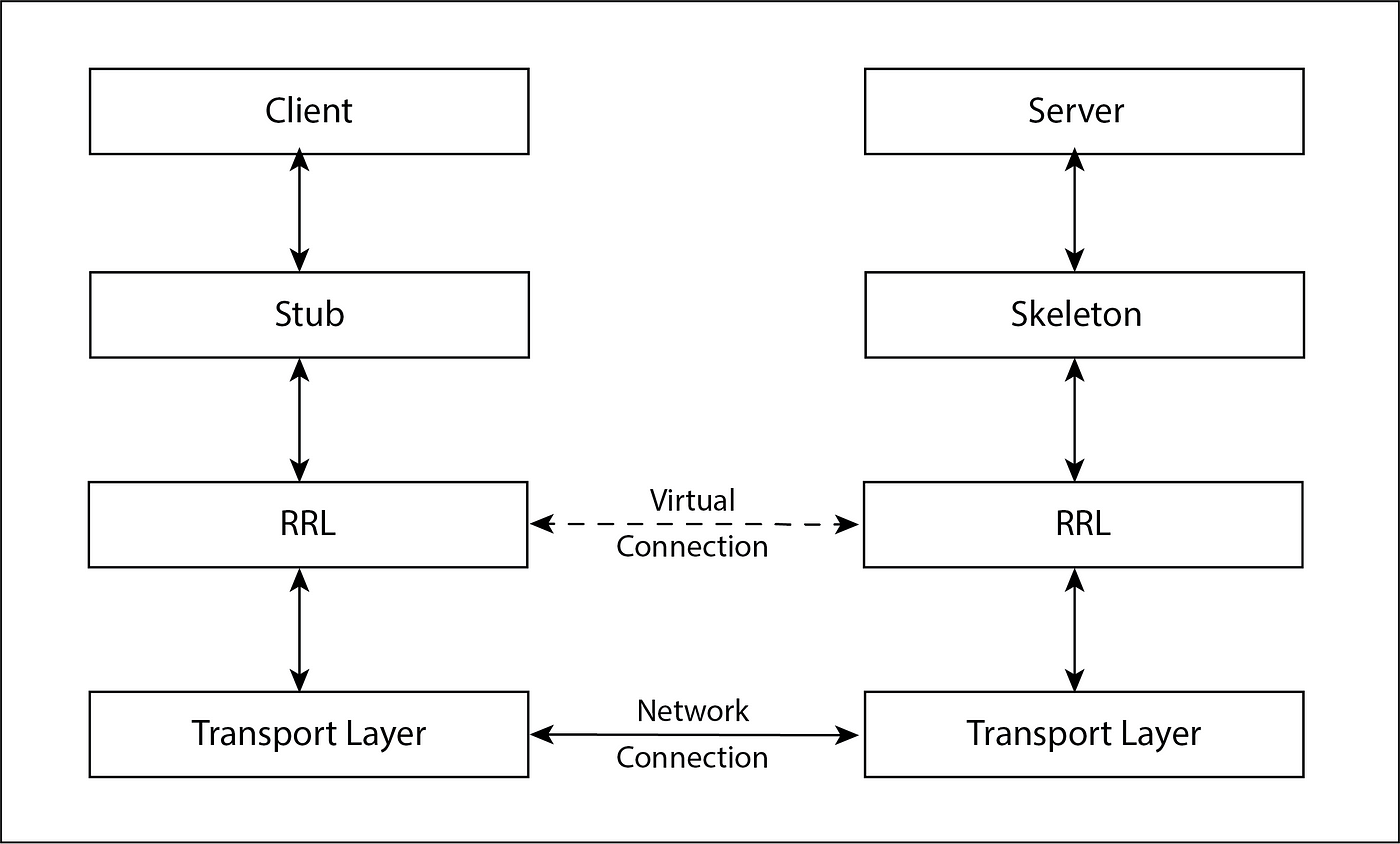
Here is a detailed explanation of the Java RMI (Remote Method Invocation) architecture:
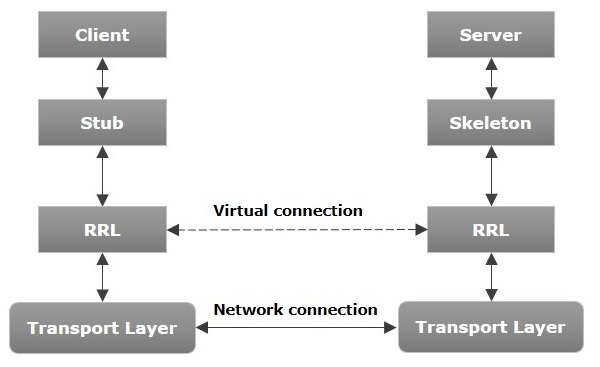
Overview
Java RMI is a protocol that enables Java objects to interact with each other remotely, allowing for distributed computing and communication between multiple nodes in a network. It provides a way for Java objects on different machines to communicate with each other as if they were located on the same machine.
