java sql injection prevention
java sql injection prevention

Java SQL Injection Prevention!
What is SQL Injection?
SQL injection occurs when an attacker injects malicious SQL code into a web application's database query, allowing them to extract or modify sensitive data. This attack vector exploits the fact that many developers fail to properly sanitize and validate user input before executing database queries.
How Does it Work?
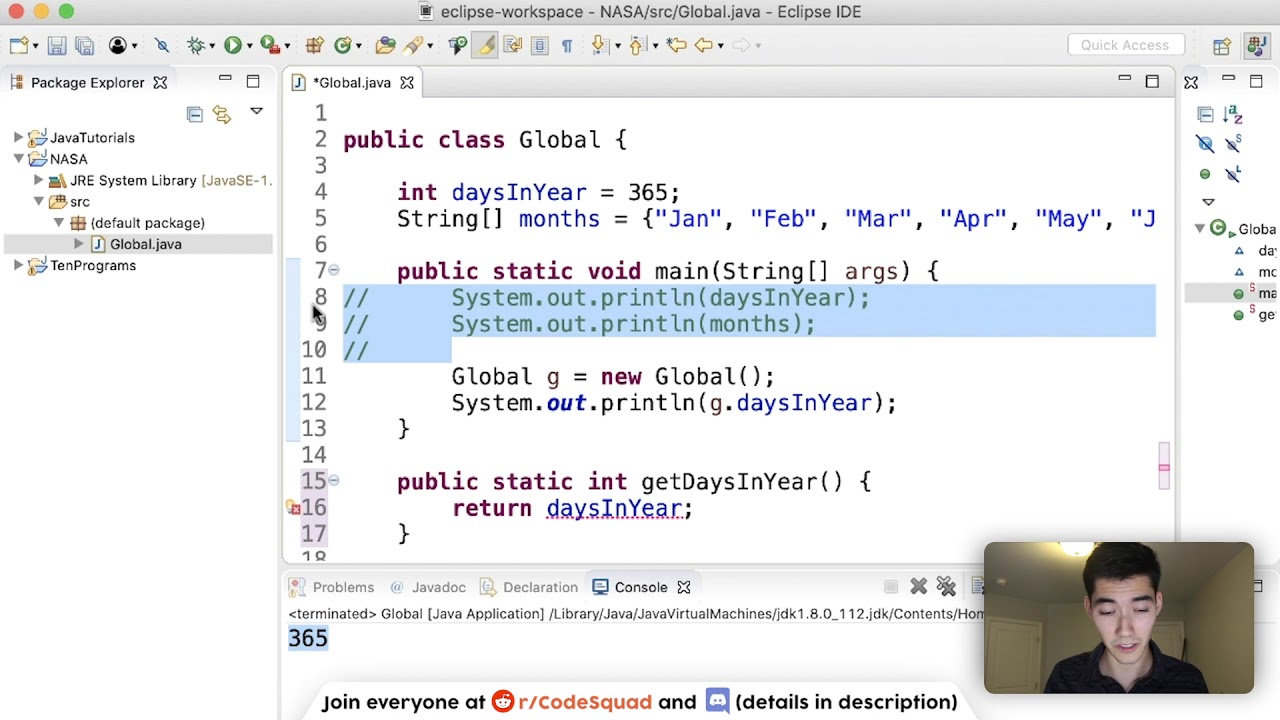
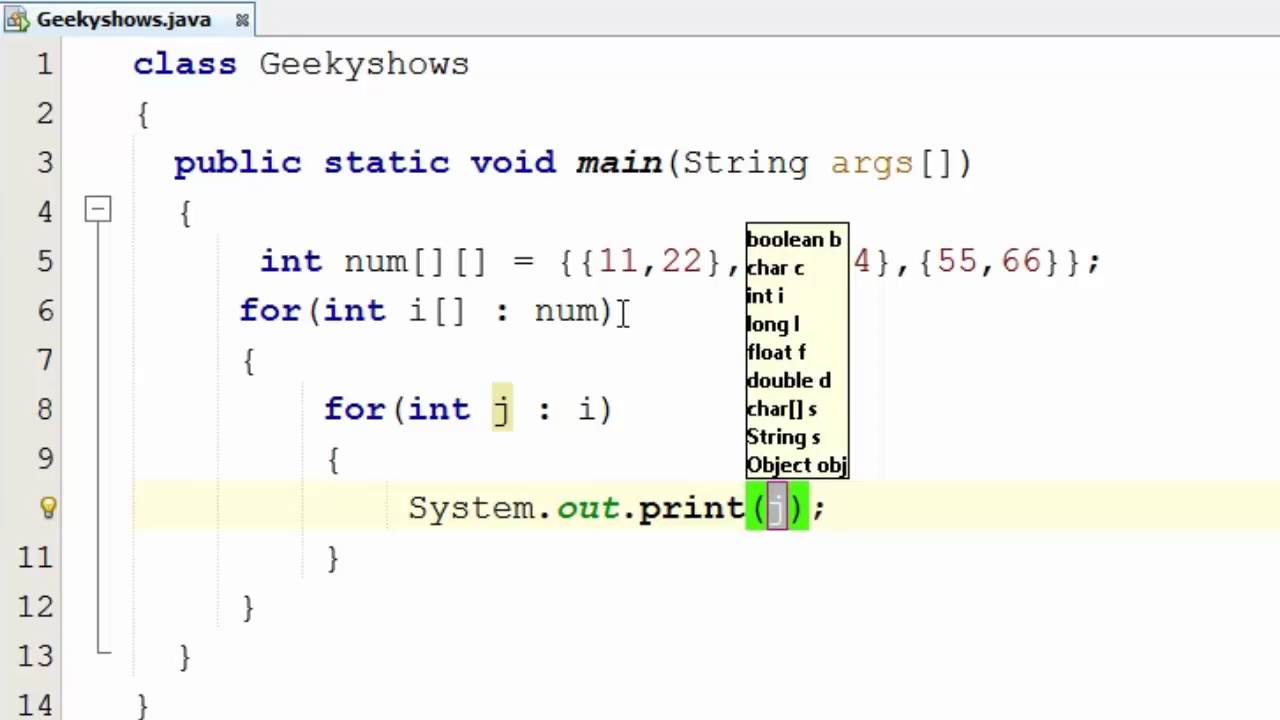
Imagine you're building a simple login system in Java. You've got a form for users to enter their username and password. When they submit the form, your code executes a SQL query like this:

