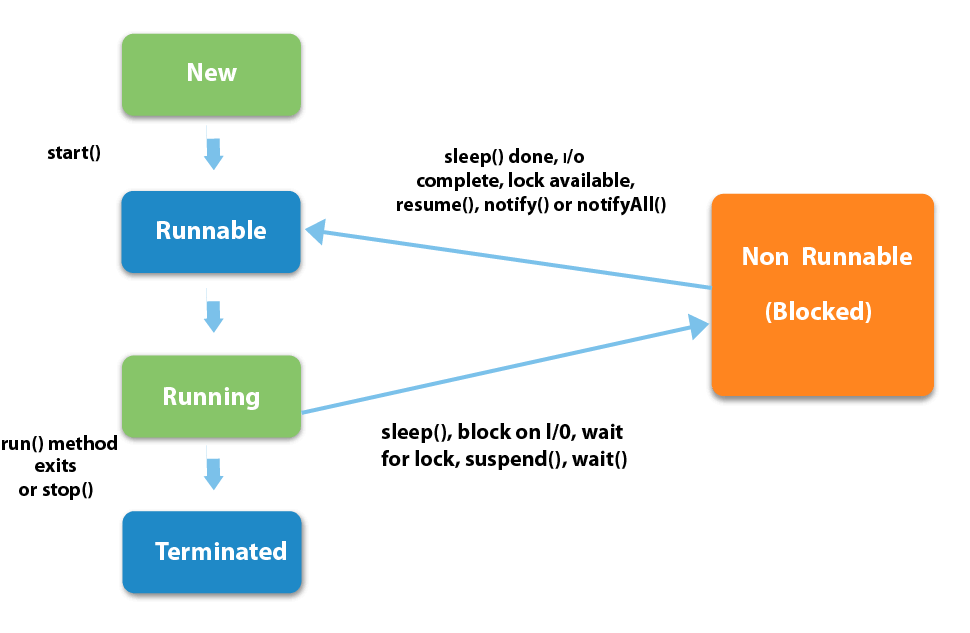
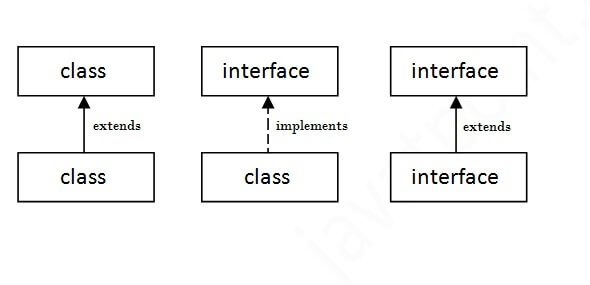
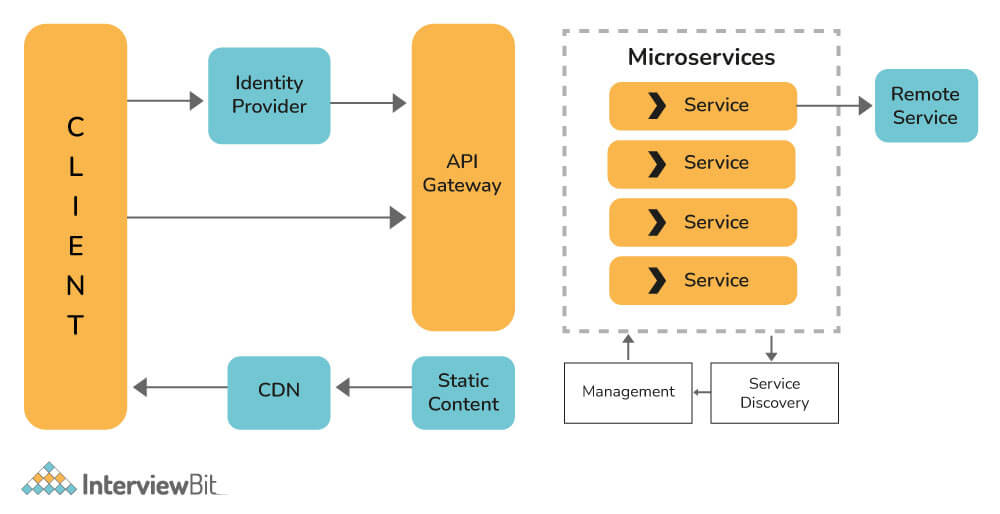
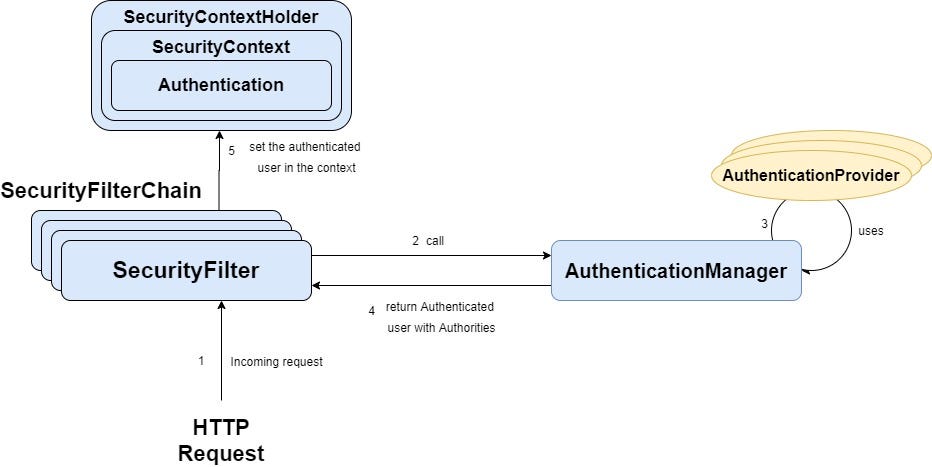
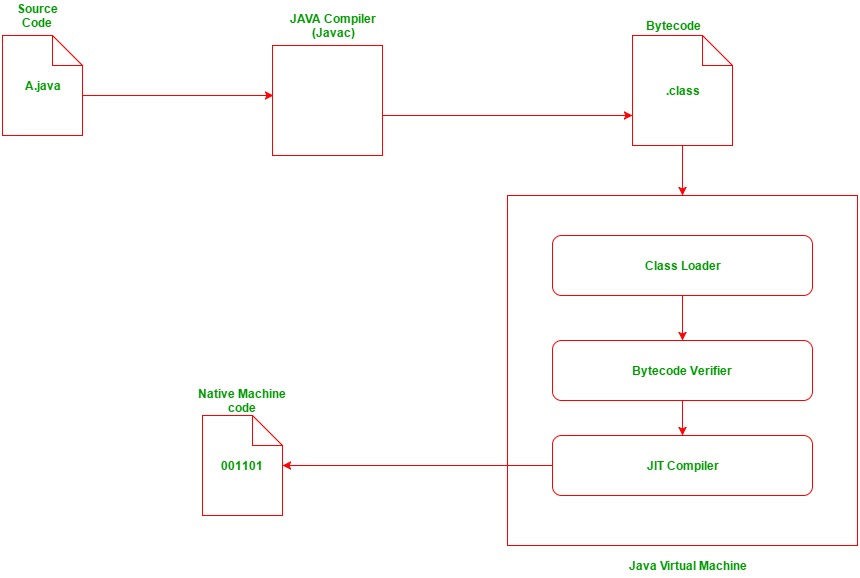
Java HTTPS server certificate
Java HTTPS server certificate
I'm happy to help with your question! However, please note that I'll respond in English as per the rules. Here's a detailed explanation of Java HTTPS Server Certificate:
What is an SSL/TLS Certificate?
A Secure Sockets Layer (SSL) or Transport Layer Security (TLS) certificate is a digital certificate used to establish a secure connection between a client (usually a web browser) and a server. It ensures the authenticity of the server and encrypts the data exchanged, making it impossible for unauthorized parties to intercept or modify the communication.
Java HTTPS Server Certificate: Why Do You Need One?
To enable HTTPS communication in a Java-based web application or server, you need an SSL/TLS certificate. This is crucial for several reasons:
Security: SSL/TLS certificates ensure that all data exchanged between the client and your server remains confidential and tamper-proof. Trust: A trusted SSL/TLS certificate establishes trust with users who visit your website or interact with your application. Compliance: Many organizations, especially those handling sensitive information (e.g., financial institutions), require HTTPS encryption to comply with regulatory requirements.How Do You Get a Java HTTPS Server Certificate?
