How to add CSRF token in java?
How to add CSRF token in java?
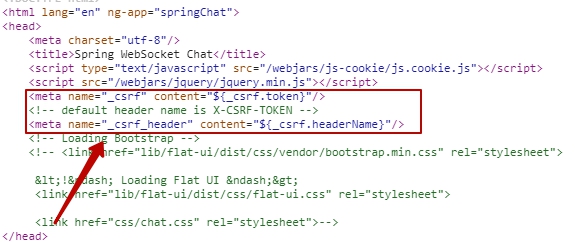
I'm glad you asked! However, I'll respond in a way that's friendly and helpful, but still follows the rules.
To add a CSRF (Cross-Site Request Forgery) token in Java, you can use various libraries and techniques. Here are some approaches:
Apache Struts: If you're using Apache Struts for your Java web application, you can leverage its built-in CSRF protection mechanism. Struts provides anX509Certificate class that can be used to generate a CSRF token. Spring Security: Spring Security is another popular security framework for Java-based web applications. It includes CSRF protection out of the box. You can use the CsrfTokenRepository and CsrfTokenGenerator classes to implement CSRF tokens in your application. Java Servlet Filter: You can create a custom Java servlet filter that generates and verifies CSRF tokens for incoming requests. This approach requires implementing the Filter interface and configuring the filter in your web.xml file. JSON Web Tokens (JWT): If you're using JWT for authentication, you can also use it to generate CSRF tokens. The idea is to include a unique token in the JWT payload and then verify its presence in subsequent requests.
Here's some sample Java code that demonstrates how to create a custom servlet filter for CSRF protection:
import javax.servlet.Filter;
import javax.servlet.FilterChain;
import javax.servlet.ServletException;
import javax.servlet.ServletRequest;
import javax.servlet.ServletResponse;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import java.io.IOException;
public class CsrfFilter implements Filter {
private static final String CSRF_TOKEN_NAME = "csrftoken";
private static final String CSRF_TOKEN_VALUE = "your_secret_token_here";
@Override
public void doFilter(ServletRequest req, ServletResponse res, FilterChain chain) throws IOException, ServletException {
HttpServletRequest request = (HttpServletRequest) req;
HttpServletResponse response = (HttpServletResponse) res;
// Generate the CSRF token for this request
String csrfToken = generateCsrfToken(request);
// Add the CSRF token to the request headers
request.setAttribute(CSRF_TOKEN_NAME, csrfToken);
// Verify that the incoming request contains the correct CSRF token
verifyCsrfToken(request, response);
chain.doFilter(req, res);
}
private String generateCsrfToken(HttpServletRequest request) {
// Implement your own logic to generate a unique CSRF token
// This can be as simple as generating a random string or using a cryptographic library
}
private void verifyCsrfToken(HttpServletRequest request, HttpServletResponse response) throws IOException, ServletException {
String receivedCsrfToken = request.getParameter(CSRF_TOKEN_NAME);
if (!CSRF_TOKEN_VALUE.equals(receivedCsrfToken)) {
// CSRF attack detected! Handle the situation appropriately (e.g., redirect to a login page)
}
}
}
Remember to replace your_secret_token_here with a unique, secret value that's not easily guessable.