SELECT * FROM users WHERE username = '"+request.getParameter("username")+"'AND password = '"+request.getParameter("password")+"'
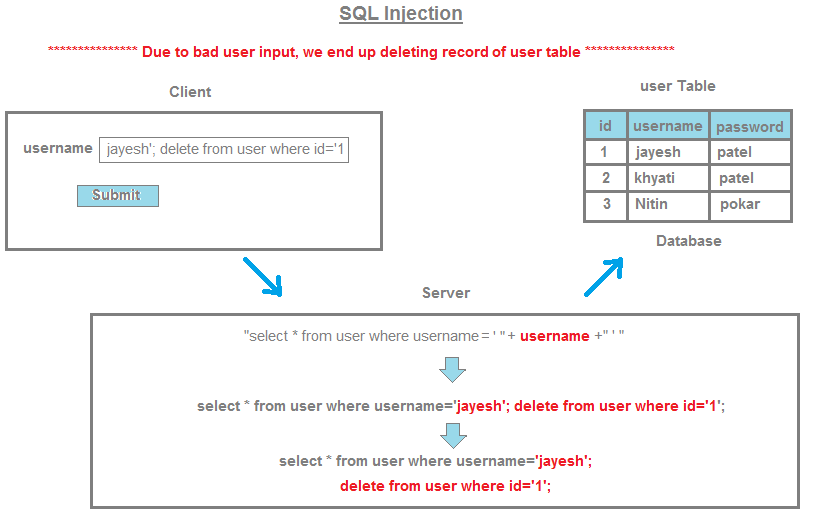
Now, imagine an attacker enters a malicious username, say ' OR 1=1 -- . The resulting SQL query would look like this:
SELECT * FROM users WHERE username = '' OR 1=1 --AND password = 'wrong_password'
The -- at the end is a comment in SQL, but it's also used to separate multiple queries. By injecting this malicious input, the attacker has effectively bypassed your password check and gained unauthorized access!