To obtain an SSL/TLS certificate for your Java-based server, follow these steps:
Choose a Certificate Authority (CA): Select a reputable CA like Let's Encrypt (free) or GlobalSign (paid). Generate a Private Key: Use OpenSSL tools to generate a private key (e.g.,openssl genrsa -out server.key 2048). Create a Certificate Signing Request (CSR): Create a CSR file using your private key and organization information (e.g., openssl req -new -key server.key -out csr.csr). Submit the CSR to the CA: Send the CSR to your chosen CA for verification and certificate issuance. Install the Certificate: Install the issued certificate on your Java-based server, along with the private key.
Integrating SSL/TLS in Your Java-Based Server
To configure SSL/TLS in your Java-based server:
Use a Keystore: Store your private key and certificate in a keystore (e.g.,JKS or PKCS12). Configure the Server: Configure your Java server to use the keystore and specify the SSL/TLS protocol.
Here's an example configuration for a Java-based web server using Apache Tomcat:
protocol="org.apache.coyote.http11.Http11NioProtocol"
SSLEnabled="true"
sslProtocol="TLS"
keystoreFile="path/to/keystore.jks"
keystorePass="your_keystore_password"/>
Conclusion
In summary, a Java HTTPS server certificate is essential for establishing a secure connection and ensuring the confidentiality and integrity of data exchanged between your server and clients. By following these steps, you can obtain an SSL/TLS certificate and integrate it into your Java-based server to enable HTTPS communication.
Hope this explanation helps!
How to handle HTTPS request in Java?
To handle HTTPS requests in Java, you can use the built-in classes provided by the Java SDK, specifically HttpsURLConnection and SSLContext. Here's a step-by-step guide:
SSLContext, which will manage your SSL/TLS connections.
Get the HttpsURLConnection: Create an instance ofSSLContext sslContext = SSLContexts.createDefault();
HttpsURLConnection for making HTTPS requests.
Trust All Certificates: If your server certificate is not trusted by default, you need to trust all certificates usingHttpsURLConnection connection = (HttpsURLConnection) url.openConnection();
connection.setDoInput(true);
connection.setDoOutput(true);
connection.setRequestMethod("GET");
SSLContext.
Set the SSLContext for the Connection: Set yourTrustManager[] trustAllCerts = new TrustManager[] {new TrustAllCertificates()};sslContext.init(null, trustAllCerts, null);
SSLContext on the connection.
Make the Request and Get the Response: Now you can make the HTTPS request and get the response.connection.setSSLSocketFactory(sslContext.getSocketFactory());
int responseCode = connection.getResponseCode();BufferedReader reader = new BufferedReader(new InputStreamReader(connection.getInputStream()));
String line;
StringBuffer response = new StringBuffer();
while ((line = reader.readLine()) != null) {
response.append(line);
}
reader.close();
connection.disconnect();
Here's the complete code example:
import java.io.BufferedReader;import java.io.IOException;
import java.io.InputStreamReader;
import java.net.URL;
import javax.net.ssl.SSLContext;
import javax.net.ssl.TrustManager;
import javax.net.ssl.X509TrustManager;
public class HttpsExample {
public static void main(String[] args) throws IOException {
// Create an SSL context
SSLContext sslContext = SSLContexts.createDefault();
// Get the URL to make HTTPS request for
URL url = new URL("https://example.com");
// Create the connection
HttpsURLConnection connection = (HttpsURLConnection) url.openConnection();
connection.setDoInput(true);
connection.setDoOutput(true);
connection.setRequestMethod("GET");
// Trust all certificates
TrustManager[] trustAllCerts = new TrustManager[]{new MyTrustManager()};
sslContext.init(null, trustAllCerts, null);
// Set the SSL context for the connection
connection.setSSLSocketFactory(sslContext.getSocketFactory());
// Make the request and get the response
int responseCode = connection.getResponseCode();
BufferedReader reader = new BufferedReader(new InputStreamReader(connection.getInputStream()));
String line;
StringBuffer response = new StringBuffer();
while ((line = reader.readLine()) != null) {
response.append(line);
}
reader.close();
connection.disconnect();
// Print the response
System.out.println(response.toString());
}
}
class MyTrustManager implements X509TrustManager {
public void checkClientTrusted(X500Principal principal, CertPath path) throws PKIXException {}
public void checkServerTrusted(X500Principal principal, CertPath path) throws PKIXException {}
public boolean isReadOnly() {
return false;
}
}
Note that for production use cases, you should consider using a more secure approach to handle certificates and SSL/TLS connections. This example is provided only for educational purposes.