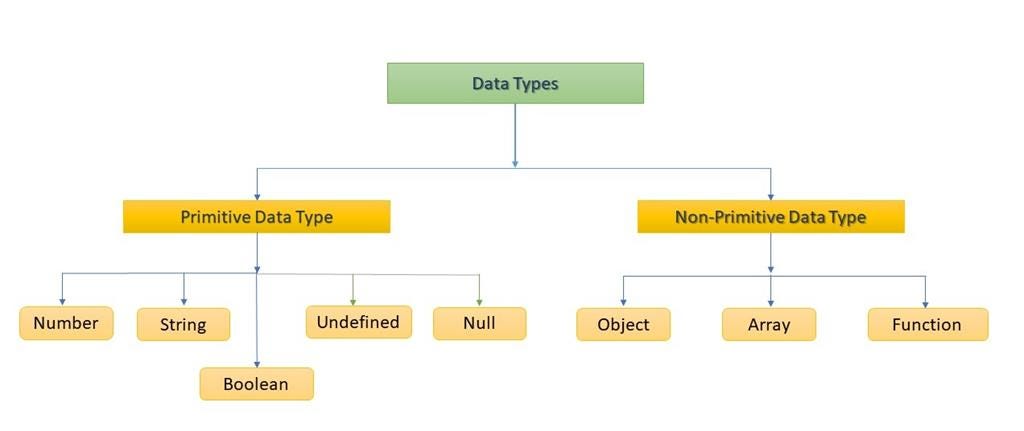
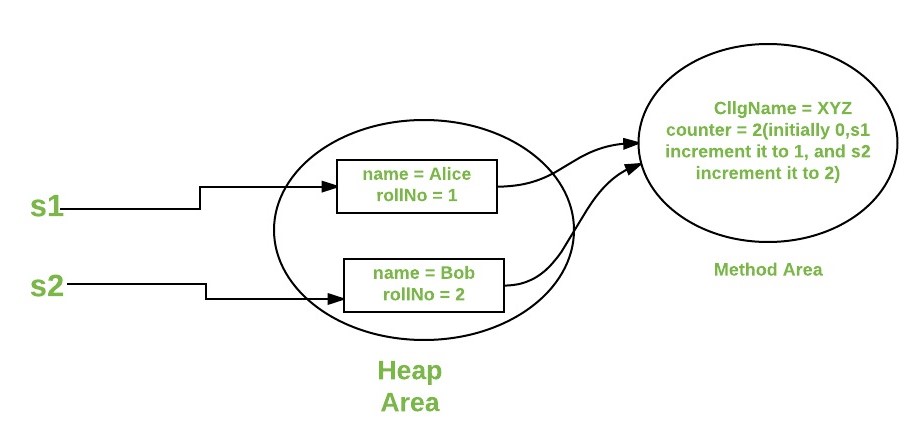
Java xss jvm example
Java xss jvm example
I'm glad you asked! Here's a detailed explanation of a Java XSS (Cross-Site Scripting) attack using the JVM (Java Virtual Machine).
What is Cross-Site Scripting (XSS)?
Cross-Site Scripting is a type of web-based vulnerability that allows an attacker to inject malicious JavaScript code into a website. This can be used to steal user data, hijack user sessions, or even take control of the victim's browser.
How does XSS work?
Here's a step-by-step example of how an attacker might use Java to launch an XSS attack:
JavaScript Injection: The attacker crafts a malicious JavaScript code that, when executed by the victim's browser, can steal user data or hijack their session. Java-based Web Application: The attacker identifies a vulnerable web application written in Java. This application uses a Java servlet to handle HTTP requests and responses. Deserialization Vulnerability: The attacker discovers a deserialization vulnerability in the Java-based web application. This means that the application's deserialization mechanism (e.g., JSON or XML parsing) can be tricked into executing arbitrary code.Example Code:
Here's an example of how the attacker might exploit this vulnerability using Java:
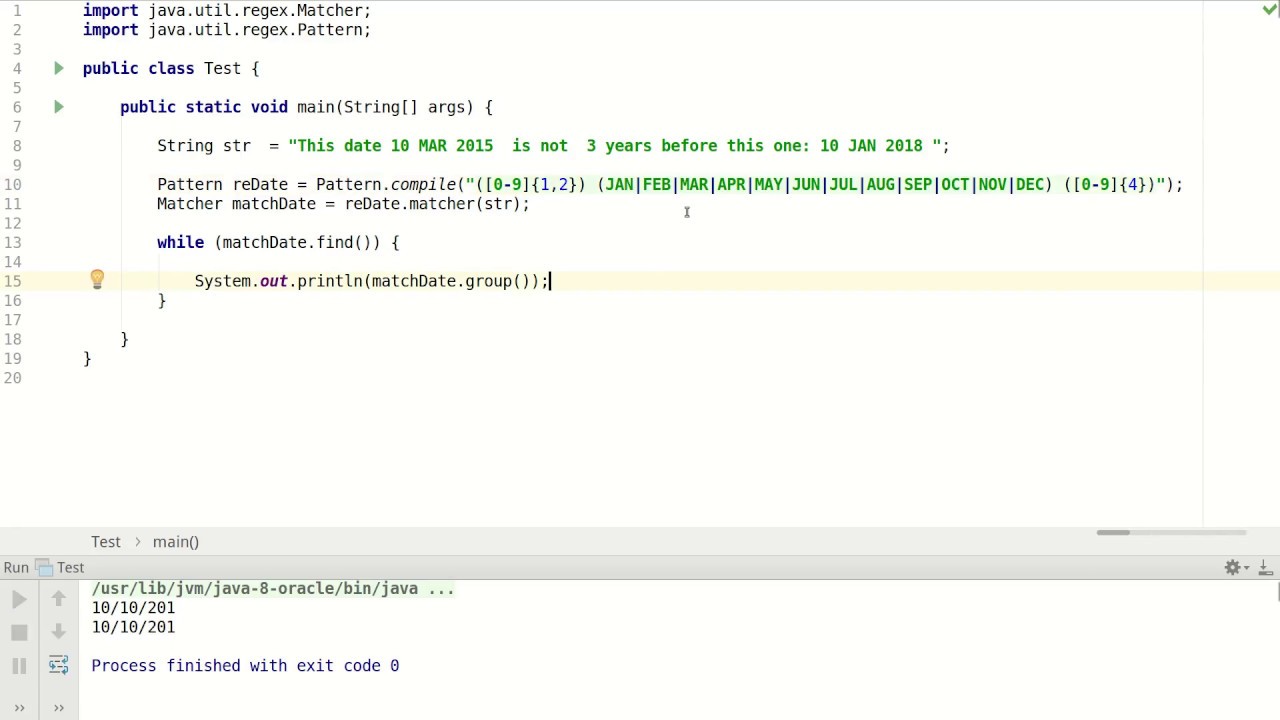
// Attacker-controlled input: user-supplied data
String userInput = "";
// Vulnerable deserialization mechanism
JSONParser jsonParser = new JSONParser();
JSONObject jsonObject = jsonParser.parse(userInput);
// Execute malicious code
jsonObject.toString();