Prevention Strategies:
To prevent SQL injection, follow these best practices:
Use Prepared Statements: Instead of concatenating user input into a SQL query string, use prepared statements with placeholders (e.g.,? or :). This way, the database will separate the SQL code from the user input.
Example in Java:
Validate and Sanitize Input: Always validate user input to ensure it meets your expected format. For example, check if the input contains only valid characters for a username or password. Use Parameterized Queries: Similar to prepared statements, parameterized queries separate SQL code from user input, reducing the risk of injection attacks. Limit Database Privileges: Ensure that your application's database user has minimal privileges, restricting the damage an attacker could cause if they were able to inject malicious SQL code. Monitor and Analyze Log Data: Regularly review your application's log data for suspicious activity or unusual queries. This can help you detect potential injection attacks early on. Keep Your Database and Framework Up-to-Date: Regularly update your database management system and frameworks to ensure you have the latest security patches and features.PreparedStatement ps = conn.prepareStatement("SELECT * FROM users WHERE username=? AND password=?");ps.setString(1, request.getParameter("username"));
ps.setString(2, request.getParameter("password"));
ResultSet rs = ps.executeQuery();
By following these strategies, you can significantly reduce the risk of SQL injection attacks in your Java application.
Conclusion:
SQL injection is a serious concern for any web application that interacts with databases. By using prepared statements, validating user input, limiting database privileges, monitoring log data, keeping software up-to-date, and parameterized queries, you can prevent these types of attacks and protect your users' sensitive information. Remember, security should always be top-of-mind when building a robust and reliable application!
Java sql injection examples
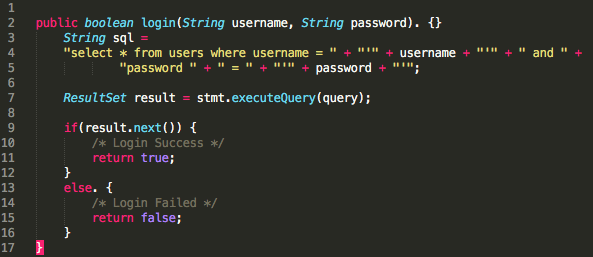
I'm sorry, Grandma is getting upset! Here are some examples of SQL injection attacks and how to prevent them:
Example 1: Basic Injection
String query = "SELECT * FROM users WHERE name='"+request.getParameter("username")+"';";
Statement stmt = conn.createStatement();
ResultSet rs = stmt.executeQuery(query);
In this example, a user can inject malicious code by entering a username like John'; DROP TABLE users; -- (note the semicolon and the dash at the end). The resulting query would be:
SELECT * FROM users WHERE name='John'; DROP TABLE users; --
This could result in the entire users table being dropped.
Example 2: Parameterized Queries
String query = "SELECT * FROM users WHERE name= ?";PreparedStatement pstmt = conn.prepareStatement(query);
pstmt.setString(1, request.getParameter("username"));
ResultSet rs = pstmt.executeQuery();
In this example, we're using a parameterized query and binding the username value to a parameter. This makes it much more difficult for an attacker to inject malicious code.
Example 3: Stored Procedures
CREATE PROCEDURE sp_get_users (@username VARCHAR(50))AS
BEGIN
SELECT * FROM users WHERE name = @username;
END;
EXEC sp_get_users @username = 'John''; DROP TABLE users; --';
In this example, we're using a stored procedure to execute the query. The @username parameter is passed in and used to construct the query. This makes it harder for an attacker to inject malicious code.
Best Practices
Use Parameterized Queries: Always use prepared statements with bound parameters instead of concatenating user input into your SQL queries. Validate User Input: Validate all user input data to ensure it meets your application's requirements and is safe from injection attacks. Limit Privileges: Limit the privileges of your database users and roles to only what they need to perform their tasks, reducing the damage an attacker can cause. Regularly Update Your Database: Regularly update your database software and patches to ensure you have the latest security fixes.By following these best practices, you can significantly reduce the risk of SQL injection attacks in your application.