Java ssl example
Java ssl example
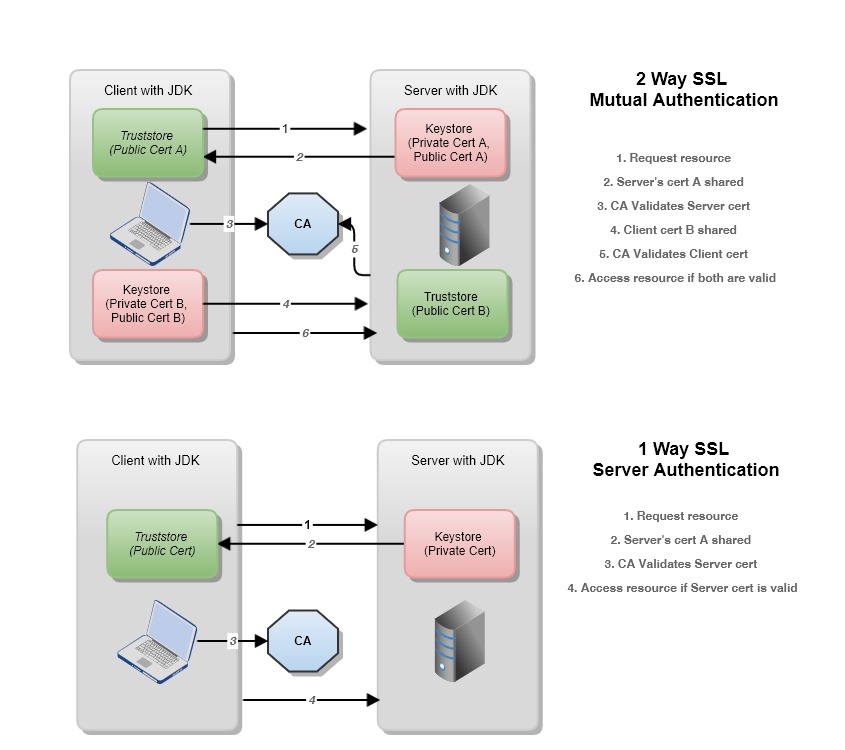
Here is an example of a simple SSL/TLS connection using Java:
import javax.net.ssl.SSLSocket;
import java.io.*;
import java.security.KeyStore;
public class SslClient {
public static void main(String[] args) throws Exception {
// Create a key store instance
KeyStore keyStore = KeyStore.getInstance("JKS");
// Load the certificate and private key from the file
char[] password = "password".toCharArray();
FileInputStream fis = new FileInputStream("cert.cer");
BufferedInputStream bis = new BufferedInputStream(fis);
keyStore.load(bis, password);
// Create a SSL socket factory
javax.net.ssl.SSLContext context = javax.net.ssl.SSLContext.getInstance();
SSLSocketFactory socketFactory = context.getSocketFactory();
// Establish the connection
SSLSocket sslSocket = (SSLSocket) socketFactory.createSocket("host", 443, true);
// Get the SSL session
String[] enabledProtocols = {"TLSv1.2"};
sslSocket.setEnabledProtocols(enabledProtocols);
int protocol = sslSocket.getSupportedProtocols()[0];
// Perform the handshake
System.out.println("Handshaking...");
sslSocket.startHandshake();
// Read from and write to the socket
InputStream in = new BufferedReader(new InputStreamReader(sslSocket.getInputStream()));
OutputStream out = new PrintWriter(new BufferedWriter(new OutputStreamWriter(sslSocket.getOutputStream())), true);
// Send a message
out.println("Hello, SSL!");
out.flush();
// Receive the response
String response;
do {
response = in.readLine();
} while (response == null);
System.out.println("Received from server: " + response);
// Close the socket
sslSocket.close();
}
}
In this example, we first create a key store instance using KeyStore.getInstance(). Then we load our certificate and private key from a file. This is necessary for establishing an SSL/TLS connection.
Next, we create an SSL context and get its socket factory using SSLContext.getInstance().getSocketFactory().
