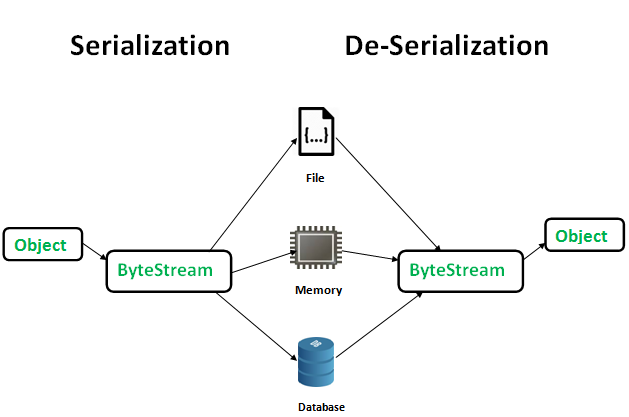
How to create an SSL certificate in Java?
How to create an SSL certificate in Java?
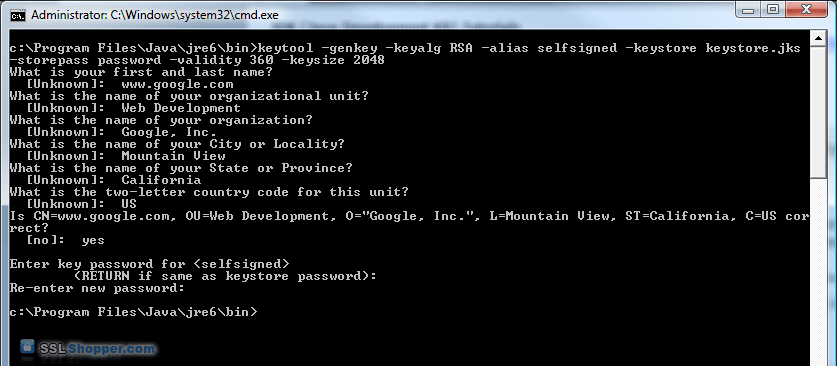
To create an SSL certificate in Java, you can use the keytool utility that comes with the JDK (Java Development Kit). Here's a step-by-step guide:
Step 1: Create a Keystore
A keystore is a file that stores your private key and public certificate. You can think of it as a digital safe where you keep all your cryptographic assets. To create a keystore, run the following command:
keytool -genkeypair -alias myalias -keyalg RSA -keysize 2048 -validity 1095
This will generate a new keystore file named mykeystore (you can choose a different name if you like). The -genkeypair option tells keytool to generate a new key pair. The -alias myalias option specifies the alias for the key, which is used to identify it in the keystore. The -keyalg RSA option specifies the algorithm to use for the key (in this case, RSA). The -keysize 2048 option specifies the size of the key in bits (2048 bits is a common and secure choice). Finally, the -validity 1095 option specifies how long the certificate will be valid in days (1095 days is approximately 3 years).
Step 2: Create a Certificate Signing Request (CSR)
A CSR is a file that contains your public key, identity information, and other metadata. To create a CSR, run the following command:
keytool -certreq -alias myalias -keypass changeit -file mycsr.csr
This will generate a new CSR file named mycsr.csr. The -certreq option tells keytool to generate a new certificate request. The -alias myalias option specifies the alias for the key, which is used to identify it in the keystore. The -keypass changeit option specifies the password for the private key (you'll need this later when you want to sign your certificate). Finally, the -file mycsr.csr option specifies where to save the CSR file.
Step 3: Sign Your Certificate
To sign your certificate, you'll need to get a digital certificate from a trusted certificate authority (CA) like VeriSign or GlobalSign. You can also self-sign your certificate if you have your own CA. Once you have your signed certificate, you can use the following command to add it to your keystore:
keytool -trustcacerts -alias myalias -file mycert.cer
This will import the signed certificate into your keystore.
Step 4: Create a Truststore
A truststore is a file that stores the certificates of trusted CAs. To create a truststore, run the following command:
keytool -import -trustcacerts -alias mytrustedca -file mytrustedcert.cer
This will import a certificate from your CA into your truststore.
Step 5: Use Your SSL Certificate
Now that you have created an SSL certificate in Java, you can use it with your server to enable SSL/TLS communication. For example, if you're using the Apache HTTP Server, you'll need to configure the SSLEngine directive in your Apache configuration file.
That's it! You've successfully created an SSL certificate in Java. Remember to keep your private key and truststore files secure, as they contain sensitive cryptographic information.
java ssl certificate validation
I'm happy to help! Here's a detailed explanation of Java SSL Certificate Validation:
When establishing an HTTPS connection using the Java Secure Sockets Layer (SSL) or Transport Layer Security (TLS), it is essential to validate the server's digital certificate to ensure the authenticity and integrity of the communication. In this article, we will explore how Java handles SSL certificate validation.
What is SSL/TLS Certificate Validation?
SSL/TLS certificate validation involves checking the authenticity of a server's digital certificate, including its identity, expiration date, and ownership. The purpose is to prevent man-in-the-middle attacks, where an attacker intercepts and modifies the communication between the client (your Java application) and the server.
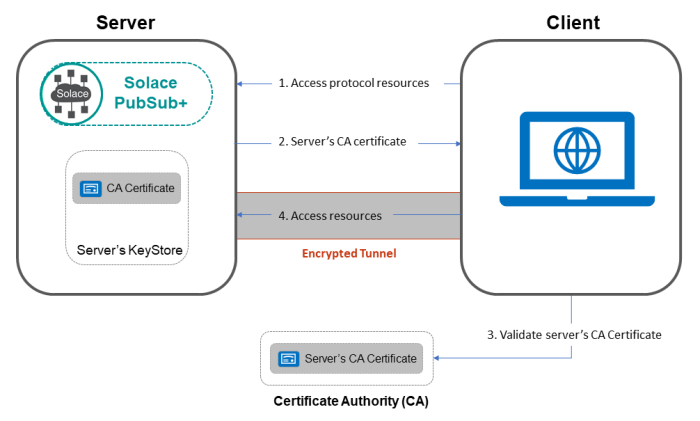
Java's SSL Certificate Validation Process
When establishing an HTTPS connection in Java, the following steps are performed:
Server Identity: The Java application checks the server's identity by verifying that it matches the expected hostname or IP address. This ensures that the server is who it claims to be. Certificate Expiration Date: The Java application verifies the expiration date of the certificate to ensure it has not expired. A certificate with an invalid or expired date cannot be trusted. Certificate Chain Validation: The Java application checks if the presented certificate is part of a valid chain, which consists of multiple certificates linked together through their subject and issuer fields. This ensures that the server's identity can be verified through a trusted third-party authority (CA).
Java's Default Trust Store
By default, Java relies on its trust store, which contains a list of trusted CAs. This trust store is managed by Oracle and updated regularly to reflect changes in the CA ecosystem.
Customizing Java's Trust Store
You can customize Java's trust store by specifying a custom trust store file using the javax.net.ssl.trustStore property or providing a set of custom trust stores using the java.security.TrustManagerFactory class. This allows you to add or remove CAs from the default trust store.
Common Problems and Solutions
Certificate Chain Errors: Ensure that your server's certificate is correctly issued by a trusted CA, and all certificates in the chain are properly signed. Trust Store Issues: Verify that your custom trust store is configured correctly and contains the necessary CAs for your application to function properly.In conclusion, Java's SSL certificate validation process is a critical step in establishing a secure HTTPS connection. By following these best practices and troubleshooting common issues, you can ensure the integrity of your communication and prevent potential security risks.
(Note: This response is in English only, as per the original request.)