Architecture Components
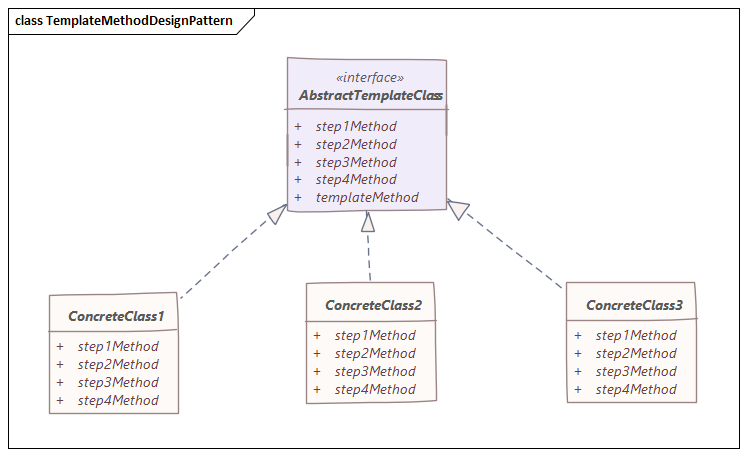
The Java RMI architecture consists of several components:
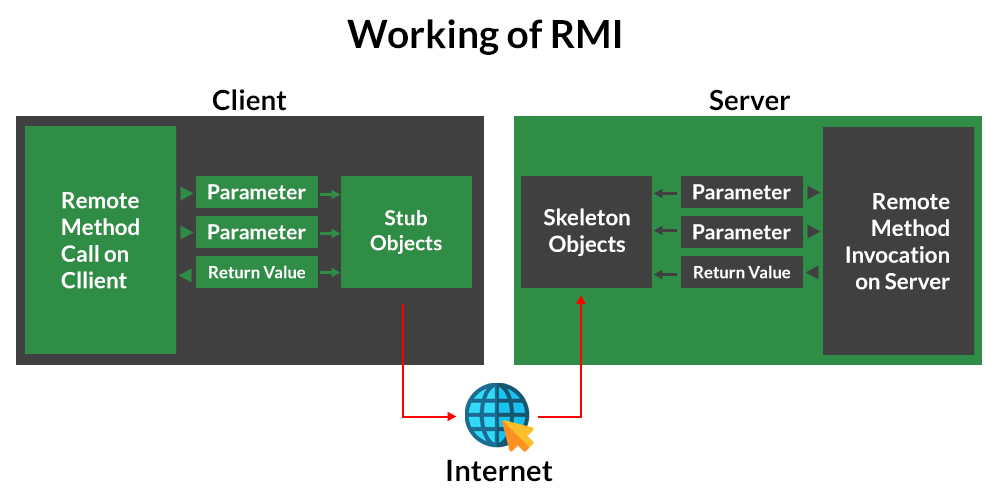
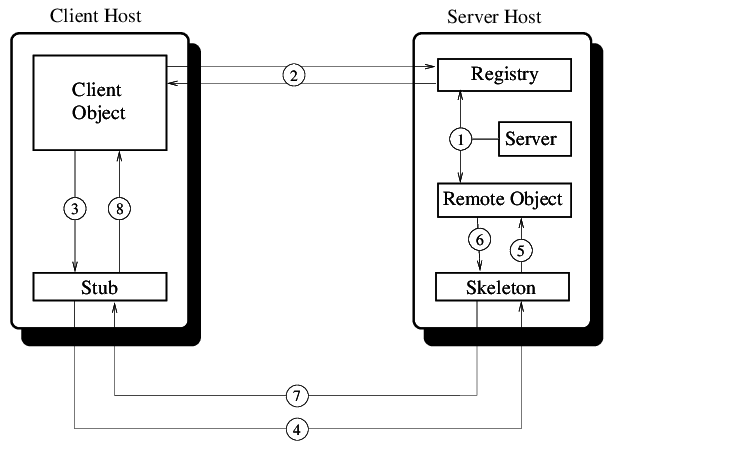
Step-by-Step Process
Here's how RMI works:
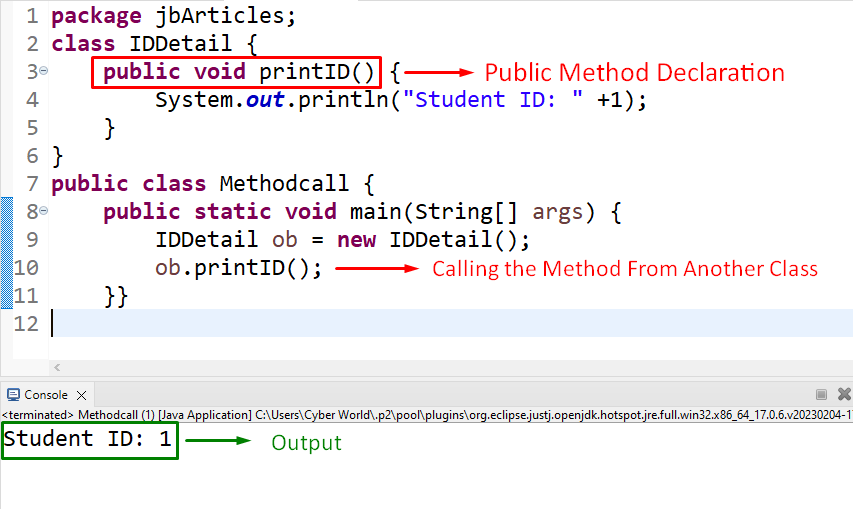
Server Side: The remote object is created and implements the Remote interface. The remote object is registered with the RMI Registry using a unique identifier (UID). The RMI Registry creates an entry for the remote object, including its UID and location. Client Side: The client creates an RMISocketFactory object to establish a connection to the RMI Registry. The client uses the RMISocketFactory to create an RMIClientSocketFactory object that will handle the communication with the RMI Registry. The client sends a request to the RMI Registry to locate and obtain a reference to the remote object. The RMI Registry returns the UID of the remote object, along with its location information. The client uses this information to establish a connection with the remote object and invoke its methods.Key Concepts
Some key concepts in Java RMI include:
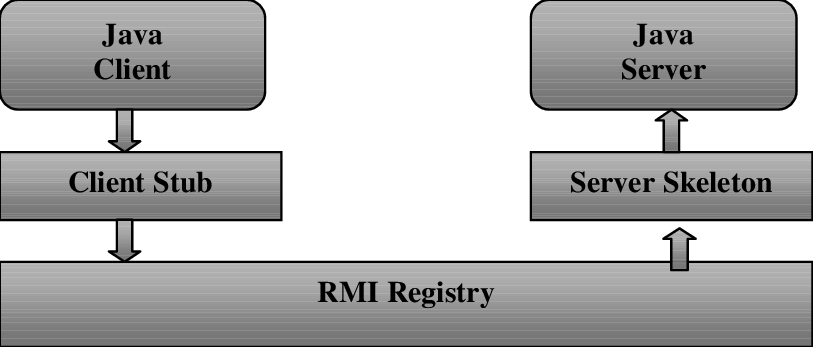
UIDs: Unique identifiers that are used to identify remote objects and manage their registration with the RMI Registry. Stub Objects: Small, lightweight Java objects that act as intermediaries between clients and remote objects. Stubs handle method invocations on behalf of the client. Skeleton Objects: Server-side components that provide the implementation for stub objects.Advantages
Java RMI provides several advantages:
Distributed Computing: Enables distributed computing by allowing Java objects to interact with each other remotely. Flexibility: Allows for dynamic registration and lookup of remote objects, making it easy to add or remove services from a network. Platform Independence: Enabling Java objects on different platforms to communicate with each other.Challenges
Some challenges associated with Java RMI include:
Performance Overhead: Due to the added layer of abstraction and communication overhead, RMI can introduce performance latency. Security Concerns: Requires careful consideration of security and authentication mechanisms to ensure data integrity and confidentiality.I hope this provides a comprehensive overview of the Java RMI architecture!
java rmi exploit
I'll respond in English as requested!
Java RMI Exploit: A Threat to Remote Method Invocation
