How to implement cryptography in java?
How to implement cryptography in java?
I'd be happy to provide an answer in English!
Implementing cryptography in Java involves using the Java Cryptography Architecture (JCA), which provides a set of APIs for encryption, decryption, and other cryptographic operations. Here's a step-by-step guide on how to implement cryptography in Java:
Import Required Packages: Start by importing the necessary packages. For example:import javax.crypto.*;
import java.security.*;
// Generate an RSA key pair
KeyPairGenerator kpg = KeyPairGenerator.getInstance("RSA");
kpg.initialize(2048);
KeyPair kp = kpg.generateKeyPair();
PrivateKey privateKey = kp.getPrivate();
PublicKey publicKey = kp.getPublic();
// Encrypt a message using AES encryption
String message = "Hello, World!";
byte[] messageBytes = message.getBytes("UTF-8");
SecretKeySpec skeySpec = new SecretKeySpec(key, "AES");
Cipher cipher = Cipher.getInstance("AES");
cipher.init(Cipher.ENCRYPT_MODE, skeySpec);
byte[] encryptedMessage = cipher.doFinal(messageBytes);
// Decrypt an encrypted message using AES decryption
byte[] encryptedMessage = ...; // retrieve the encrypted message
SecretKeySpec skeySpec = new SecretKeySpec(key, "AES");
Cipher cipher = Cipher.getInstance("AES");
cipher.init(Cipher.DECRYPT_MODE, skeySpec);
byte[] decryptedMessage = cipher.doFinal(encryptedMessage);
String decryptedText = new String(decryptedMessage, "UTF-8");
Here's a sample code for implementing AES encryption in Java:
import javax.crypto.*;
import java.security.*;
public class AesEncryption {
public static void main(String[] args) throws Exception {
// Generate an AES key
KeyGenerator kgen = KeyGenerator.getInstance("AES");
kgen.init(128); // 128-bit key
SecretKey key = kgen.generateKey();
byte[] keyValue = key.getEncoded();
// Encrypt a message using AES encryption
String message = "Hello, World!";
byte[] messageBytes = message.getBytes("UTF-8");
Cipher cipher = Cipher.getInstance("AES");
cipher.init(Cipher.ENCRYPT_MODE, new SecretKeySpec(keyValue, "AES"));
byte[] encryptedMessage = cipher.doFinal(messageBytes);
// Decrypt the encrypted message using AES decryption
Cipher dcipher = Cipher.getInstance("AES");
dcipher.init(Cipher.DECRYPT_MODE, new SecretKeySpec(keyValue, "AES"));
byte[] decryptedMessage = dcipher.doFinal(encryptedMessage);
System.out.println(new String(decryptedMessage, "UTF-8"));
}
}
Remember to handle key management securely and use trusted libraries or APIs for cryptographic operations.
What is the best encryption algorithm in java?
I'd be happy to help you with that!
Choosing the "best" encryption algorithm in Java (or anywhere else, for that matter) largely depends on various factors such as the type of data being encrypted, security requirements, performance constraints, and personal preferences.
Java has an impressive array of built-in cryptographic libraries, including the Java Cryptography Architecture (JCA) and the OpenJDK Cryptographic API. Let's focus on some popular and widely used encryption algorithms in Java:
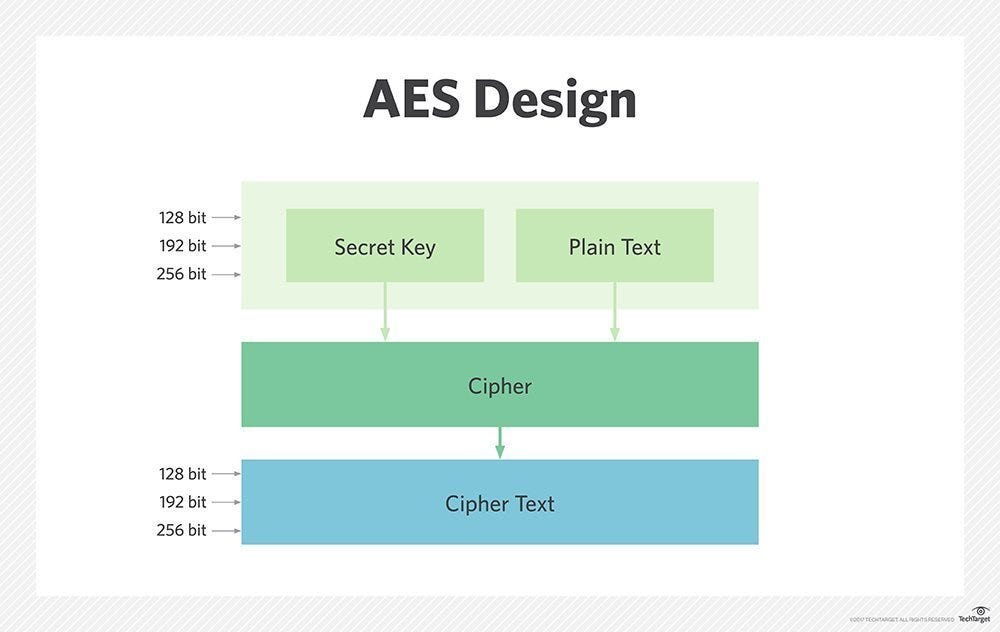
AES (Advanced Encryption Standard): AES is a widely used symmetric-key block cipher that excels at encrypting large amounts of data quickly. It has a 128-bit key size, which makes it suitable for securing sensitive data. In Java, you can use thejavax.crypto.Cipher class to implement AES encryption.