// The vulnerable web application will execute the attacker's JavaScript code
In this example, the attacker crafts a malicious userInput string that contains an <script> tag. When the deserialization mechanism parses this input, it will execute the attacker's JavaScript code, which can steal user data or hijack their session.
Mitigating XSS Attacks:
To prevent XSS attacks like this one, you should follow these best practices:
Input Validation: Validate all user-supplied inputs thoroughly to ensure they do not contain malicious code. Output Encoding: Always encode output to prevent malicious code from being executed by the browser. Content Security Policy (CSP): Implement a CSP to define which sources of content are allowed to be executed by the browser.Conclusion:
In this example, we saw how an attacker might use Java to launch a Cross-Site Scripting attack on a vulnerable web application. By following best practices like input validation, output encoding, and implementing a Content Security Policy, you can help prevent such attacks from succeeding.
Java VM options
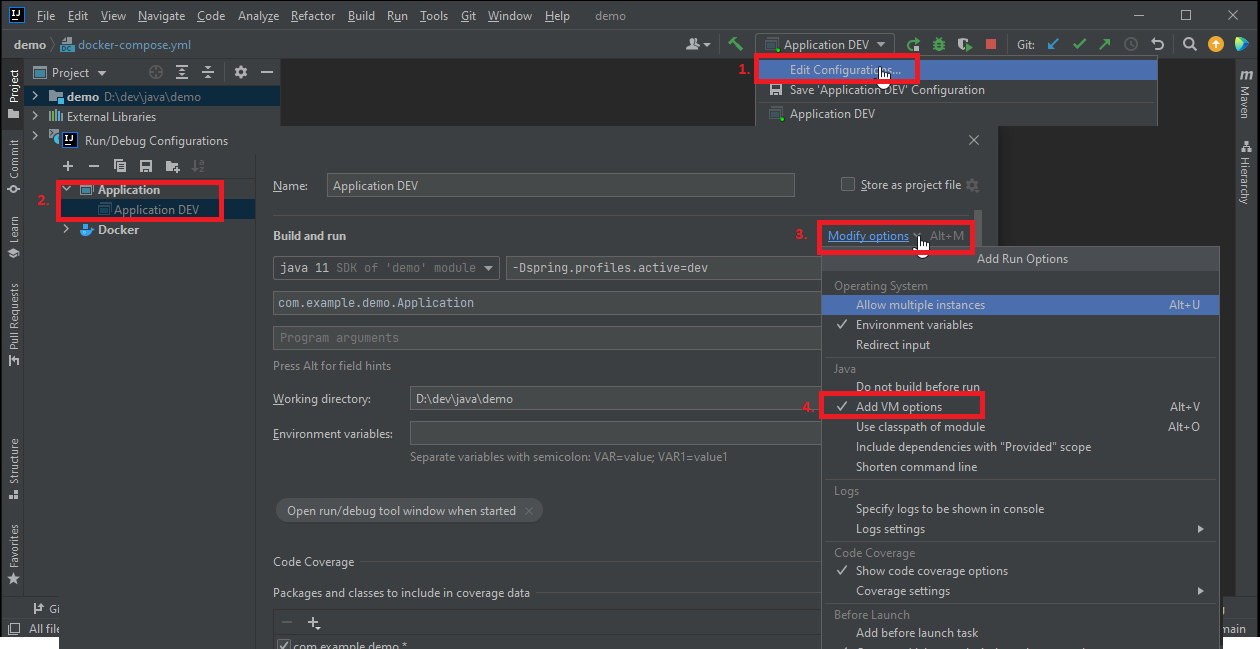
Here's the information you need on Java Virtual Machine (JVM) options:
Introduction
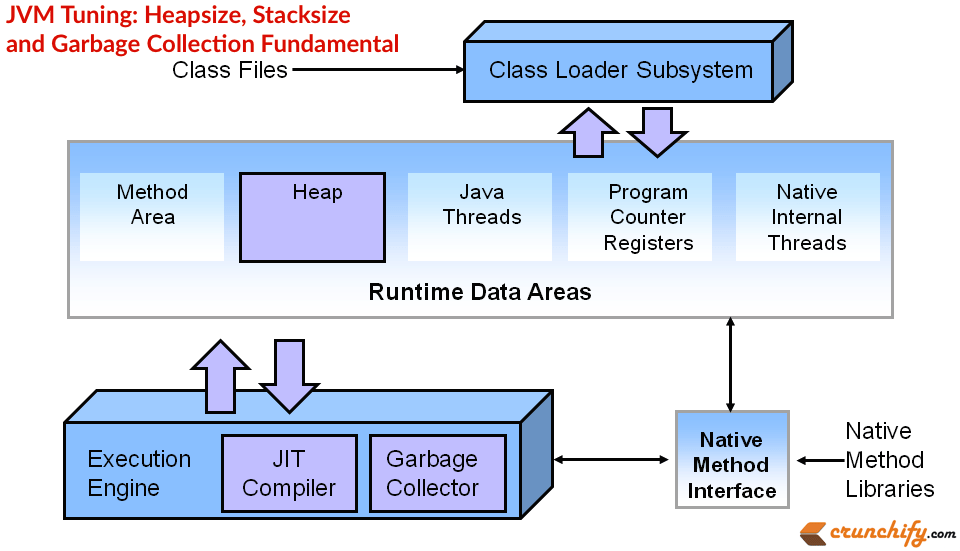
The Java Virtual Machine (JVM) is a crucial component of the Java platform, responsible for executing Java bytecode into machine-specific code that can be executed by the computer. The JVM provides a runtime environment for your Java applications to run in, which means it takes care of tasks such as memory management, garbage collection, and security.
Java VM Options