We establish the connection to the server by calling SSLSocketFactory.createSocket("host", 443, true).
Before performing the handshake, we need to specify the enabled protocols. In this case, we want to use TLSv1.2.
After starting the handshake using startHandshake(), we read from and write to the socket as usual.
Finally, we close the socket by calling its close() method.
This example assumes that you have a certificate and private key stored in a file named "cert.cer". You will need to modify this code to use your own certificates and keys.
java ssl debug
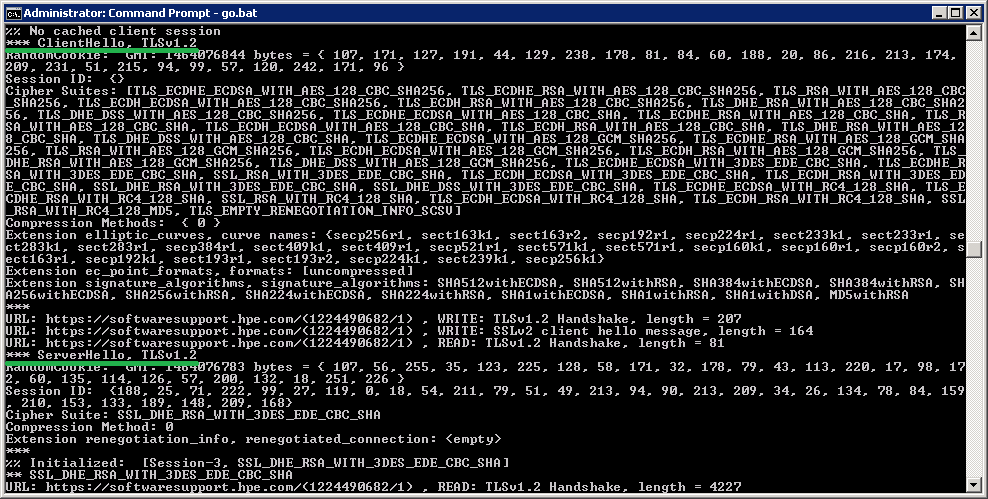
Java SSL Debugging!
When it comes to debugging SSL/TLS issues in a Java application, there are several approaches and tools that can help you identify the problem. Here are some steps to follow:
Step 1: Enable SSL Debug Logging
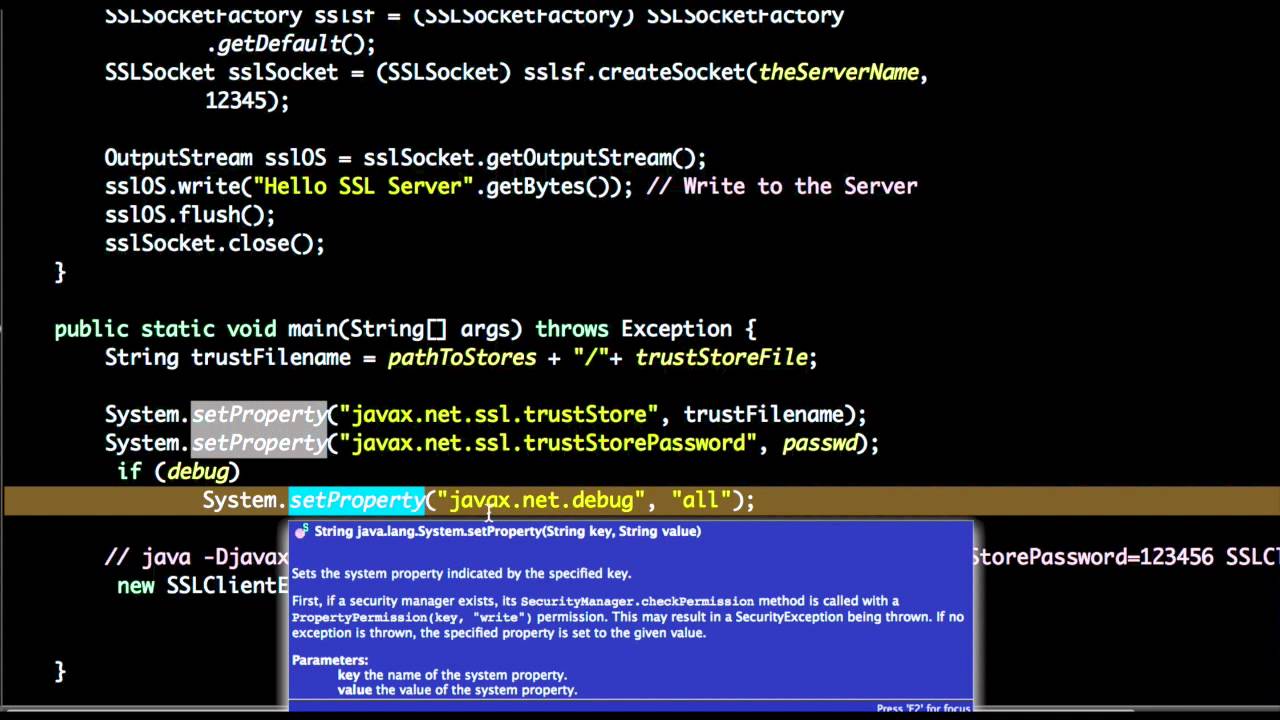
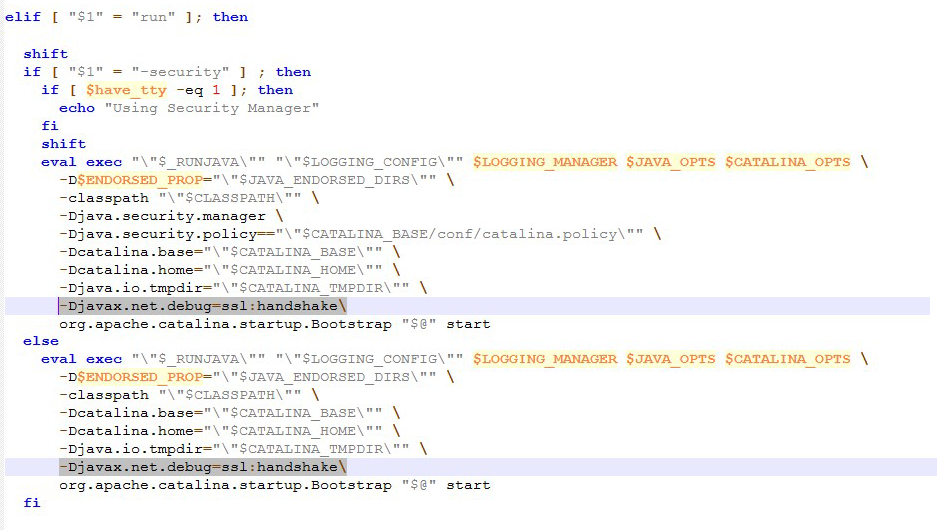
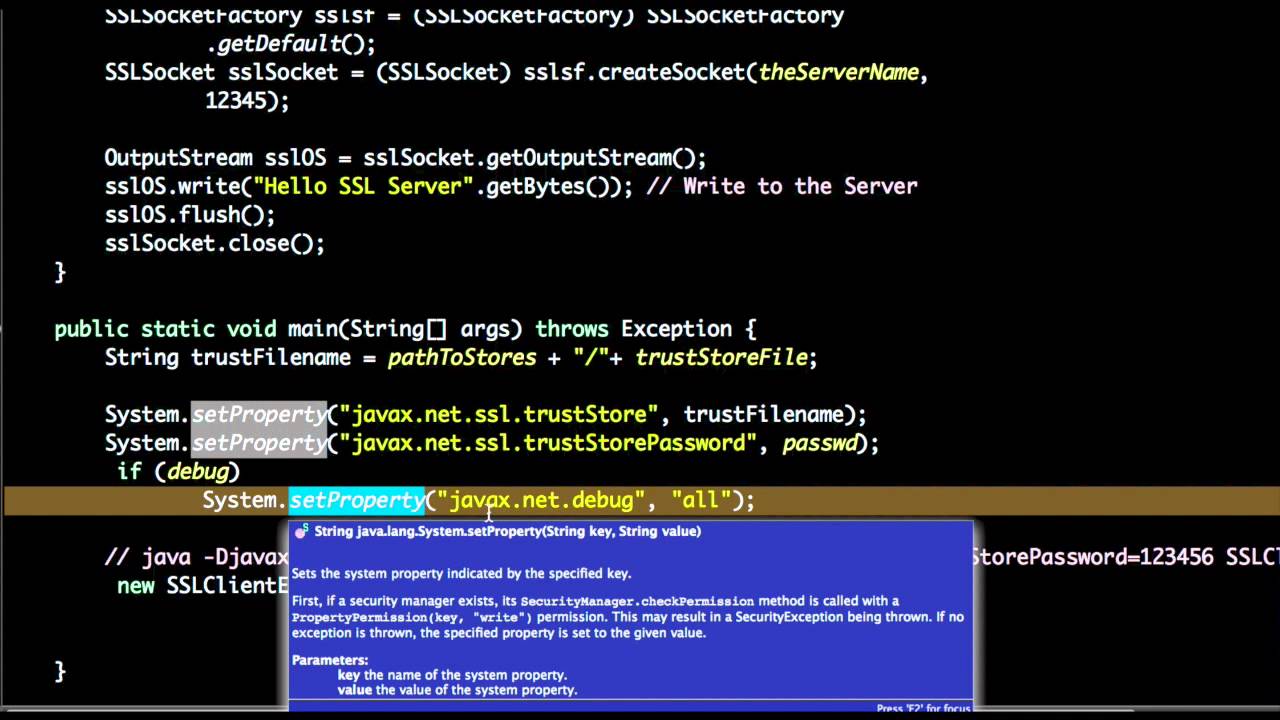
To start with, you'll need to enable debug logging for SSL/TLS in your Java application. You can do this by setting the following system property:
