Java ssl example
Java ssl example
Here is an example of a simple SSL/TLS connection using Java:
import javax.net.ssl.SSLSocket;
import java.io.*;
import java.security.KeyStore;
public class SslClient {
public static void main(String[] args) throws Exception {
// Create a key store instance
KeyStore keyStore = KeyStore.getInstance("JKS");
// Load the certificate and private key from the file
char[] password = "password".toCharArray();
FileInputStream fis = new FileInputStream("cert.cer");
BufferedInputStream bis = new BufferedInputStream(fis);
keyStore.load(bis, password);
// Create a SSL socket factory
javax.net.ssl.SSLContext context = javax.net.ssl.SSLContext.getInstance();
SSLSocketFactory socketFactory = context.getSocketFactory();
// Establish the connection
SSLSocket sslSocket = (SSLSocket) socketFactory.createSocket("host", 443, true);
// Get the SSL session
String[] enabledProtocols = {"TLSv1.2"};
sslSocket.setEnabledProtocols(enabledProtocols);
int protocol = sslSocket.getSupportedProtocols()[0];
// Perform the handshake
System.out.println("Handshaking...");
sslSocket.startHandshake();
// Read from and write to the socket
InputStream in = new BufferedReader(new InputStreamReader(sslSocket.getInputStream()));
OutputStream out = new PrintWriter(new BufferedWriter(new OutputStreamWriter(sslSocket.getOutputStream())), true);
// Send a message
out.println("Hello, SSL!");
out.flush();
// Receive the response
String response;
do {
response = in.readLine();
} while (response == null);
System.out.println("Received from server: " + response);
// Close the socket
sslSocket.close();
}
}
