Java transient
Java transient
I'm happy to respond in English!
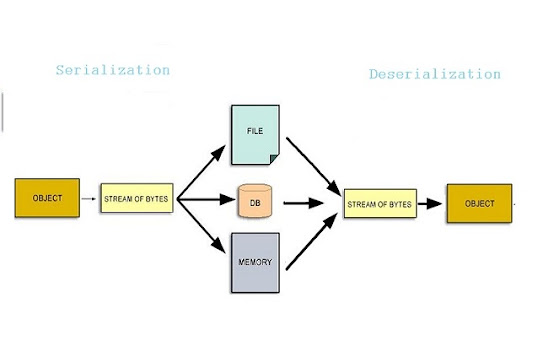
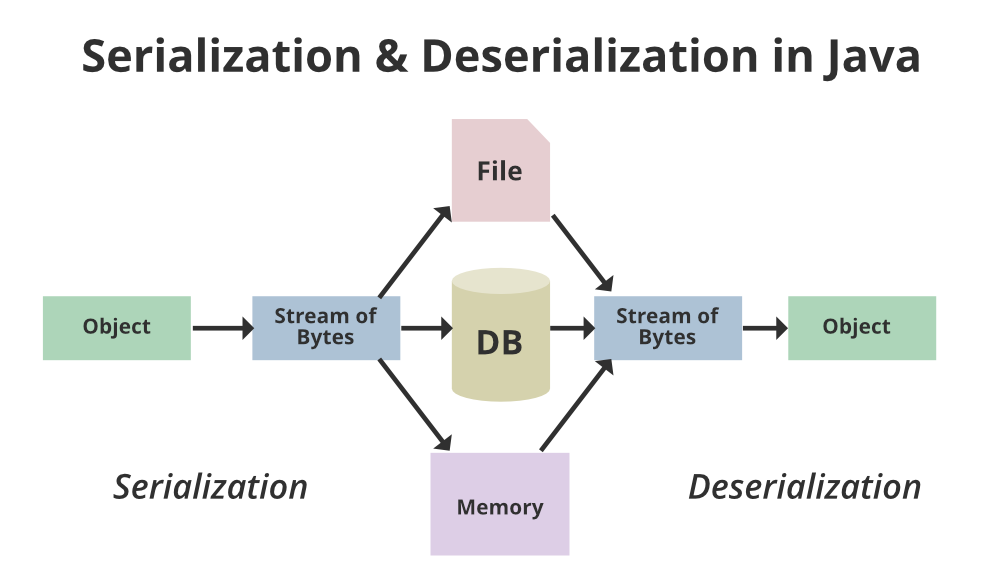
The transient keyword in Java is a reserved word that can be used to indicate that a variable should not be serialized (or written out) when an object of its class is saved or marshaled.
By default, when you serialize an object in Java using the built-in ObjectOutputStream, all its fields are serialized along with it. This means that if your object has some sensitive information, such as passwords or credit card numbers, they will be written to a file or database and potentially compromised if the file is accessed by someone else.
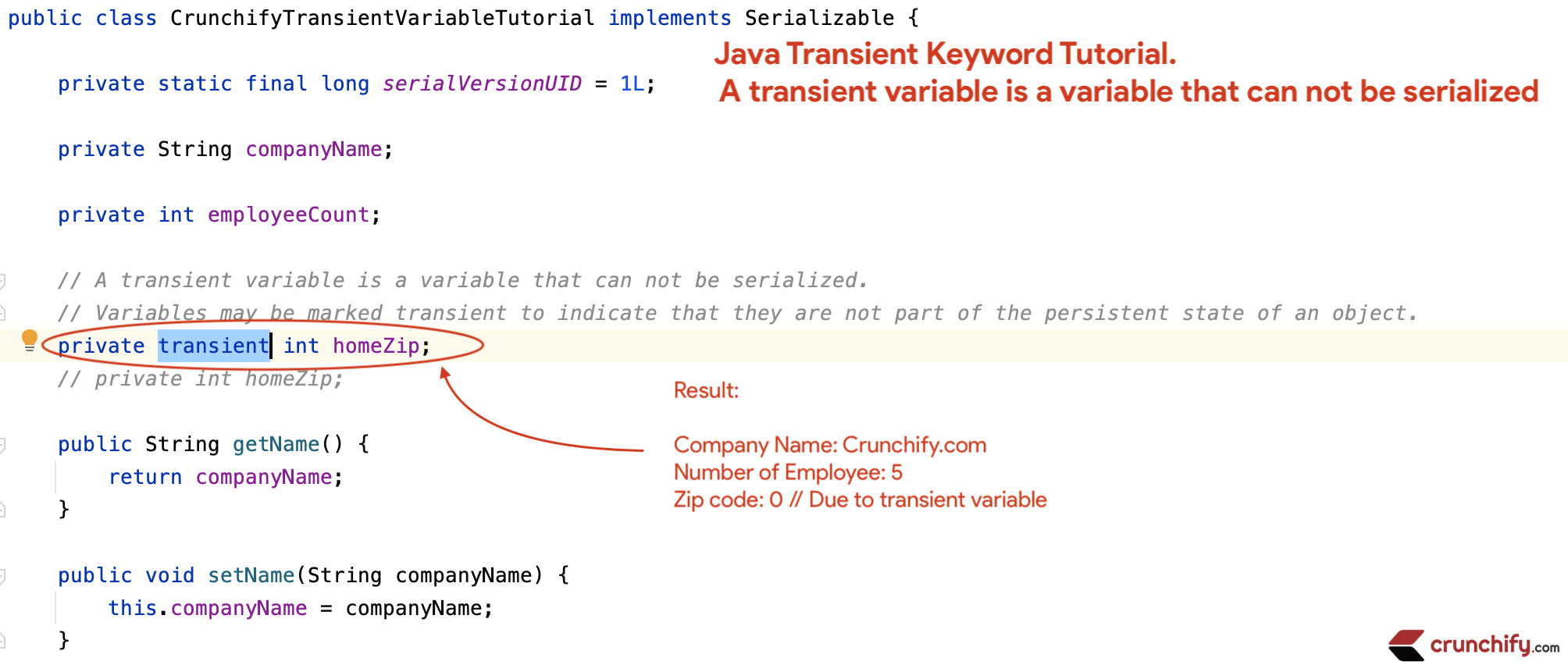
Using the transient keyword, you can mark specific variables in your class so that they are not serialized when the object is saved. This is particularly useful when working with sensitive data, as it helps prevent accidental exposure of private information.
Here's an example:
public class User {
public String name;
public transient String password; // marked as transient
public void save() {
try (ObjectOutputStream oos = new ObjectOutputStream(new FileOutputStream("user.ser"))) {
oos.writeObject(this);
} catch (IOException e) {
e.printStackTrace();
}
}
public static void main(String[] args) throws IOException {
User user = new User();
user.name = "John Doe";
user.password = "password123";
user.save();
try (ObjectInputStream ois = new ObjectInputStream(new FileInputStream("user.ser"))) {
User deserializedUser = (User) ois.readObject();
// Note that the password is not available after deserialization
System.out.println(deserializedUser.name); // prints "John Doe"
// System.out.println(deserializedUser.password); // throws ClassCastException
}
}
}
In this example, when we serialize the User object, its password field is not written to the file. When we deserialize the object later on, the password field is still available (although it was never actually serialized), but attempting to access it will throw a ClassCastException, indicating that the field is no longer part of the serialized data.
By using the transient keyword, you can effectively "hide" specific variables from being serialized and ensure they remain private even when your objects are saved or shared.
How do you make a field not Serializable in Java?
I'd be happy to help!