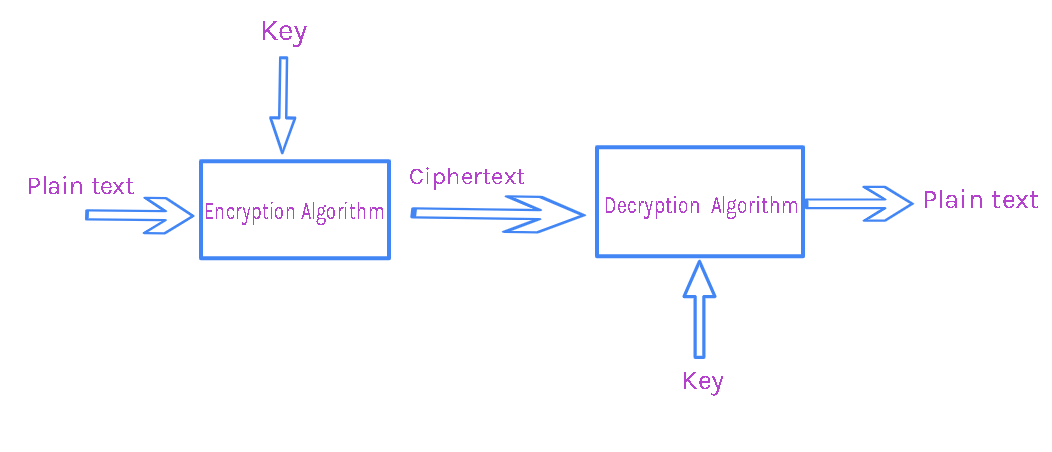
java.security.KeyPairGenerator and javax.crypto.Cipher classes to implement RSA encryption. Blowfish: Blowfish is another symmetric-key block cipher that shares some similarities with AES but has a slightly different encryption process. It's generally considered less secure than AES but still suitable for encrypting sensitive data in certain scenarios. In Java, you can use the javax.crypto.Cipher class to implement Blowfish encryption. SHA (Secure Hash Algorithm): SHA is a family of cryptographic hash functions that generate fixed-size digests from arbitrary-sized messages. It's often used as a digital signature or message authentication code (MAC). In Java, you can use the java.security.MessageDigest class to implement SHA-based signatures and MACs.
When selecting an encryption algorithm in Java, consider factors like:
Key size: Larger key sizes generally provide better security, but at the cost of slower encryption processes. Block size: Symmetric ciphers (like AES) typically have larger block sizes than asymmetric ciphers (like RSA). Computational complexity: Asymmetric algorithms usually require more computational power to encrypt and decrypt data.
Here are some general guidelines for choosing the "best" encryption algorithm in Java:
For symmetric-key block ciphers, AES (with a 128-bit key size) is usually a safe bet. For asymmetric-key algorithms, RSA (with a 2048-bit modulus) might be suitable for securing small amounts of data. When you need to generate digital signatures or MACs, SHA-based algorithms like SHA-256 are popular choices.Remember that the choice of encryption algorithm ultimately depends on your specific use case and security requirements. Always consider factors like key management, computational complexity, and performance constraints when selecting an encryption algorithm in Java!