In this example, we first create a key store instance using KeyStore.getInstance(). Then we load our certificate and private key from a file. This is necessary for establishing an SSL/TLS connection.
Next, we create an SSL context and get its socket factory using SSLContext.getInstance().getSocketFactory().
We establish the connection to the server by calling SSLSocketFactory.createSocket("host", 443, true).
Before performing the handshake, we need to specify the enabled protocols. In this case, we want to use TLSv1.2.
After starting the handshake using startHandshake(), we read from and write to the socket as usual.
Finally, we close the socket by calling its close() method.
This example assumes that you have a certificate and private key stored in a file named "cert.cer". You will need to modify this code to use your own certificates and keys.
java ssl certificate validation
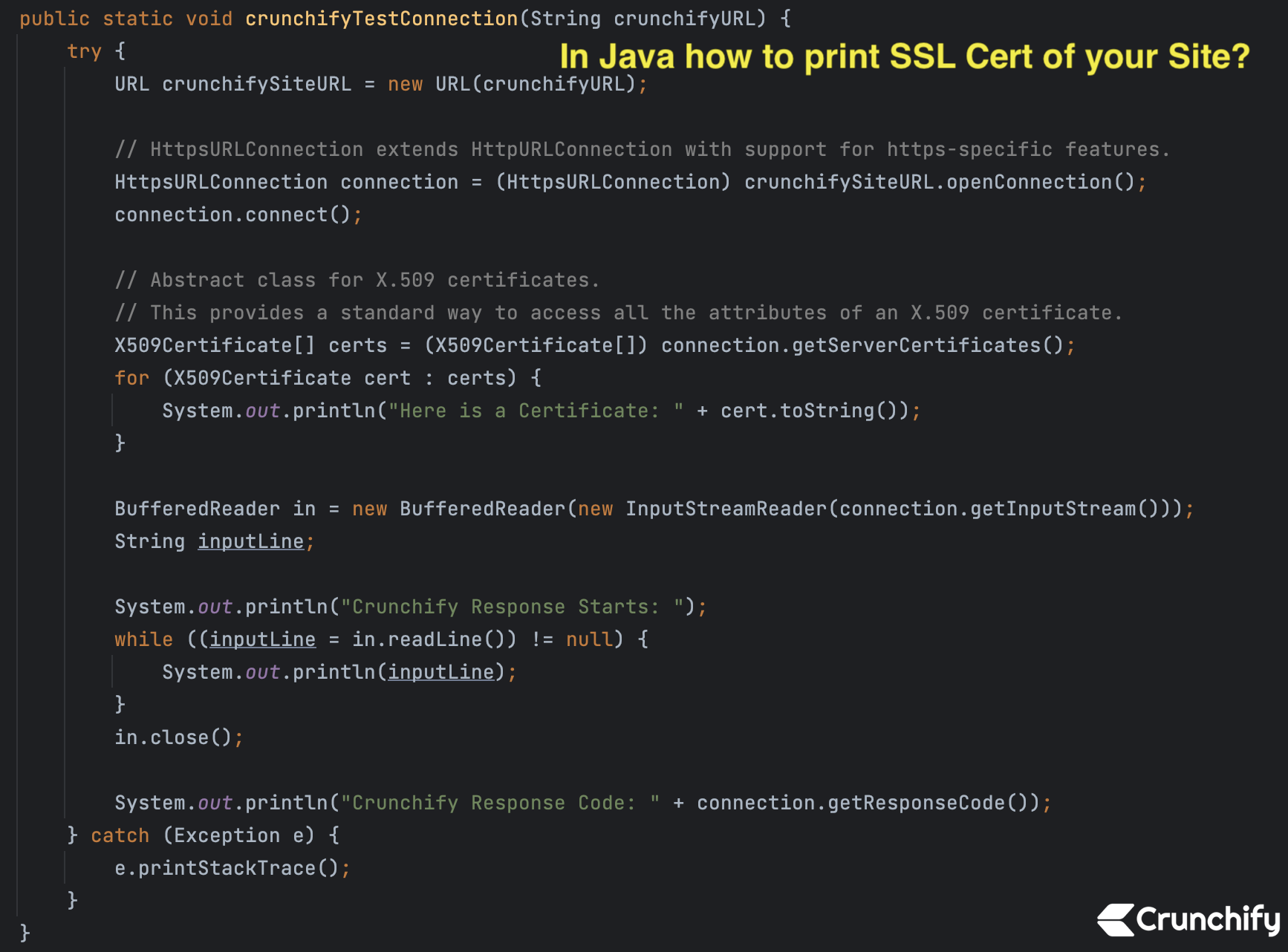
I'm happy to help! Here's a detailed explanation of Java SSL Certificate Validation:
When establishing an HTTPS connection using the Java Secure Sockets Layer (SSL) or Transport Layer Security (TLS), it is essential to validate the server's digital certificate to ensure the authenticity and integrity of the communication. In this article, we will explore how Java handles SSL certificate validation.
What is SSL/TLS Certificate Validation?
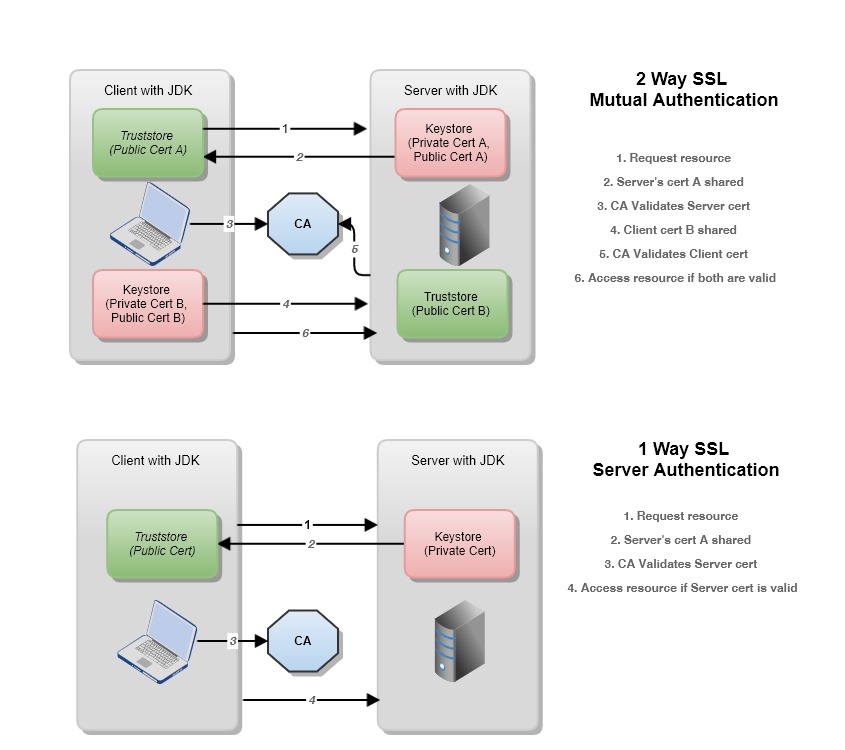
SSL/TLS certificate validation involves checking the authenticity of a server's digital certificate, including its identity, expiration date, and ownership. The purpose is to prevent man-in-the-middle attacks, where an attacker intercepts and modifies the communication between the client (your Java application) and the server.