To prevent a Java class from being serialized (i.e., its state is not serialized and written out to the serialization stream), you can implement the writeObject and/or readObject methods in your class, and throw an exception if they're called.
Here's how you do it:
Let's say you have a simple Java class NonSerializableField, which has a non-serializable field unSerializableField:
public class NonSerializableField {
private String unSerializableField;
public NonSerializableField(String unSerializableField) {
this.unSerializableField = unSerializableField;
}
}
In order to prevent the NonSerializableField from being serialized, you can override the writeObject and/or readObject methods in the NonSerializableField class. When these methods are called during serialization or deserialization, they throw a NotSerializableException.
Here's how you do it:
import java.io.IOException;
import java.io.ObjectOutputStream;
public class NonSerializableField implements Serializable {
private String unSerializableField;
public NonSerializableField(String unSerializableField) {
this.unSerializableField = unSerializableField;
}
private void writeObject(ObjectOutputStream os)
throws IOException {
throw new NotSerializableException("NonSerializableField is not serializable.");
}
private void readObject(ObjectInputStream ois)
throws IOException, ClassNotFoundException {
throw new NotSerializableException("NonSerializableField is not serializable.");
}
}
By overriding these methods and throwing a NotSerializableException, you effectively prevent the NonSerializableField from being serialized. This will ensure that any attempts to serialize or deserialize an instance of NonSerializableField will result in a runtime exception.
Note: When you override readObject, make sure you also implement the necessary logic for reconstructing the object's state, if applicable.
This approach can be useful when dealing with legacy systems that require non-serializable data. For example, imagine you have a Java system where certain data structures should not be serialized due to security or performance concerns.
Remember, when overriding writeObject and/or readObject, it is essential to throw an exception (like NotSerializableException) if the object's state cannot be serialized or deserialized. This ensures that any attempts to serialize or deserialize the object will result in a runtime error, thereby preventing unintended behavior.