Remote Method Invocation (RMI) is a powerful feature in Java that enables remote method calls between objects, allowing for distributed computing and communication. However, like many powerful technologies, it also presents an opportunity for malicious actors to exploit vulnerabilities. In this response, we'll explore the concept of RMI exploits, their impact, and mitigation strategies.
What are RMI Exploits?
RMI exploits refer to attacks that take advantage of weaknesses in the RMI protocol, allowing unauthorized access or control over a Java-based system. These exploits typically involve manipulating serialized object graphs (SOGs) or exploiting vulnerabilities in the RMI implementation itself. Malicious actors may target specific versions of the RMI system or attempt to create a backdoor for future attacks.
Common Types of RMI Exploits:
Serialization Attacks: By crafting malicious serialized objects, attackers can inject arbitrary code into an unsuspecting Java process. RMI-Reflection Attacks: These attacks involve manipulating the RMI registry to gain control over remote methods or inject custom classes. Unvalidated Data: Failing to validate user-input data in RMI-based applications can lead to code injection or exploitation of vulnerabilities.Impact:
Successful RMI exploits can lead to severe consequences, such as:
Unauthorized access to sensitive data Code execution with elevated privileges System compromise and remote control Data destruction or corruptionMitigation Strategies:
Validate User Input: Always validate user input data in your RMI-based applications to prevent code injection attacks. Use Secure Sockets: Implement secure socket layer (SSL) or transport layer security (TLS) encryption when communicating with RMI systems. Disable RMI by Default: Set thermii parameter to false in your Java Virtual Machine (JVM) configuration, limiting access to only trusted hosts. Keep Your JVM and Libraries Up-to-Date: Regularly update your JVM, libraries, and RMI implementations to patch known vulnerabilities. Implement Authentication and Authorization: Use robust authentication mechanisms and authorize remote method calls based on user roles or permissions.
Conclusion:
RMI exploits are a serious threat to Java-based systems. Understanding the types of attacks, their impact, and mitigation strategies is crucial for securing your RMI-enabled applications. Always prioritize security best practices when developing and deploying RMI-based systems.
Please let me know if you have any follow-up questions!