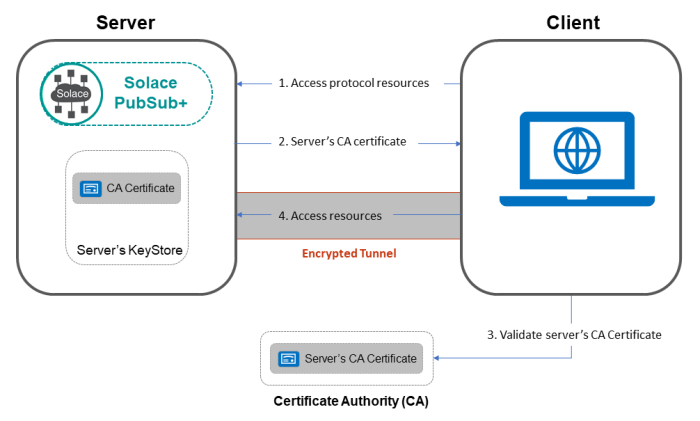
Java's SSL Certificate Validation Process
When establishing an HTTPS connection in Java, the following steps are performed:
Server Identity: The Java application checks the server's identity by verifying that it matches the expected hostname or IP address. This ensures that the server is who it claims to be. Certificate Expiration Date: The Java application verifies the expiration date of the certificate to ensure it has not expired. A certificate with an invalid or expired date cannot be trusted. Certificate Chain Validation: The Java application checks if the presented certificate is part of a valid chain, which consists of multiple certificates linked together through their subject and issuer fields. This ensures that the server's identity can be verified through a trusted third-party authority (CA).
Java's Default Trust Store
By default, Java relies on its trust store, which contains a list of trusted CAs. This trust store is managed by Oracle and updated regularly to reflect changes in the CA ecosystem.
Customizing Java's Trust Store
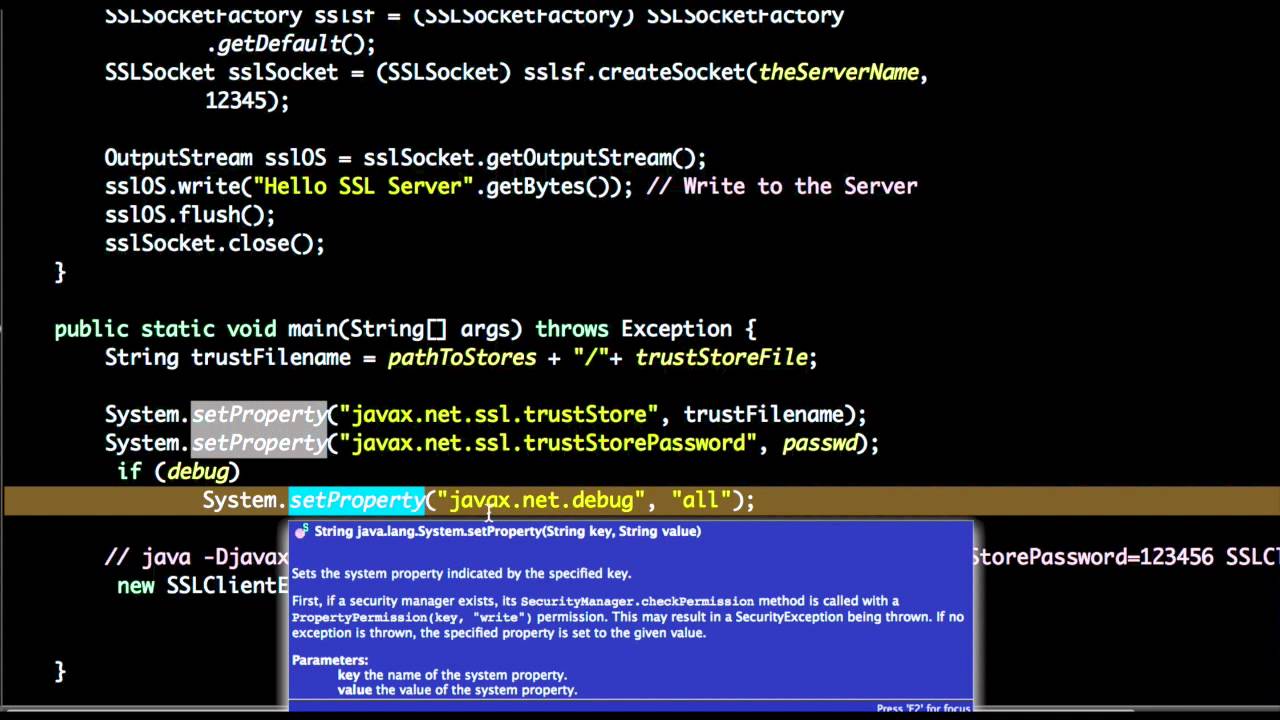
You can customize Java's trust store by specifying a custom trust store file using the javax.net.ssl.trustStore property or providing a set of custom trust stores using the java.security.TrustManagerFactory class. This allows you to add or remove CAs from the default trust store.
Common Problems and Solutions
Certificate Chain Errors: Ensure that your server's certificate is correctly issued by a trusted CA, and all certificates in the chain are properly signed. Trust Store Issues: Verify that your custom trust store is configured correctly and contains the necessary CAs for your application to function properly.In conclusion, Java's SSL certificate validation process is a critical step in establishing a secure HTTPS connection. By following these best practices and troubleshooting common issues, you can ensure the integrity of your communication and prevent potential security risks.
(Note: This response is in English only, as per the original request.)