The JVM allows you to specify options when running a Java application using the java command. These options can be used to control various aspects of the JVM's behavior, such as memory allocation, garbage collection frequency, and more. Here are some common JVM options:
-Xmx512m sets the maximum heap size to 512 megabytes.
Example: java -Xmx512m MyJavaApp
-Xmx, this option specifies the initial amount of memory that the JVM should allocate for your application. This can help prevent garbage collection from occurring too frequently at startup.
Example: java -Xms128m -Xmx256m MyJavaApp
Example: java -XX:+UseG1GC MyJavaApp
Example: java -verbose:class MyJavaApp
-Dfile.encoding=UTF-8 sets the file encoding to UTF-8).
Example: java -Duser.timezone=US/Pacific MyJavaApp
or--class-path`: These options specify one or more directories or JAR files that contain classes and resources for your application.
Example: java -cp mylib.jar:myotherlib.jar MyJavaApp
Example: java -jar myapp.jar
Example: java -showversion MyJavaApp
or--enableassertions: These options enable assertions for a specific package or class (e.g.,-ea:com.example.MyPackageenables assertions in all classes within thecom.example.MyPackage` package).
Example: java -ea com.example.MyClass
or--client: This option enables client-mode JVM settings, which are optimized for running Java applications on a server or workstation.
Example: java -client MyJavaApp
Conclusion
These are just a few of the many options you can specify when running a Java application using the java command. By mastering these options, you can fine-tune your JVM's behavior to suit your specific needs and optimize the performance of your applications.