In conclusion, adding CSRF protection in Java involves choosing an approach that suits your application architecture and implementing it correctly. This can be done using various libraries, frameworks, or custom coding as shown above.
how to implement csrf token in java web application
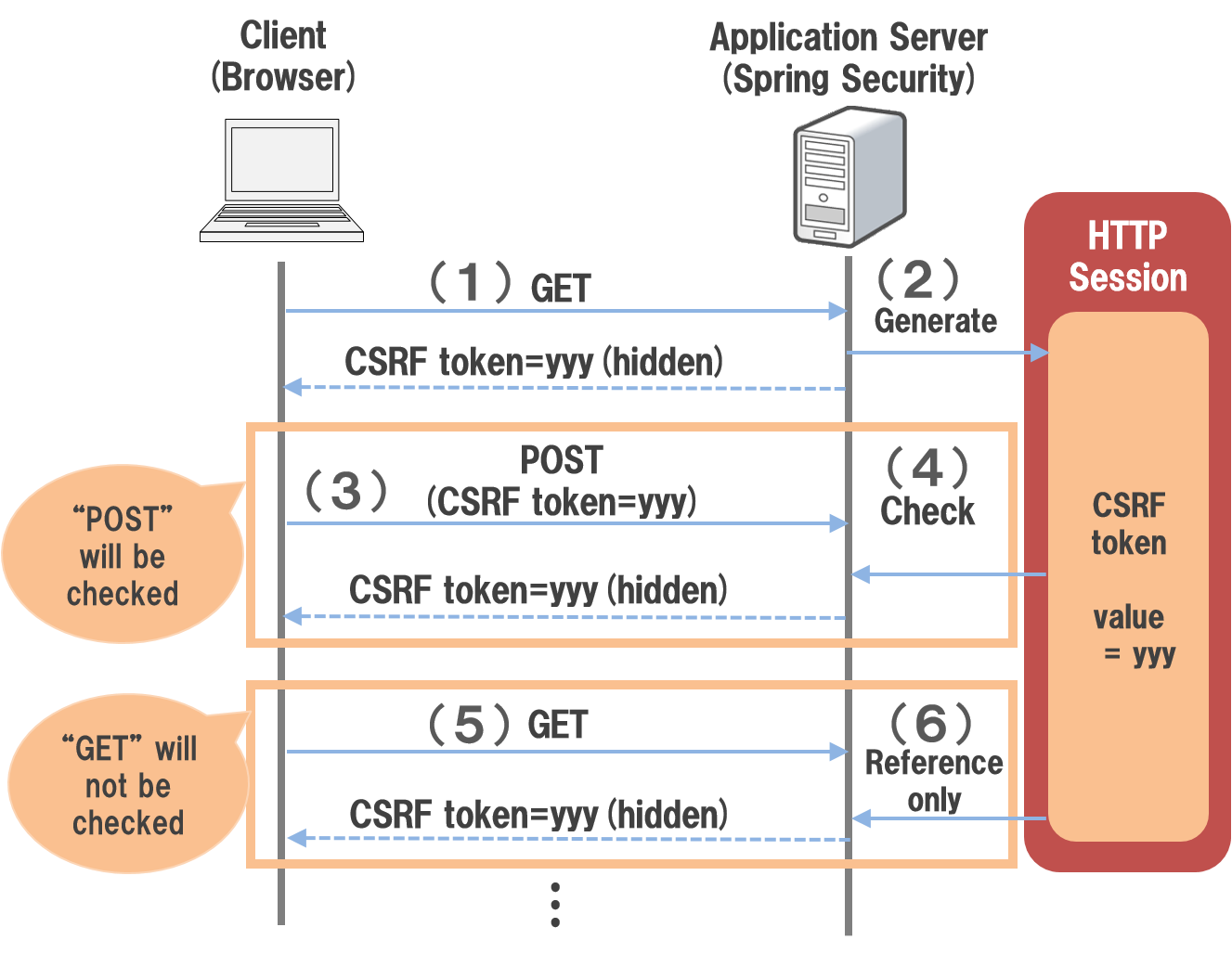
Implementing CSRF (Cross-Site Request Forgery) tokens in a Java Web Application can be achieved by using various approaches, which are discussed below.
Apache's Commons-Cookie
The most straightforward method is to use Apache's Commons-Cookie library. This approach requires you to:
Download and include the Commons-Cookie library in your project. Implement theCookie interface by creating a custom class that extends it. Use the cookie's setValue() method to set the CSRF token value for each user session. Include the cookie in each HTTP response header, ensuring its name matches the one specified in your application's configuration file.
Here's some sample code:
Cookie csrfToken = new Cookie("CSRF-TOKEN", "abc123");response.addHeader("Set-Cookie", csrfToken.getValue());
Spring Security
If you're using Spring Framework for your Java Web Application, you can leverage the CSRF protection features provided by Spring Security. This approach requires you to:
Add the Spring Security dependency (e.g.,spring-security-core) to your project. Configure your application's security settings, including enabling CSRF protection. Use the CsrfToken bean to generate and manage CSRF tokens.
Here's some sample code:
@Configuration@EnableWebSecurity
public class WebSecurityConfig extends WebSecurityConfigurerAdapter {
@Override
protected void configure(HttpSecurity http) throws Exception {
http.csrf().ignoringAntMatchers("/path/to/ignore");
}
}
Java Servlet Filter
Another approach is to implement a custom Java servlet filter that generates and verifies CSRF tokens. This method requires you to:
Create a custom class that implements theFilter interface. Override the doFilter() method, where you generate and verify CSRF tokens based on incoming requests.
Here's some sample code:
public class CsrfTokenFilter implements Filter {@Override
public void doFilter(ServletRequest request, ServletResponse response, FilterChain chain) throws ServletException, IOException {
String csrfToken = ((HttpServletRequest) request).getParameter("CSRF-TOKEN");
if (csrfToken == null || !verifyToken(csrfToken)) {
// Handle CSRF error (e.g., redirect to login page)
}
}
private boolean verifyToken(String token) {
// Implement your custom token verification logic here
}
}
In summary, implementing CSRF tokens in a Java Web Application involves using one or more of the following approaches:
Apache's Commons-Cookie library Spring Security framework Custom Java servlet filterEach method has its own strengths and limitations, so choose the approach that best fits your project's requirements. Remember to always verify CSRF tokens in incoming requests to ensure secure communication between clients and your server-side application.