-Djavax.net.debug=ssl
This will enable detailed SSL/TLS debugging output. You can also specify specific log levels, such as ssl:dump or ssl:handshake, to get more fine-grained information.
Step 2: Use the OpenSSL Command-Line Tool
Another useful tool for debugging SSL/TLS issues is OpenSSL. You can use OpenSSL's built-in debug commands to inspect the certificate and key files used by your Java application.
openssl s_client -connect : -showcerts
Replace <host> and <port> with the host name and port number of your SSL/TLS server.
Step 3: Inspect SSL/TLS Handshake Data
To inspect the SSL/TLS handshake data, you can use a tool like sslscan or ssllabs. These tools can help you identify any issues with certificate validation, key usage, or other handshake-related problems.
sslscan :
Replace <host> and <port> with the host name and port number of your SSL/TLS server.
Step 4: Review Java SSL/TLS API Debug Output
When you run your Java application with SSL debug logging enabled, you can review the output to identify any issues related to certificate validation, key usage, or other SSL/TLS-related problems. Look for error messages or warnings that might indicate a problem.
-Djavax.net.debug=ssl
This will give you detailed information about the SSL/TLS handshake process, including any errors or warnings.
Step 5: Use Third-Party Debugging Tools
There are several third-party debugging tools available that can help you diagnose SSL/TLS issues in your Java application. Some popular options include:
Wireshark: A network protocol analyzer that can capture and inspect SSL/TLS packets. Fiddler: A web debugging proxy that can capture and manipulate SSL/TLS traffic. Burp Suite: An integrated suite of tools for security testing, including SSL/TLS analysis.Conclusion
Debugging SSL/TLS issues in a Java application requires a combination of logging, inspection, and analysis. By following these steps, you should be able to identify and resolve most SSL/TLS-related problems. Remember to always enable debug logging and inspect the SSL/TLS handshake data carefully to pinpoint the issue!